UPDATES:
27.11.2024: As mentioned by TrustWave, “Supercar Phishing Kit” has an high level of overlapping with the most recent update of “Rockstar 2FA Phishing-as-a-Service”
26.09.2024: As mentioned by Any.Run, “Supercar Nebula” has an high level of overlapping with “Storm-1575“
In August 2024, Fortgale identified and analyzed an extensive phishing campaign employing a previously publicy undocumented phishing kit now dubbed “Supercar Phishing Kit.” This campaign targets mainly Microsoft 365 users via deceptive emails, which contain various attachments designed to redirect recipients to a counterfeit login page. A few campaigns observed using the same Phishing Kit have been observed targeting enterprise Google accounts. Upon submission of credentials, the harvested data is exfiltrated to a domain themed around luxury cars.
Our investigation revealed that this campaign is part of a broader, ongoing attack wave. Variations of this attack have been observed targeting employees across multiple Italian companies, utilizing modified email themes and attachment types to evade detection.
The following sections provide a detailed breakdown of the campaign’s mechanics and the underlying structure of the phishing kit used in these attacks.
The ownership of “Supercar Phishing Kit” has been attributed to “Supercar Nebula“, and it is probably being distributed following a Phishing-as-a-Service (PaaS) model.
Key Findings:
- The analyzed phishing campaign is delivered via targeted emails with an HTML attachment containing a hardcoded fake Microsoft 365 login page.
- Upon submission, credentials are sent via a POST request to
https://shih-tzu-fancierson[.]ru. - Over 4000 (and still growing) similar domains, all luxury car-themed, have been identified as part of the same phishing kit infrastructure.
- Multiple campaigns have been observed using the same phishing kit, specifically targeting employees of Italian companies across different sectors.
Email Analysis
Overview
The phishing campaign initiates with a targeted email, specifically designed to deceive recipients. The goal is to lure recipients into opening the attached HTML file and unknowingly submitting their credentials.
Email Content
- Subject: “Attached is your e-fax issued on [REDACTED]”
- Body Text: The email suggests that an e-fax document is attached, prompting the recipient to open the file to view its contents.

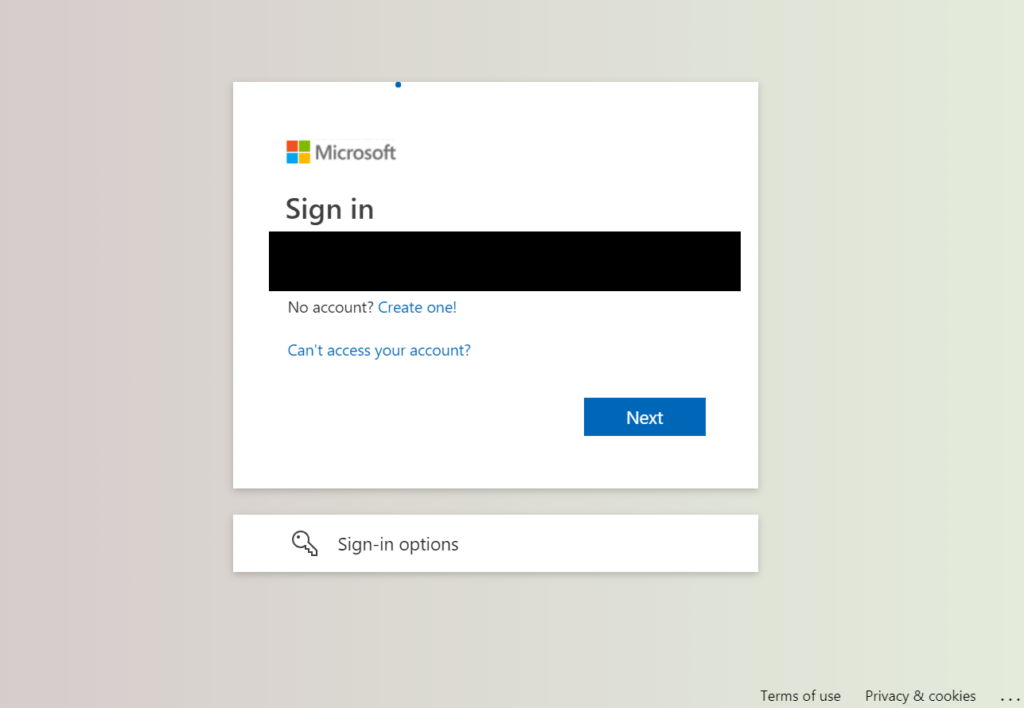
The HTML file attached to the email contains a hardcoded fake Microsoft 365 login page tailored for specific users.
Other Campaigns
In the same period we have observed other campaigns having the same structure for the exfiltration of credentials, using different email styles and topics. An example is reported below, themed around employee benefits:
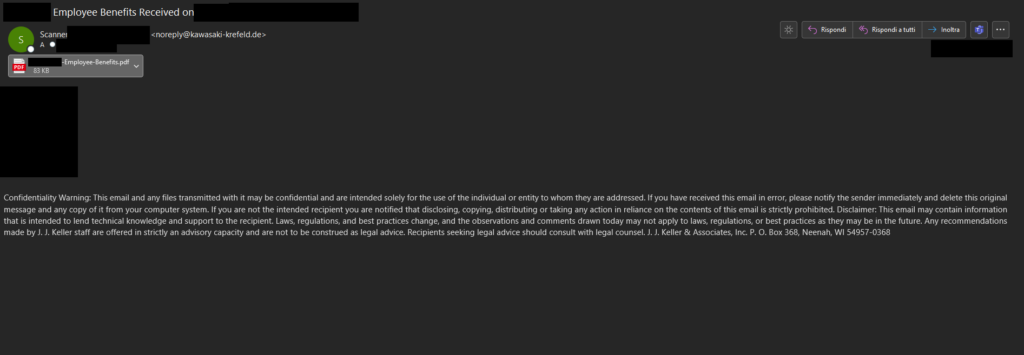
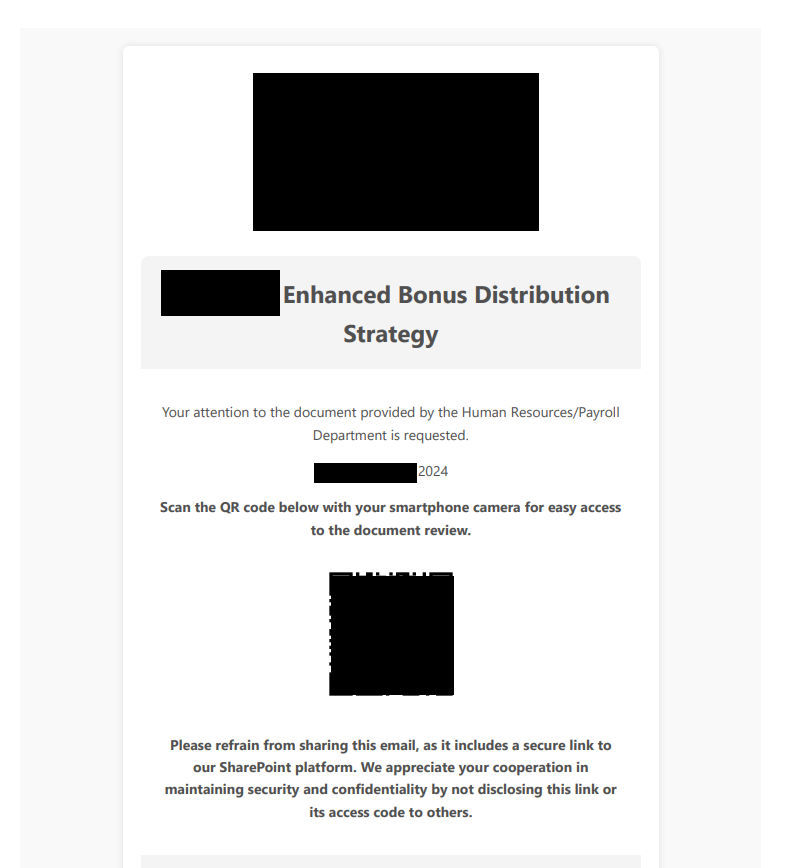
In this case the attachment is a pdf containing a QR code leading to a Phishing page:
Phishing Page Analysis
HTML Code Analysis
Page Structure
The HTML code used in different Phishing campaign related to Super Car Phishing Kit is customized with particular variables names and, more interestingly, comments referring to famous citations about the automobilistic world:
<!– <span>Driving unlocks the doors to exploration.</span> –>
<!– Life’s soundtrack is the hum of a well-tuned engine. –>
<!– <span>Driving unlocks the doors to exploration.</span> –>
<!–>Driving is freedom on the open road.</p> –>
<!– A car’s beauty is in its resilience. –>
Credential Exfiltration
The common pattern among all the different campaigns is observed when the victim click on the login button after inserting its credentials. In that moment a POST request is made to a malicious website – in the first case analyzed to: “https://shih-tzu-fancierson[.]ru“. More precisely, the request follows the pattern: “POST https.//maliciouswebsite.ru///randomnumber.php” where “randomnumber” is usually a three digit number.
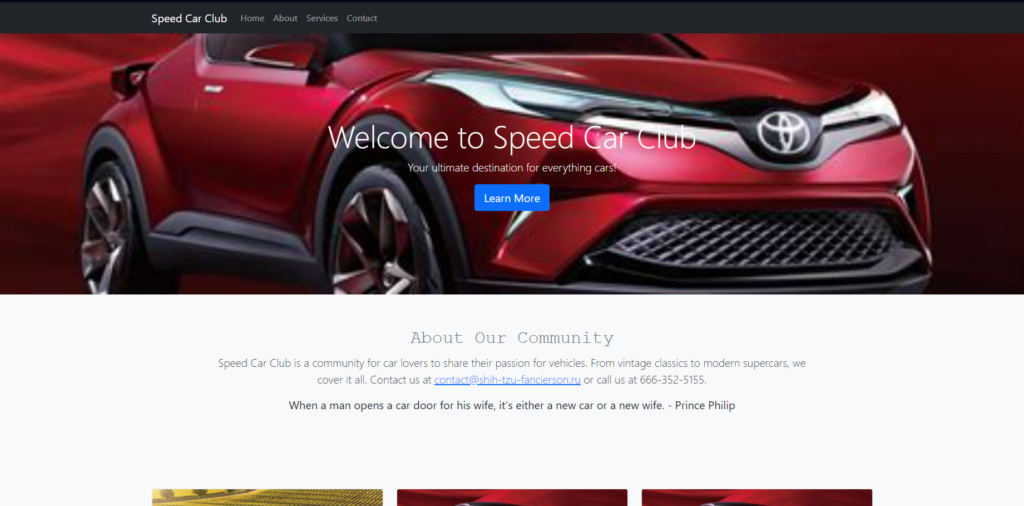
The second example reported exfitered the data to: “ulsevibeol[.]ru”, having similar characteristics:
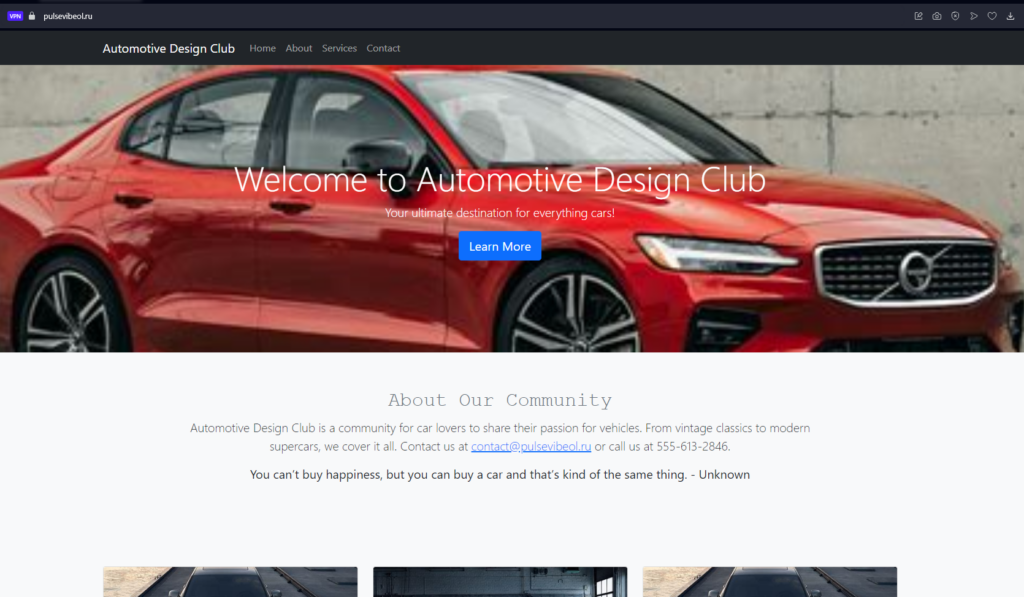
Infrastructure and Domain Analysis
Fortgale’s investigation uncovered a vast network of domains, totaling over 4000, all associated with the “Supercar Phishing Kit.” These domains share a common luxury car theme and are connected to phishing campaigns that have targeted various Italian companies.
Other examples of landing pages for similar domains:
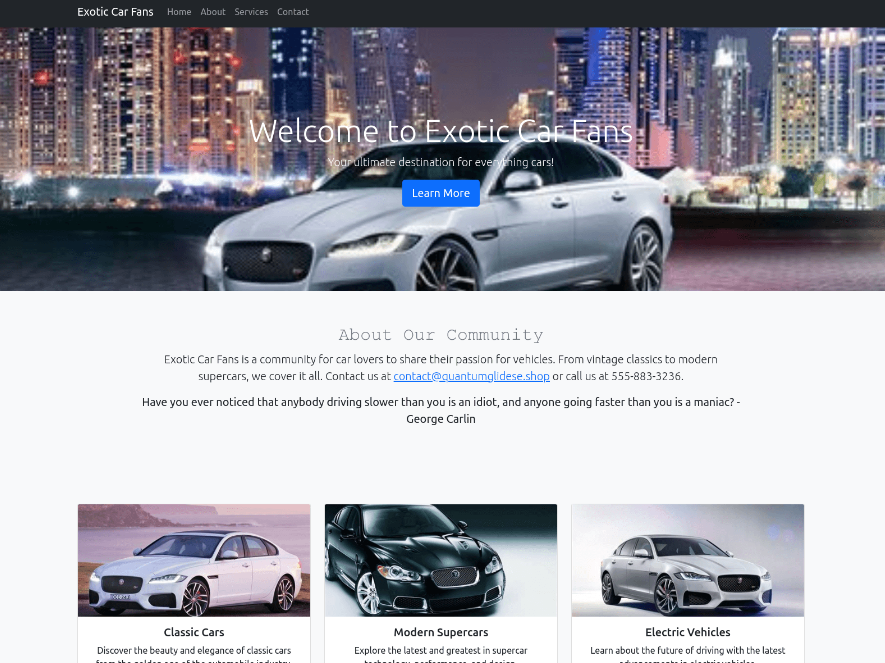
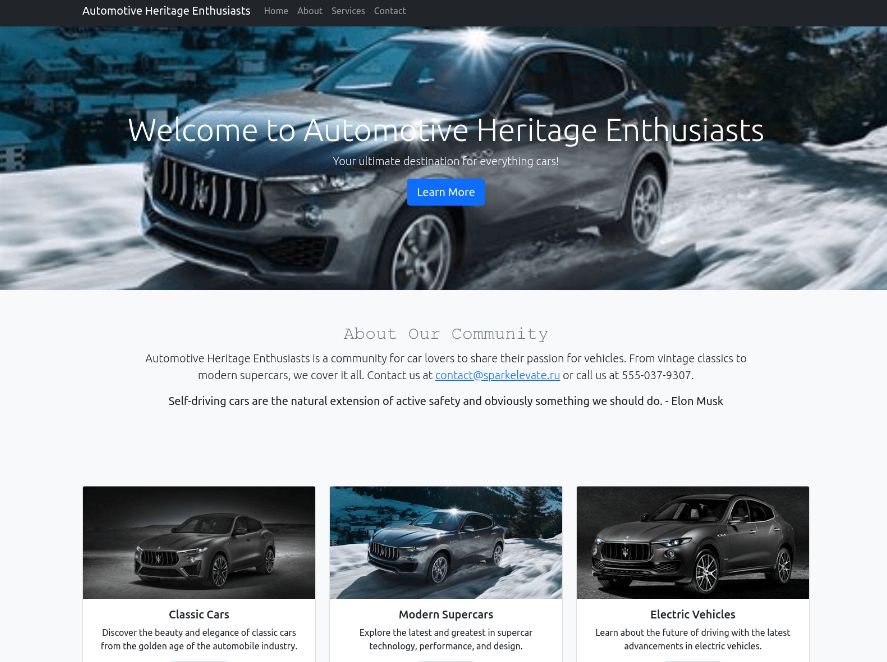
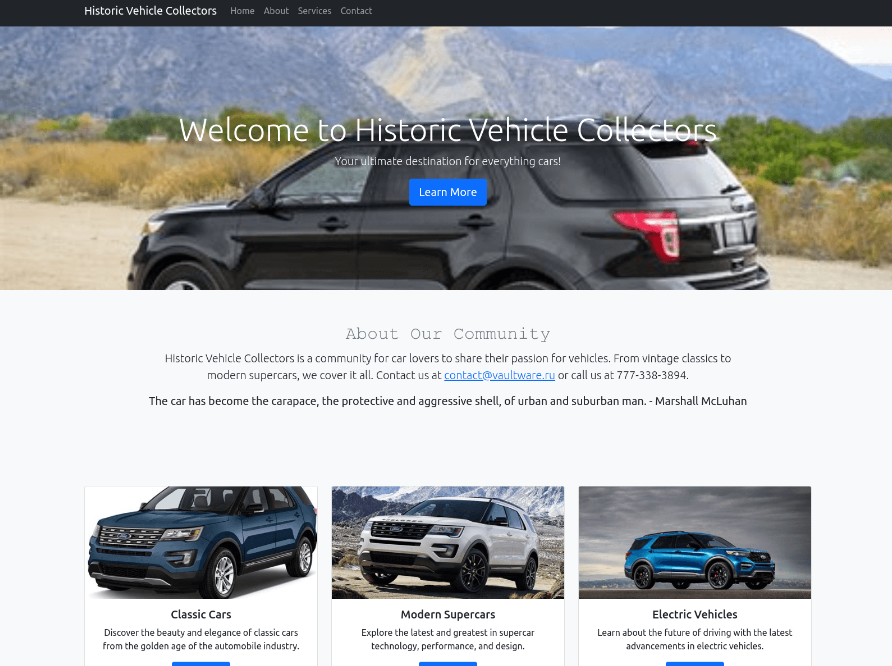
- Total Identified Domains: Over 4,000 domains have been identified, all employing similar tactics and infrastructure, and active over the past four months since around May 2024. While the majority of these websites use the “.ru” domain, others with extensions like “.shop”, “.moscow”, “.site” and “.su” have also been observed.
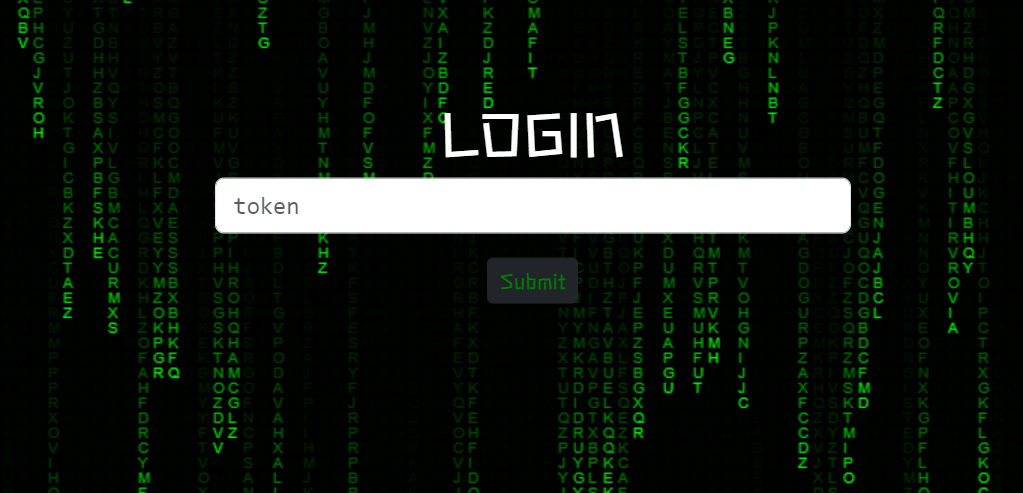
- Login Pages: Each domain features a login page, believed to be used by threat actors to manage collected data.
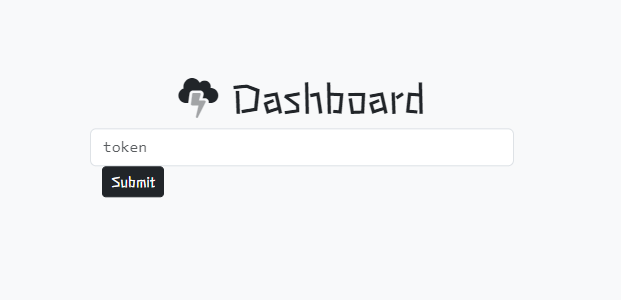
login page
These pages are likely designed to serve as a control panel for the attackers, where they can view and manage the stolen credentials. They are all protected by the Cloudflare Human Verification check.
Attribution
Fortgale attributes the development of the “Supercar Phishing Kit” to a threat actor group dubbed “Supercar Nebula“.
Similar Variants
While the most prevalent backend theme remains the supercar and luxury motif, we are also identifying other variations. Specifically, different domains are using the same phishing kit hidden behind similarly structured websites, but using distinct topics such as “Wellness and Self Care.” Notably, these variants are associated with the exfiltration of Google credentials.
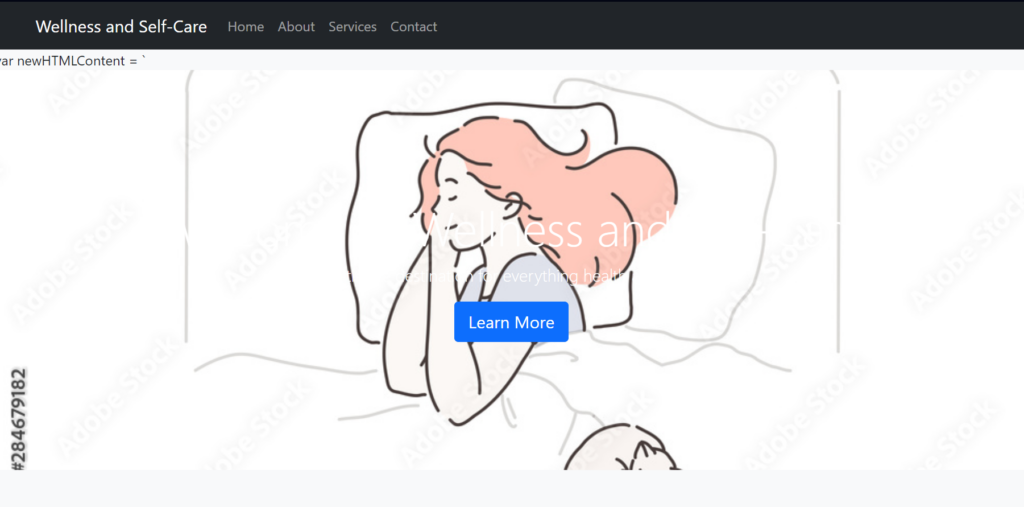
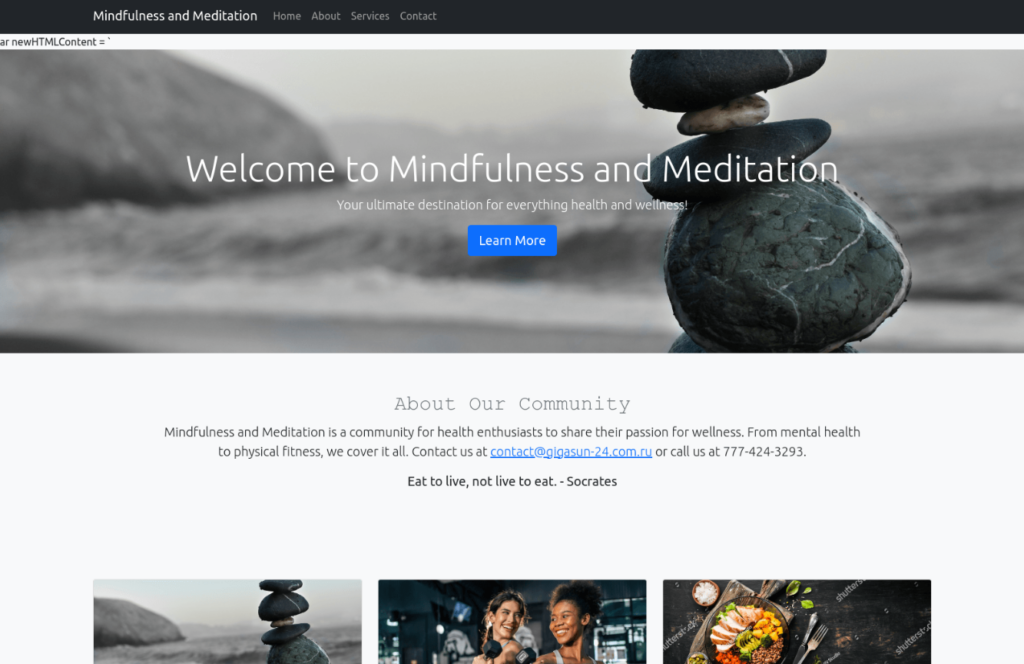
Interestingly, the login page for accessing the dashboard features a different design while retaining the core characteristics. This suggests that the phishing kit allows for some degree of customization or that these domains are using modified versions of the original code. The practice of altering existing code to create new variants of malicious tools is a common tactic among cyber threat actors.
Notably, campaigns associated with this specific variant do not show any kind of particular comment in the html of the Phishing page.