In 2021, Fortgale conducted an Incident Response operation to eradicate the WannaMine malware from the systems of an Italian company operating in the industrial sector. The malware proliferated across several hundred systems, exploiting a variety of propagation techniques.
Upon installation, WannaMine initiates cryptocurrency mining activities, leading to substantial disruptions in the company’s operations due to the overutilization of resources on compromised servers and workstations.
Fortgale orchestrated the Incident Response activities, successfully eliminating the malware from the affected infrastructure.

Key Operations Conducted by Fortgale for Incident Management:
- Conduct a risk assessment to gauge the level of threat to the organization
- Determine the methods through which the infrastructure was compromised
- Develop TTPs (Tactics, Techniques, and Procedures) essential for organizing an efficient and effective response
Identification of Cyber-Criminals (Threat Actors) within the Corporate Perimeter
- Identify systems under criminal control
- Identify user accounts exploited for Lateral Movement within the network
- Determine the methods used for gaining access to the infrastructure
Identification of the Offensive Structure (C2, IP addresses, domains)
Implementation of Blocks
- Limit or prevent further unauthorized access to the network
- Thwart ongoing offensive operations by the threat actors
Identification of Compromised Systems
Removal of Criminal Persistence from the Company’s Network
- Eliminate malware from affected systems
- Restore corporate IT services to full operational status
- Terminate communication channels (C2) utilized by the criminals
Specialized Activities Yield Comprehensive Security Restoration
The specialized activities carried out by Fortgale enabled the complete restoration of the security status of the infrastructure in a short time frame, thereby preventing further unauthorized access by criminals to the corporate network. During the operation, the presence of other malware compromises was observed, indicating the infiltration of multiple criminal groups within the network.
Characteristics of the WannaMine Worm
Unlike other compromises, the WannaMine worm propagated throughout the corporate network using a range of techniques: valid credentials (utilizing tools like Mimikatz and Empire modules) and exploiting vulnerabilities (such as EternalBlue, CVE-2017-0144).
Scale and Scope of the Operation
Given the scale of the compromise and the worm’s propagation capabilities, Fortgale conducted an Incident Response operation across several hundred systems (both workstations and servers). The operation involved the use of Python scripts and Cloud-based tool APIs for the definitive removal of the malware from all the company’s systems.
Specific Measures Taken by Fortgale Analysts
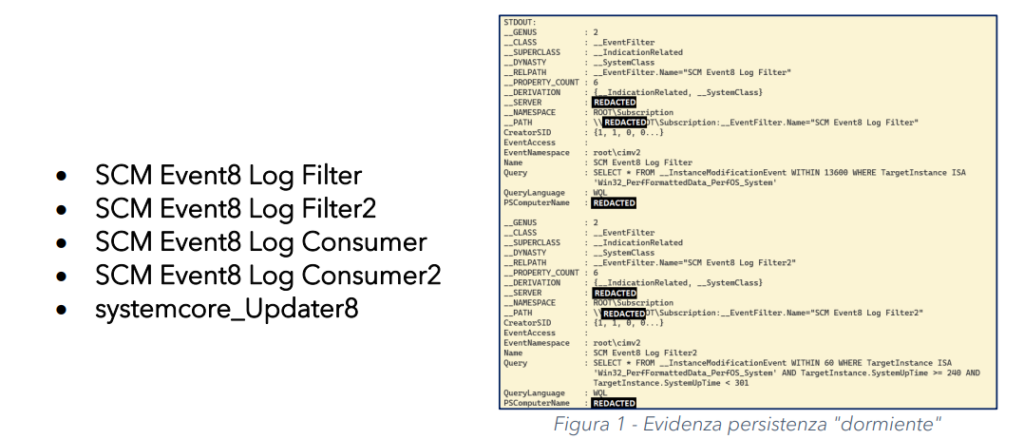
Specifically, Fortgale analysts removed the following WMI (Windows Management Instrumentation) objects that were not associated with security alerts but were used by the malware to maintain persistence:
(Note: The WMI objects removed are not listed in the original text, and therefore not included here.)
By rigorously executing these activities, Fortgale successfully restored the compromised infrastructure to full operational status while mitigating the risk of future breaches.
How to defend? Fortgale MDR!
Necessity for Specialized Skills in Defensive and Offensive Maneuvers
For these types of offensive tactics, it is crucial to employ specialized expertise in both defensive and offensive domains. Fortgale engages in Cyber Defence activities, safeguarding companies across various sectors and revenue scales by performing tasks such as:
The specialized nature of Fortgale’s Cyber Defence services enables the company to address a broad spectrum of cybersecurity challenges, reinforcing the operational and informational integrity of client enterprises.
- Security Monitoring
- Malware Analysis
- Threat Hunting
- Incident Response