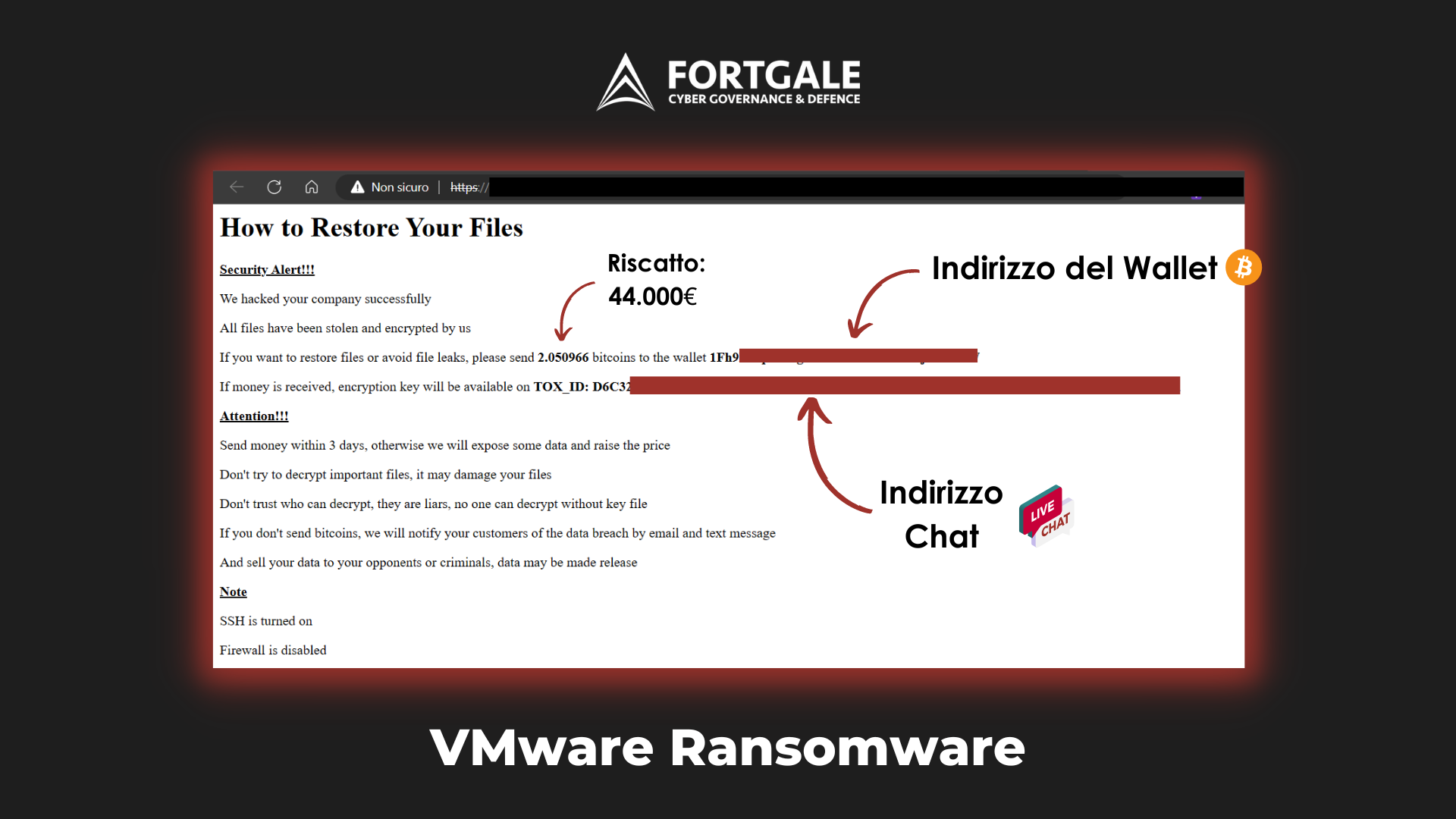
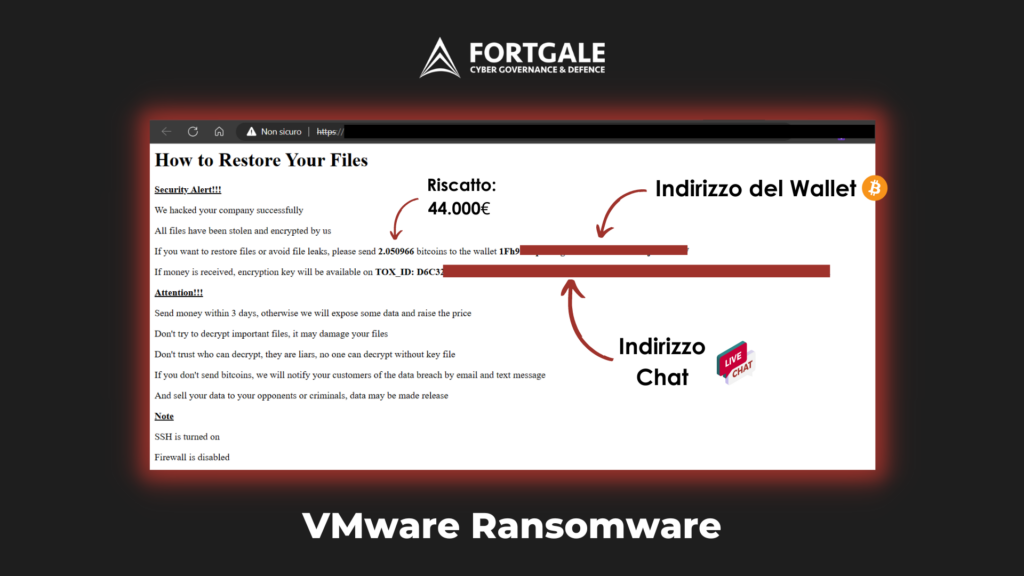
VMware ESXi #Ransomware: What is going on? What does the following code means?
D6C324719AD0AA50A54E4F8DED8E8220D8698DD67B218B5429466C40E7F72657C015D86C7E4A
In the last few hours, several sources have reported massive Ransomware-type activity against VMware ESXi servers exposed on a public network.
The activity currently appears to be conducted by at least 2 different criminal groups.
How?
Both groups are exploiting a 2021 RCE vulnerability that allows malicious code (𝗥𝗮𝗻𝘀𝗼𝗺𝘄𝗮𝗿𝗲) to be launched remotely (CVE-𝟮𝟬𝟮𝟭-𝟮𝟭𝟵𝟳𝟰 )
Current situation (4th of February)
There is currently massive hacking activity happening globally. Most of the compromised systems (around 500) were found to be in France.
The first server compromises emerge in Italy and Switzerland.
Italy and Switzerland
From an analysis activity, there would appear to be around 600 vulnerable servers present in Italy, 300 in Switzerland.
Other Information:
In the image an example of the security device placed by the criminal group inside a compromised server.
The first steps to take at this juncture are: applying security patches and reducing the exposure of critical services to the public internet.
To these should be added specific strategic assessments for securing critical systems such as a VMware server.
Other Info: Fortgale
Our Services: Fortgale Cyber Defence
TOX_ID
D6C324719AD0AA50A54E4F8DED8E8220D8698DD67B218B5429466C40E7F72657C015D86C7E4A