In May 2022, a new, particularly evasive Worm was observed for the first time, spreading in private and corporate networks through compromised USB sticks.
This new Worm has been given the name “Raspberry Robin“.
Worms that propagate through USB devices are certainly not new threats and very often, since they are old malware, command and control infrastructures are offline.
Raspberry Robin, on the other hand, is a real threat to the security of companies as:
- it is actively run by criminals;
- uses a sophisticated chain of compromise for defense evasion;
- it is used as a bridge for Ransomware-type attacks (fonte);
- uses compromised QNAP systems such as C2 infrastructure and TOR (The Onion Routing) network.
Preventing a Compromission
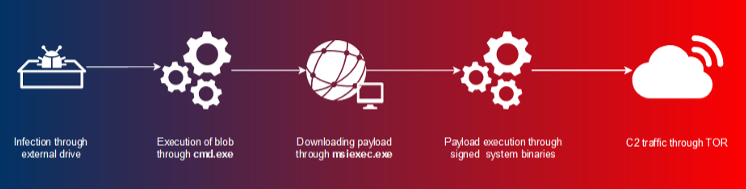
As previously mentioned, Malware enters the infrastructure via an initial compromise of a Workstation via a USB device.
When opening the USB device, the victim is shown a classic Windows connection:
Double clicking on the latter starts the chain of compromise by showing the correct opening of a destination folder on the screen while simultaneously launching a series of malicious commands:
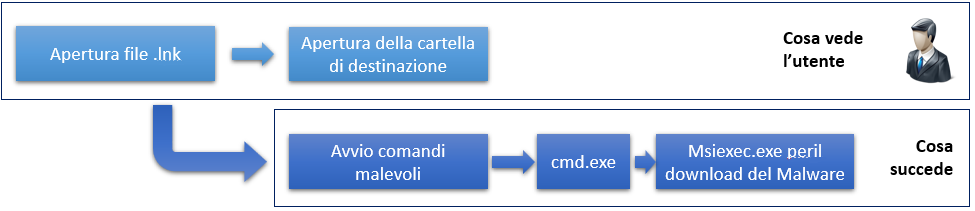
The first malicious command has the Downloader function and is used to actually download the Raspberry Robin malware:

A peculiarity of the Malware is the use of previously compromised QNAP servers in order to distribute the final malicious payload.
At this point, the download of the final payload completes the compromise phase and starts communications with the command and control server typically on the TOR (The Onion Routing) network:
Threat Detection Methods
Defending an infrastructure from a Raspberry Robin malware compromise can be performed on several levels.
Endpoint Security
With visibility into all enterprise systems, you can identify this type of compromise by detecting the execution of suspicious commands. In this case, the identification of the msiexec process associated with the presence of the http keyword could be a first alarm bell
Testing defence:
E’ possibile simulare l’attività offensiva, per poter testare l’effettiva capacità difensiva dei sistemi per questo genere di compromissione, lanciando il comando (Test Atomic Red Team):
msiexec.exe /q /i "https://github.com/redcanaryco/atomic-red-team/raw/master/atomics/T1218.007/src/T1218.007_JScript.msi"
Network and Intelligence Feed
It is possible to identify a compromise from Raspberry Robin malware and similar, using the information acquired from the company’s network, following two different approaches:
Use of Intrusion Detection System types::
- in this case, if correctly configured, the IDS system should have rules for identifying malicious traffic by sniffing communications with the C2.
Use of Intelligence Feed:
- leveraging information from intelligence feeds regarding malware and offensive systems. In fact, it is enough to correlate the information of IP addresses and domains to identify anomalous traffic!
Attention! In this case, from a defensive point of view, the identification of the threat occurs post-compromise! The system is already compromised and there may be impacts on the victim system’s information.
Fortgale Defence
Fortgale takes care of securing companies from these types of cyber threats and compromises! From defense against Malware attacks (Ransomware, Worms, Trojans and Spyware) to compromises of perimeter systems through application and system vulnerabilities.
We identify attackers from the first moment they try to take their first steps into the Company’s systems and networks.
With specialist services designed for different company characteristics, we can intervene on different aspects of defence.
Contact: info@fortgale.com