In the evolving landscape of cybersecurity threats, Fortgale is tracking PhishSurf Nebula, an advanced Cyber Espionage group active since 2021 and primarily targeting entities within the Banking & Finance and Real Estate sectors across Europe and North America.
In particular, most of the involved companies are Private Equity Firms, Hedge Funds, Venture Capitals and Luxury Real Estate Dealers.
PhishSurf Nebula (hereinafter PSN) has been demonstrated to possess advanced offensive capabilities, including the ability to bypass Multi-Factor Authentication (MFA) systems, a security measure employed by organizations to safeguard their employees from unauthorized access.
This article delves into the modus operandi and Tactics, Techniques and Procedures of PSN, highlighting aspects useful for Chief Information Security Officers (CISOs) and IT Departments in safeguarding their organizations and emphasizing the limitations of MFA when dealing with Advanced Cyber Attacks.
Attack Flow
- PSN identifies potential targets of interest
- A customized phishing website is built
- The phishing campaign is developed specifically for the specific targets
- Malicious emails, distributed in low volumes, are sent to victims
- Clicking on the malicious links and login leads to the deployment of persistence mechanisms on the victim’s account (Office 365, Google Workspace)
- Exfiltration, lateral movement, and privileges escalation activities are then carried on by the Threat Actor
 |
How to Defend
- Enhanced Security Measures: Given the persistent efficacy of PSN in circumventing MFA, CISOs and IT departments should contemplate the integration of supplementary security layers. This may encompass:
- The adoption of Behavioral Analysis
- The implementation of Identity Anomaly Detection activities
- The deployment of Advanced Endpoint Protection mechanisms
- Intelligence: Leverage Threat Intelligence feeds to ensure a proactive approach against evolving phishing techniques. Regular updates from these feeds facilitate staying ahead of the latest tactics employed by PSN and other threats
- Continuous Monitoring and Adaptation: The evolving nature of PSN’s tactics necessitates ongoing vigilance and the adaptation of security strategies to counter new threats effectively. Participate in industry-specific information-sharing groups could be an effective strategy to stay informed about the latest attack trends
- Employee Training and Awareness: Conduct routine phishing awareness training sessions for personnel, emphasizing the criticality of adeptly recognizing and promptly reporting phishing attempts to mitigate potential security breaches
Takeaways
A PSN breach could lead to severe C-Level accounts compromission having, as consequences, data exfiltration, financial losses and reputational damage.
Fortgale believes in an holistic approach that merges advanced cyber defense practices with leading cybersecurity technologies as an effective safeguard against sophisticated cyber threats like PSN.
Below is reported an in-depth analysis, with a complete overview of the attack patterns, Threat Actor, victims and campaigns.
In-Depth Analysis
PSN’s attack campaigns employ phishing emails as their attack vector to establish long-term access to victims’ account. These emails contain malicious attachments or links that redirect users to customized phishing websites.
PhishSurf Nebula’s attacks follow a standard infection process, which consists of mainly three steps:
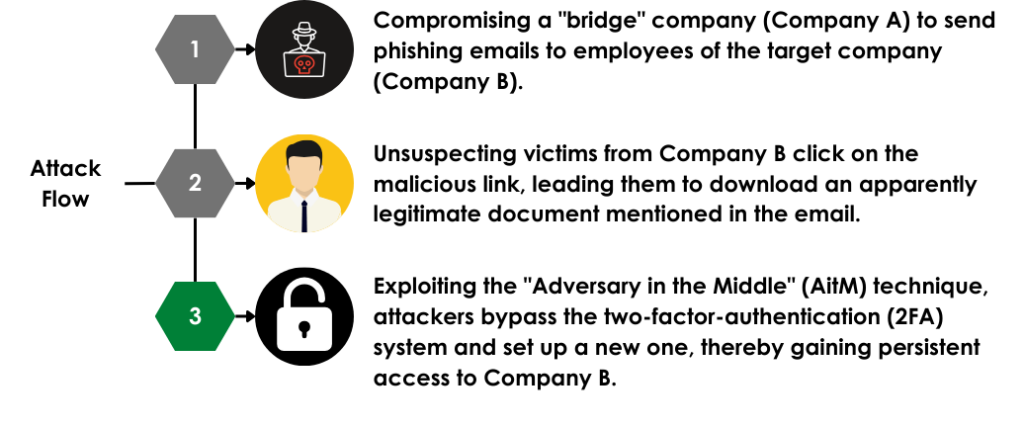 |
Key aspects of the attack:
- The phishing email’s link employs OpenRedirect technique (CWE-601 URL Redirection to Untrusted Site ‘Open Redirect’)
- After clicking the link, the user is redirected to an intermediate legitimate website, compromised by the threat actor.
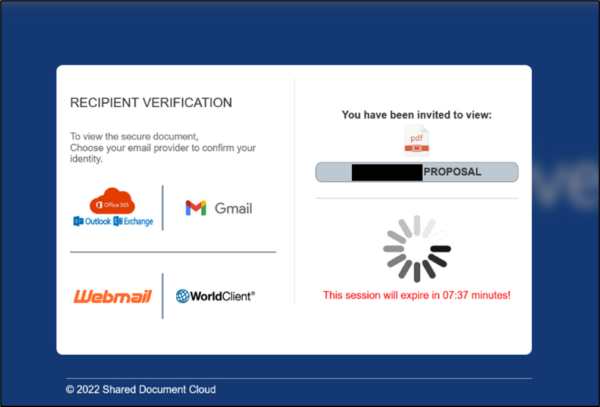
- The final landing page -shown above- is the one leveraging the PhishingKit.
- Different providers, in particular Office365, outlook. Exchange, Gmail, Webmail, are offered as login options, in order to maximize the surface of possible of victims.
Threat Actor
PhishSurf Nebula stands out due to its usage of a custom PhishingKit.
It seems that the Threat Actor abused of an open-source project called “Surf” (GitHub – headzoo/surf.) to execute Persistence activities on victims’ accounts.
The evidence surrounding this kit led Fortgale to designate the threat actor as “PhishSurf Nebula.”
The activities of the Threat Actor follow a cyclic rhythm, intensificating and reducing periodically.
Over the last nine months, Fortgale had gathered valuable information and insights:
 |
Targets
PhishSurf targets strategic users mainly in the context of investments and real estate. The aim is probably to exfiltrate information related to assets, funds and acquisitions in order to sell them to relevant stakeholders.
At the same time, breached systems and companies can be used as vectors (Company A) to other potential victims (Company B) as explained above.
Victims are mainly US and Europe-based companies.
Fortgale has identified several targets in recent months through its Threat Intelligence activities. Some of these targets include:
| Company | Country | Sector | First Seen |
|---|---|---|---|
| Bl** ***** Advisors | Switzerland | Financial Services | June 2023 |
| D****** AM | United Kingdom | Alternative Investments | May 2023 |
| Investment ********** Institute | Australia | Institutional Investments | March 2023 |
| ** Investments | Switzerland | Financial Services | March 2023 |
| V*** *** Advisors | United Kingdom | Financial Services | March 2023 |
| Q****** Financial | Austria | Financial Solutions | March 2023 |
| K****** Strategies | US | Investments | March 2023 |
| W***** Capital | Dubai | Venture Capital | February 2023 |
| *** Capital | Switzerland | Portfolio Management | February 2023 |
| ** Capital | Bulgaria | Real Estate | February 2023 |
| F***** Law LLP | United Kingdom | Legal Aservices | February 2023 |
| **-Innovation | Germany | Solar Energy | December 2022 |
| ** Advisors | US | Financial Advisors | December 2022 |
| **** Trust | Germany | Financial Services | December 2022 |
| ******* Masons | United Kingdom | Legal Services | November 2022 |
| E*******e | United Kingdom | Private Equity | October 2022 |
| B*** & S****** | Luxembourg | Legal Services | October 2022 |
| N**** S** Capital | Denmark | Investment Management | October 2022 |
| S******.at | Austria | Real Estate Project Develop. | October 2022 |
| B******* & Co | The Netherlands | Investment Management | October 2022 |
| L******** Capital | Canada | Investment Management | October 2022 |
| L************* BioCapital | Denmark | Trusts and Estates | October 2022 |
| L******** | Luxembourg | Investments | September 2022 |
| O**** Law | Germany | Legal Services for funds | September 2022 |
| A****** G***** Capital | Germany | Venture Capital | September 2022 |
| P****** | Denmark | Law Practices | September 2022 |
| ** Partners | Australia | Accounting | September 2022 |
| A***** | Belgium | Real Estate | September 2022 |
| S**** B** Ventures | sweden | Investment in Biotherapeutics | September 2022 |
| V****** Partners | Singapore | Venture Capital | September 2022 |
| E****** P**** Frères | France | Financial Services | September 2022 |
| S*** Ventures | United Kingdom | Venture Capital | September 2022 |
| A*****a | United Kingdom | Insurance | August 2022 |
| P*** F*** Partners | United Kingdom | Cliamate-Related Investments | August 2022 |
| F****** SA | Luxembourg | Insurance Company | August 2022 |
| A*** Partners | France | Financial Services | August 2022 |
| L*** Harbour | United Kingdom | Real Estate | August 2022 |
| ***** Management Services | United States | Property Management | August 2022 |
| T**** France | France | Financial Investors | August 2022 |
| S*****.com | United Kingdom | Commodity Investments | April 2022 |
Tactics and Recent Developments
The threat actor employs Digital Ocean to host fake login pages, creating multiple instances personalized with the target company’s name.
More than 300 unique IP Addresses have been collected, all having the same characteristics and interface.
The first sign of this strategy date back to 2021 and references have been seen until 4 months ago (August 2023).
After vanishing from Fortgale radars unexpectedly, PhishSurf Nebula has re-emerged in recent days.
Despite retaining its focus on targeting specific companies, PSN has made subtle changes to its infrastructure and tactics.
The latest insights reveal that the phishing kit is now hosted on “openresty” and exploits IPFS.io as a vector. IPFS, a modular suite of protocols, facilitates data organization and transfer through peer-to-peer networking.
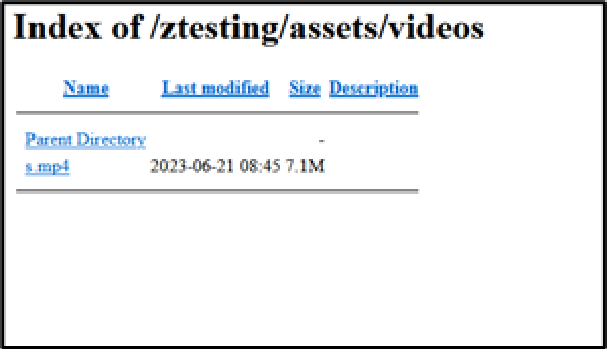
Furthermore, PSN has adopted a new strategy of hosting media elements on a third-party website.
 |
Similar Campaigns
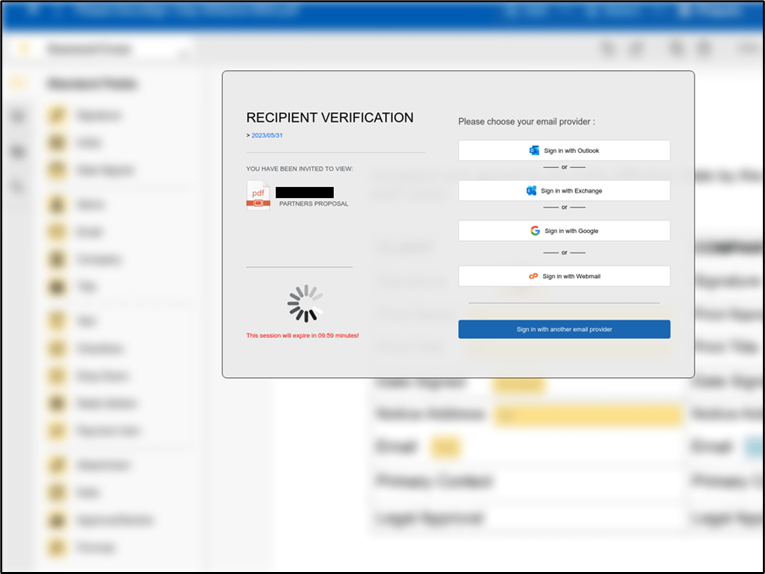 |
Fortgale’s research revealed similar campaigns sharing tactics and infrastructure with the tracked threat. A Phishing landing page with a slightly different design was found – image below.
Further investigation uncovered common backend components, affirming a medium-confidence connection to PhishSurf Nebula.
Editor’s Notes
Similarities were founded between our analysis and the Intrusion Set described at: link.
We are currently not publicy relasing Indicators Of Compromise (IOCs) since they would expose the involved companies.
Contact us for further information: info@fortgale.com
Attack Patterns
Mapping of Tactics, Techniques and Procedures (TTPs) used by the Threat Actor.
| CODE | NAME | DESCRIPTION |
| EXECUTION | ||
| T1204 | User Execution | An adversary may rely upon specific actions by a user in order to gain execution. Users may be subjected to social engineering to get them to execute malicious code by, for example, opening a malicious document file or link. |
| PERSISTENCE | ||
| T1111 | Two-Factor Authentication Interception | Adversaries may target multi-factor authentication (MFA) mechanisms, (i.e., smart cards, token generators, etc.) to gain access to credentials that can be used to access systems, services, and network resources |
| INITIAL ACCESS | ||
| T1192 | Spearphishing Link | Adversaries may send spearphishing emails with a malicious link in an attempt to gain access to victim systems. |






