In the ever-evolving landscape of cyber threats, threat actors are constantly seeking new and innovative ways to deceive and compromise unsuspecting targets. One of the latest techniques that Fortgale observed gaining prominence over the last few months is the utilization of QR codes in phishing email campaigns (Spearphishing Technique – T1566).
In this article, we delve into the phenomenon of phishing emails leveraging QR codes – a technique define as “Quishing” – sheding light on the motivations behind this technique and sharing indicator of compromises (IOCs) and part of the data collected, to allow a better identification of these campaigns.
QR Codes
QR codes, short for Quick Response codes, were originally designed to facilitate rapid data exchange. However, their convenience has not gone unnoticed by cybercriminals. These matrix barcodes can encode a variety of information, including website URLs.
So, why are threat actors increasingly turning to QR codes in their phishing campaigns?
Mobile Devices
One significant driver behind the growing adoption of QR code-enabled phishing lies in the user behavior it exploits. QR codes entice users to scan them with their mobile devices, and herein lies an inherent vulnerability. Unlike their desktop counterparts, mobile devices often lack the same level of security, protection, and user awareness. Moreover, mobile screens are smaller, making it harder for users to scrutinize URLs and discern phishing attempts.
Enhanced Cover-Up
QR codes provide an effective means of concealing malicious URLs. To the human eye, the QR code appears innocuous, making it harder for users to discern the true nature of the link. Users tend to be more casual and less cautious when using their smartphones, especially for personal tasks like scanning QR codes. This complacency is something threat actors exploit.
Bypass Antispam engines
Quishing is a dangerous form of phishing because it is not recognized by most antispam filters or email security software. Antispam filters usually scan the text and attachments of the emails, but they do not analyze the content of the QR codes. Therefore, they cannot detect the malicious links hidden in the QR codes. Email security software may also fail to identify quishing emails as phishing, because they rely on indicators such as sender’s address, subject line, or domain name, which can be easily spoofed by the threat actors.
Real Cases
Over the last few months Fortgale identified different campaigns leveraging Squishing as a way to perform cyberattacks.
They all share the same tactics, mainly divided in three steps:
- Exploit psychological triggers, playing on the recipient’s curiosity, fear, or urgency to make the user to scan the QR Code, by inviting him to check a document or recover access to his account
- Redirect the user to a fake login page related to their account, usually created through a phishing kit like evilginix
- Exiltrate user credential to gain access to the user’s company systems
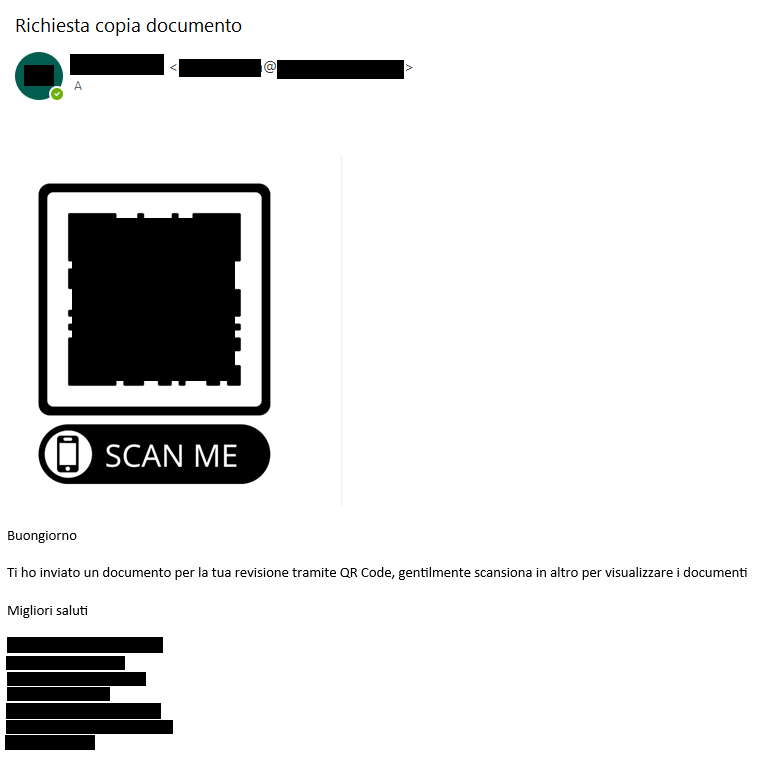
Phishers often impersonate legitimate organizations, making use of sender addresses that appear genuine at first glance.
In the following example, the attacker posed as the account manager of a real existent italian company.
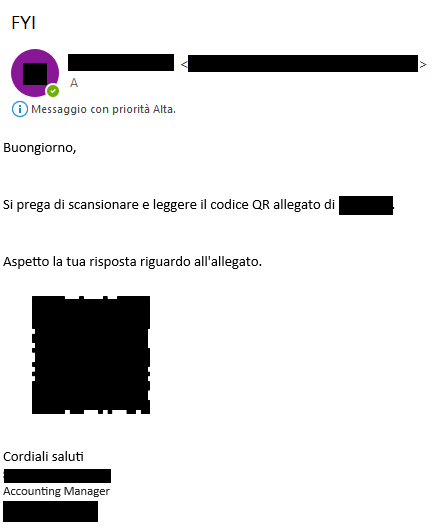
These phishing emails frequently revolve around topics like HR, payroll, or authentication.
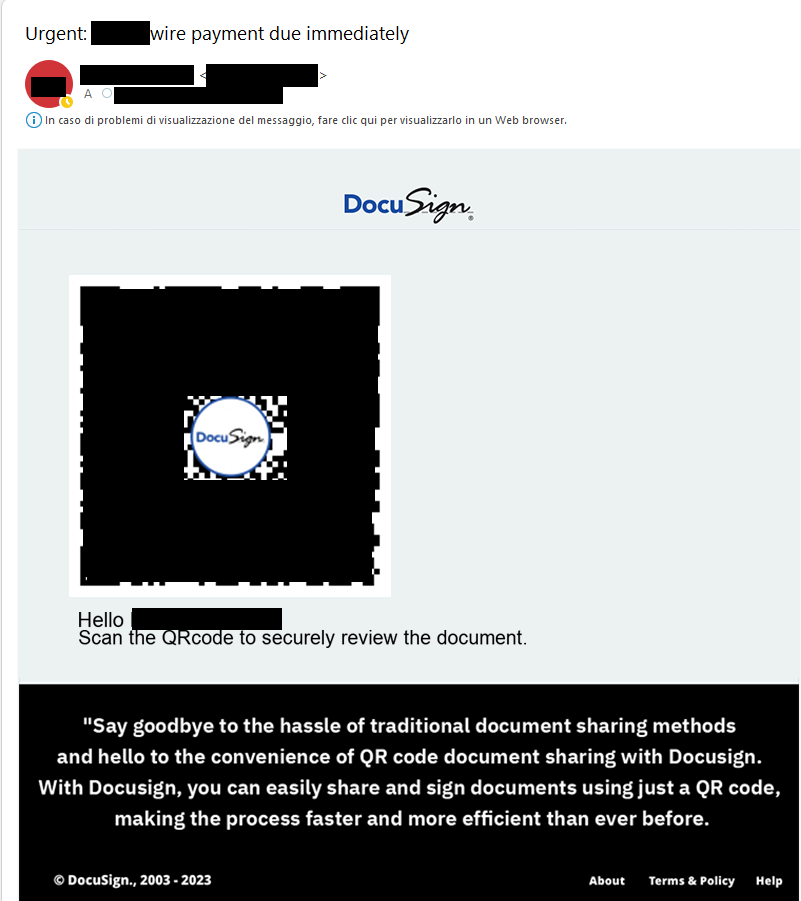
In the case below, for example, the theme is DocuSign and the victim is asked to review a document.
In these Quishing campaigns Sharepoint was used instead as theme, one related to Taxes payment and one to employee benefits:
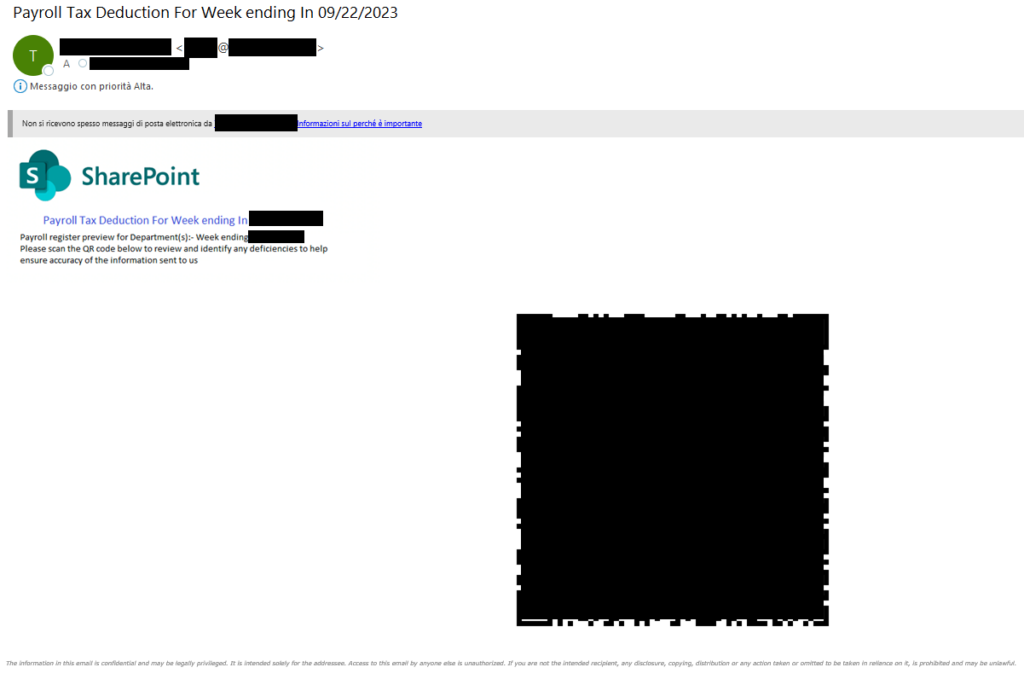
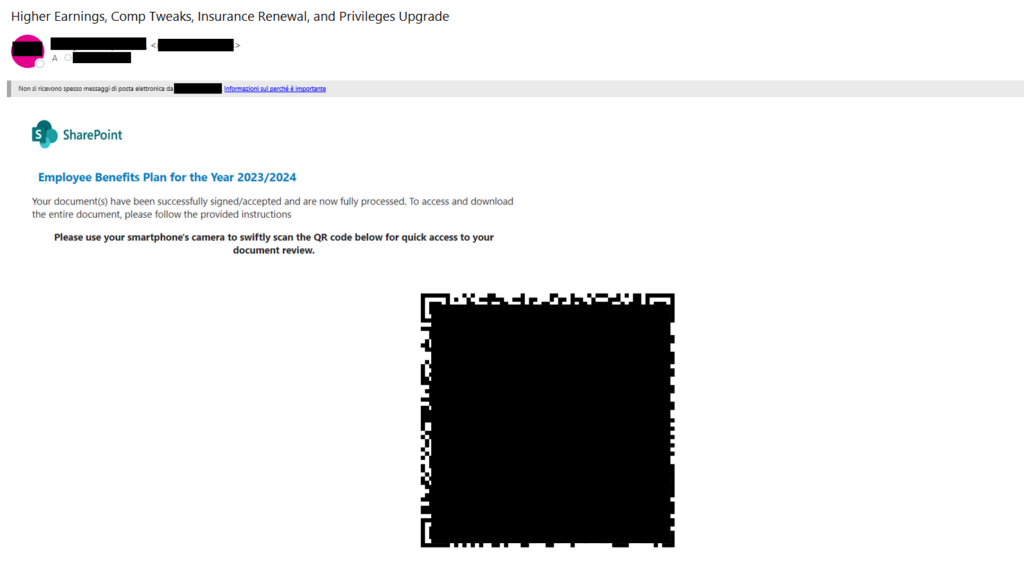
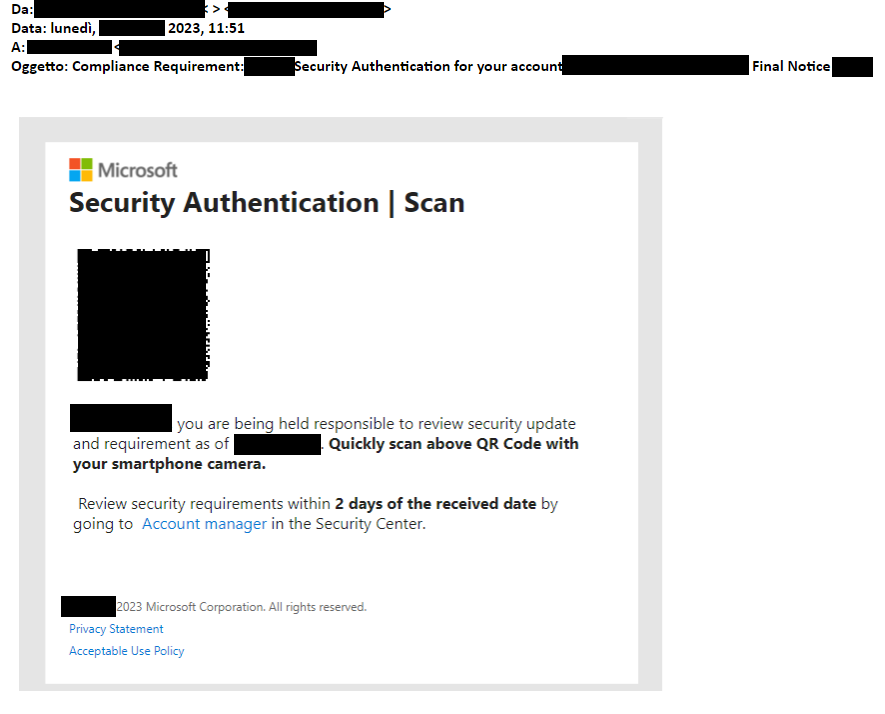
One of the primary risks involves the utilization of these campaigns for targeted attacks against C-Level individuals within companies, given their elevated permissions and access to sensitive information. In the following example, attackers meticulously replicated a security authentication message purportedly from Microsoft, prompting the user to scan a QR code for a purported security update review. The level of execution in this instance is higher than that of previous examples, demonstrating a tailored approach aimed at a specific target.
Conclusions
Understanding these patterns and indicators is crucial for cybersecurity experts when developing proactive measures and educating users about the risks associated with QR code-enabled phishing attacks. In the ever-shifting landscape of cyber threats, staying informed and prepared is paramount to safeguarding both individuals and organizations from falling prey to these deceptive schemes.