In June 2022, a Malware campaign was analyzed (report) that exploits Google Ads and SEO Poisoning techniques to distribute the RedLine Stealer malware in the form of a Notepad++ installer (Drive-By Compromise; tactic: Initial Access).
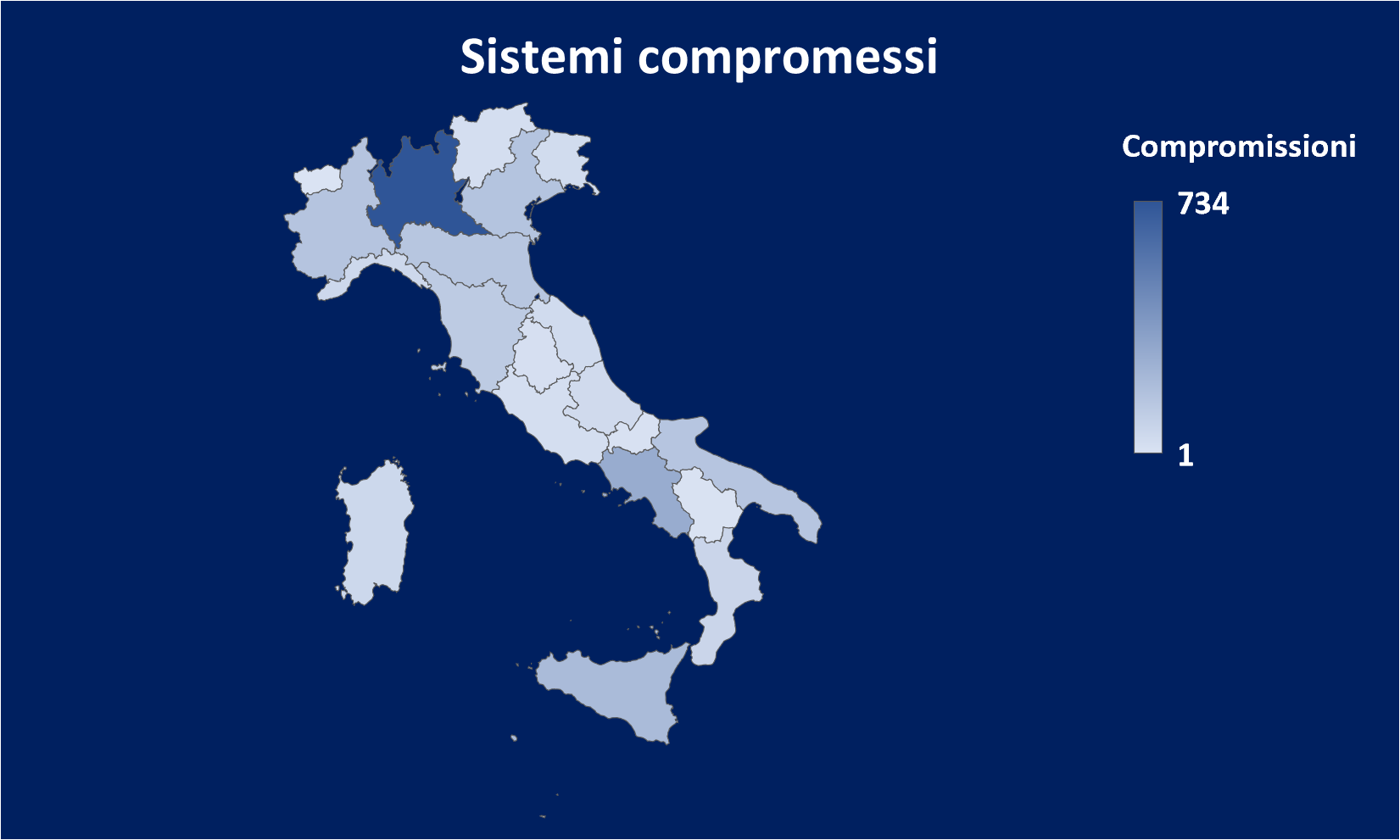
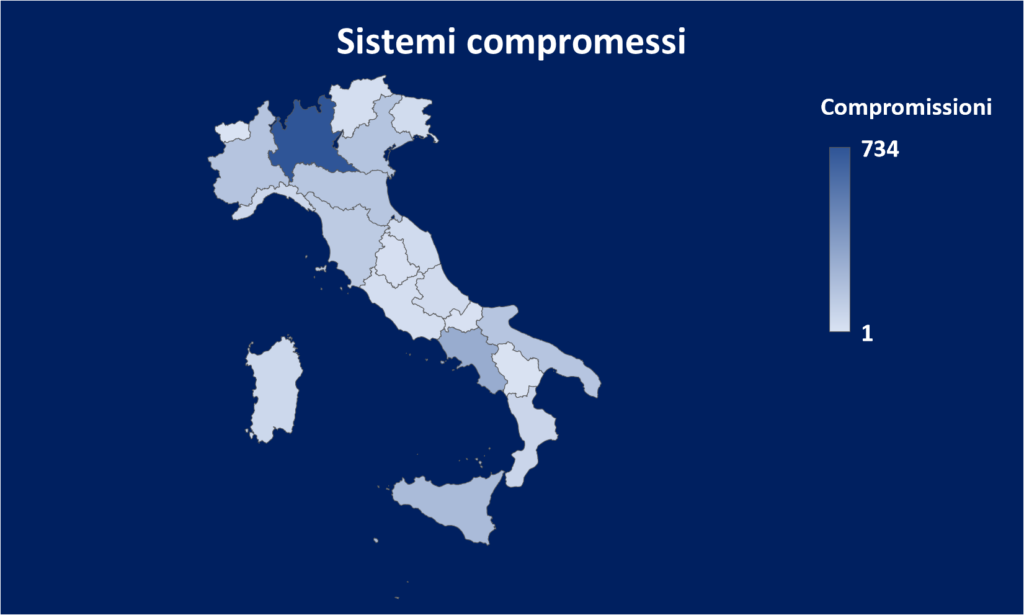
The target of the campaign is Italian systems and IT technical departments. In fact, 2686 systems were compromised by RedLine and put up for sale in the last 90 days (average price $10).
The victim, once the installation file is started, unknowingly runs the RedLine Stealer Malware.
Some considerations:
- RedLine is one of the most active Malware
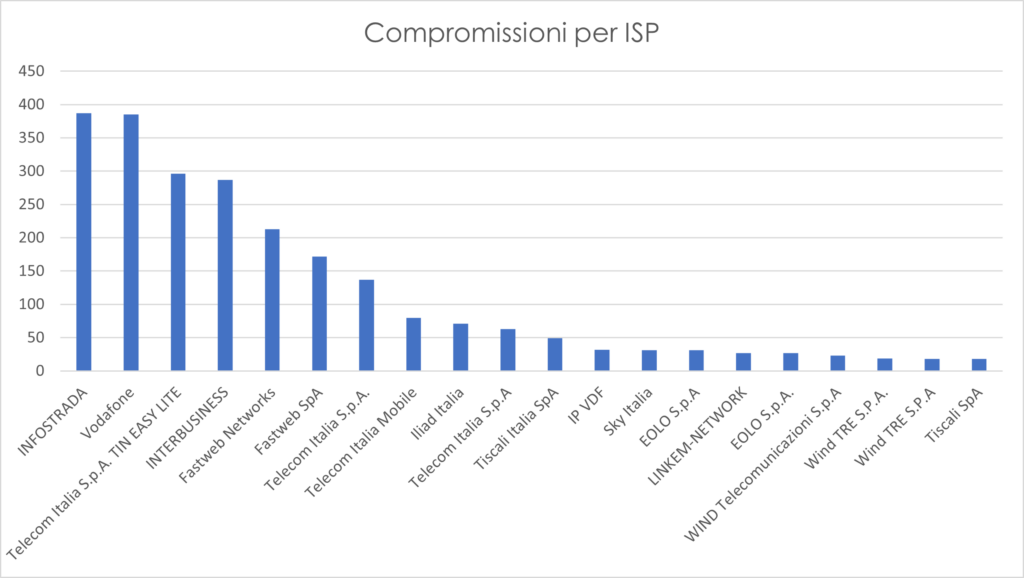
- the victim systems are sold in 2 different Black Markets
- There are around 15 seller accounts
- average selling price per seat: $10
- 2686 Italian systems put on sale in the last 90 days

Hopw to defend:
- activating a specialist service for protection from Cyber Attack (More Info)
- applying a perimeter lock for the notepad-edit-text[.]org domain (removing [ ])
- paying more attention to the websites used to download software to install on company systems
- perform threat hunting activities to search for potential compromises
What NOT to do:
- apply perimeter blocking for IP addresses (presence of Cloudflare CDN)
- uninstall legitimate versions of Notepad++ software
- prevent access to official Notepad++ software websites
SEO Poisoning
SEO poisoning, or search poisoning, is an offensive technique in which criminals create malicious websites and make them appear among the top results of search engines. In this way it is possible to create an offensive campaign targeted for specific victims who search for certain keywords.
The attackers’ aim is to convince the victim to download malicious software.
Website Analysis
By searching “notepad++” using the Google search engine, the advertising banner appears:
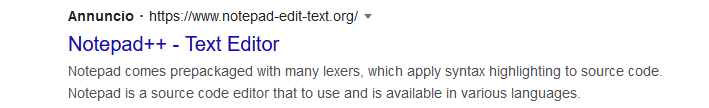
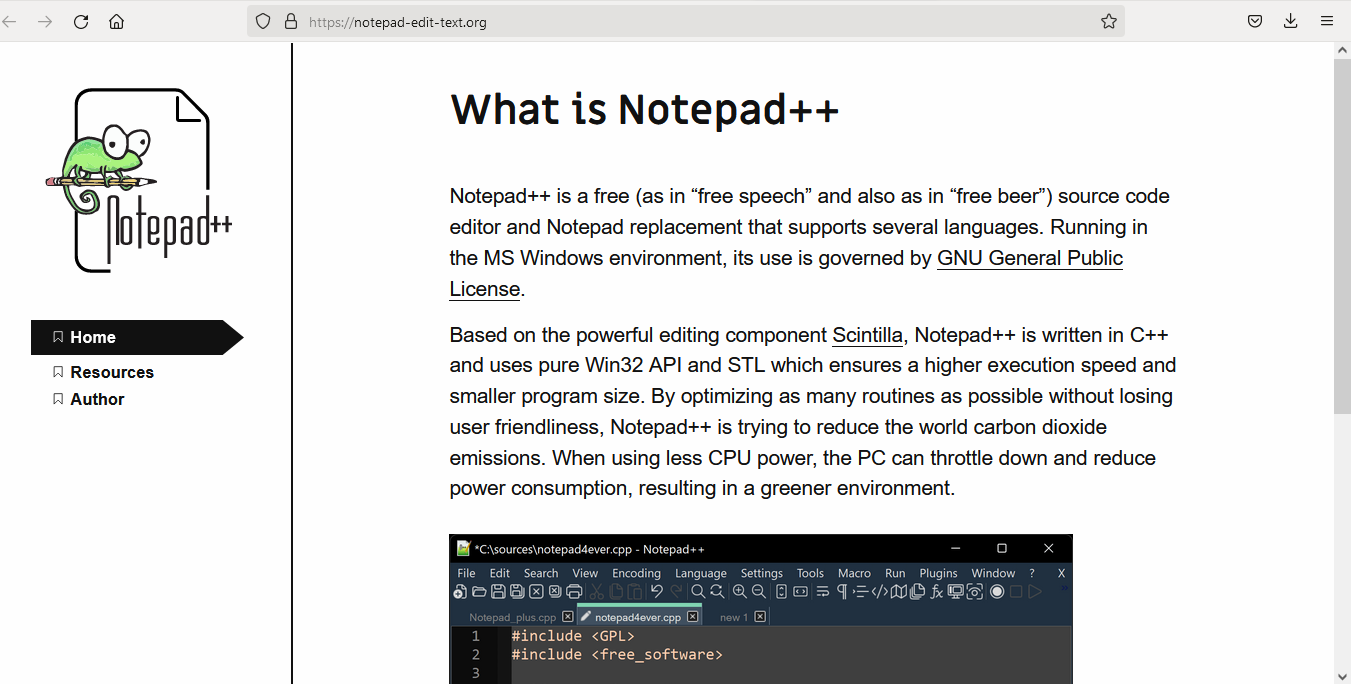
The website appears to be a copy of the original version of Notepad++. Inside, at the path https://notepad-edit-text[.]org/downloads, there is a list of previous versions, but the related links are not working and return the error code 404.
The only working link for downloading the malicious software is the one relating to version 8.4.1.
The Threat Actor mistakenly maintained a defunct link to “https://notepad-plus-plus.apps4p[.]org/“
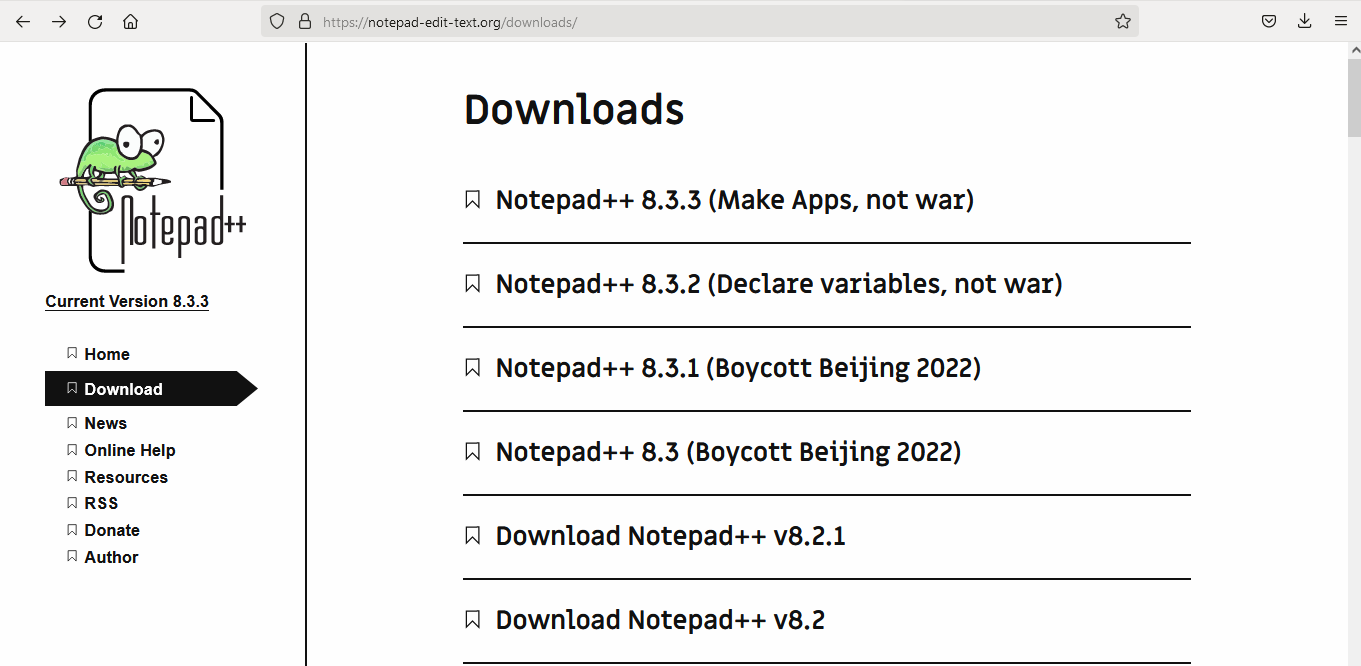
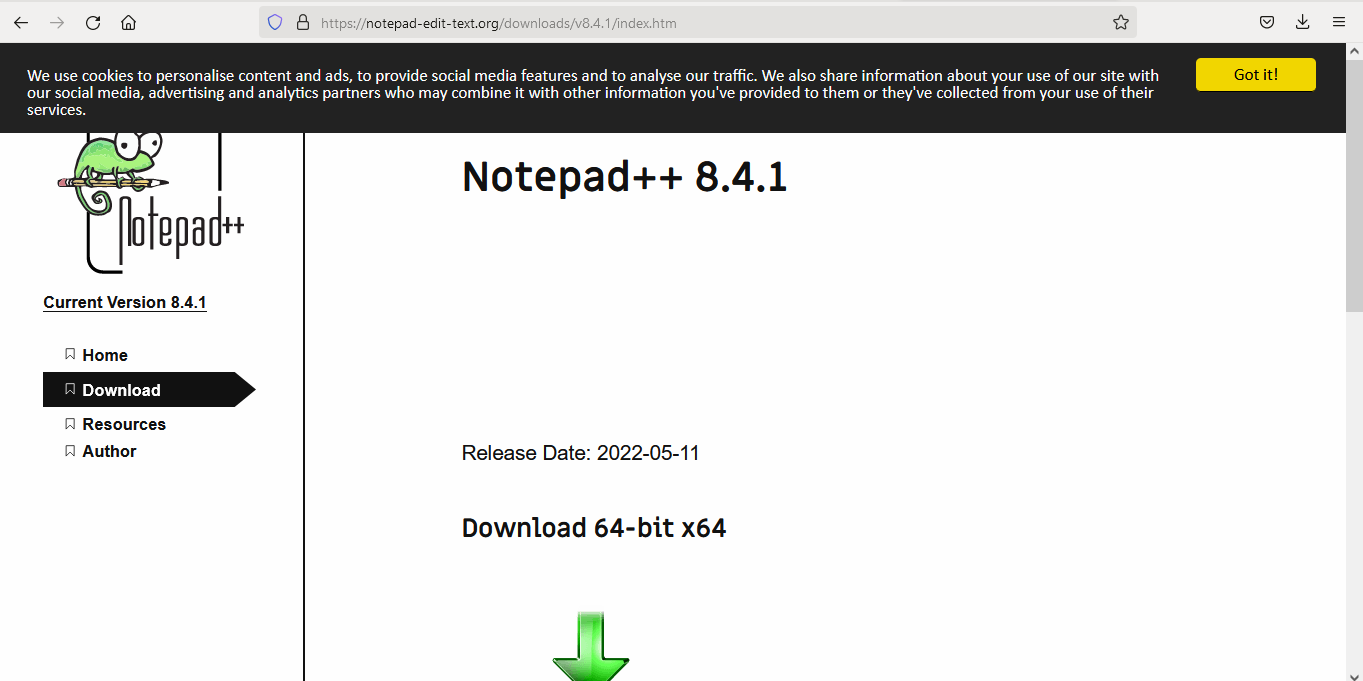
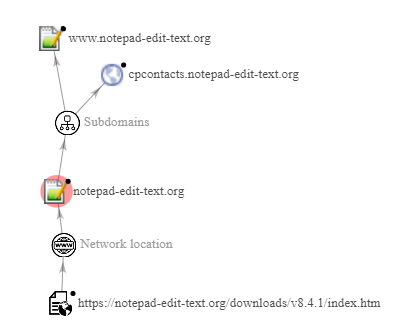
Domains Analysis
The notepad-edit-text[.]org domain was registered on May 23, 2022, currently protected by the Cloudflare service which masks its real origin addresses.
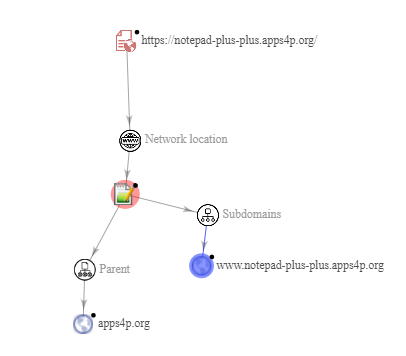
It is not possible to obtain useful information from the WHOIS of the sites:
Registry Registrant ID: REDACTED FOR PRIVACY Registrant Name: REDACTED FOR PRIVACY Registrant Organization: unknown Registrant Street: REDACTED FOR PRIVACY Registrant City: REDACTED FOR PRIVACY Registrant State/Province: VA Registrant Postal Code: REDACTED FOR PRIVACY Registrant Country: US Registrant Phone: REDACTED FOR PRIVACY Registrant Phone Ext: REDACTED FOR PRIVACY Registrant Fax: REDACTED FOR PRIVACY Registrant Fax Ext: REDACTED FOR PRIVACY
Info related to *-edit-text[.]org
Registry Registrant ID: REDACTED FOR PRIVACY Registrant Name: REDACTED FOR PRIVACY Registrant Organization: unknown Registrant Street: REDACTED FOR PRIVACY Registrant City: REDACTED FOR PRIVACY Registrant State/Province: VA Registrant Postal Code: REDACTED FOR PRIVACY Registrant Country: US Registrant Phone: REDACTED FOR PRIVACY Registrant Phone Ext: REDACTED FOR PRIVACY Registrant Fax: REDACTED FOR PRIVACY Registrant Fax Ext: REDACTED FOR PRIVACY
Info realted to *-plus-plus.apps4p[.]org
Analisi del IP C2
The malware contacts the IP address 194.36.177[.]124 geolocated in Ukraine and previously associated with other operations attributable to Malware RedLine Stealer.
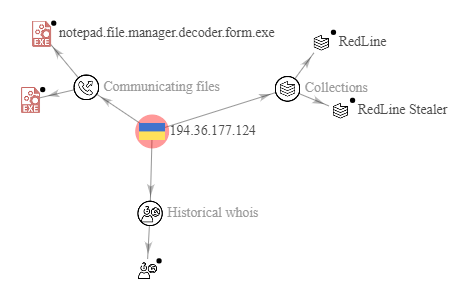
Indicators of Compromise (IOCs)
Malicious website domains:
- notepad-edit-text.org
- notepad-plus-plus.apps4p.org
C2 IP server addresses:
- 194.36.177.124