Recently, our team identified the use of the PlugX Trojan (MITRE ID: S0013) within Italian corporate systems. The Trojan managed to infiltrate the target systems through the use of an infected USB device.

The system compromise is executed through the techniques of Replication Through Removable Media (T1091) and DLL Side-Loading (T1073).
In recent months, several technical articles have been published concerning the use of the PlugX Trojan. A recent analysis revealed that the Trojan has been enhanced with the HTML Smuggling technique, used in the initial phase of compromising the victim system.
This technique involves sending phishing emails containing attached files that hold JavaScript code capable of automatically downloading the malware.
PlugX, also known as Destroy RAT, Kaba, Korplug, Sogu, TIGERPLUG, and RedDelta, has been in existence since 2008 and is categorized as a Remote Access Trojan (RAT). Over time, it has undergone continuous modifications and improvements to evade security defenses.
The reuse of parts of its code by various Threat Actors has contributed to the malware’s spread, leading to numerous different versions.
Some analyses of this malware (by TrendMicro and Sophos) associate it with operations of Chinese APT groups. Its use has often been observed in compromises involving critical sectors such as the energy industry, defense, technology, the financial sector, and government institutions.
Recently, the focus of these Threat Actors has been shifting towards European entities, which are victims of an increasing number of attacks.
Details
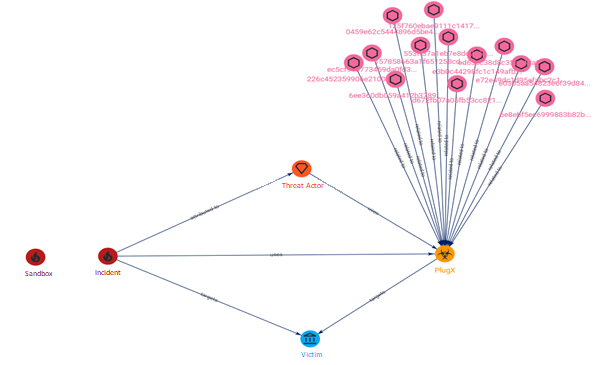
The variant of PlugX observed by our team exploits the execution of a .lnk file contained within a compromised USB device. When the user clicks on this file, the following command is executed:
"C:\Windows\System32\cmd.exe" /q /c " \ \RECYCLER.BIN\files\x32dbg.exe"
This executes the legitimate software “x32dbg.exe”, associated with the loading of the malicious dll “x32bridge.dll”.
This mechanism is known as “DLL Side-Loading” (T1073) and involves creating a malicious DLL with the same name as a legitimate DLL, so that it is loaded by legitimate software without raising suspicion.
The information obtained from the analysis suggests that, in this specific case, it is not an attack aimed at compromising the involved organization, but rather an inadvertent result of previous compromises.
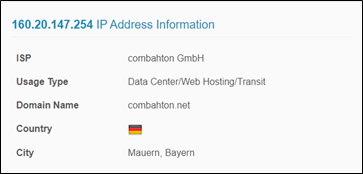
This variant of the trojan contacts the Command and Control (C2) server at the IP address 160.20.147[.]254 (Germany – ROUTERHOSTING).
Conclusions
The increased targeting of European users and the detection of the malware in Italy are indicators of an evolution and update in the attack patterns of PlugX. It represents a particularly complex and insidious threat, especially as it is used for espionage activities typical of various Advanced Persistent Threat (APT) groups. These groups carry out targeted attacks with specific objectives to extract sensitive information.
At the end of this article, we share the Indicators of Compromise (IOCs) associated with this threat.
Attack Patterns
| CODE | NAME | DESCRIPTION |
| DEFENSE-EVASION | ||
| T1218 | System Binary Proxy Execution | Adversaries may bypass process and/or signature-based defenses by proxying execution of malicious content with signed, or otherwise trusted, binaries. |
| T1036 | Masquerading | Masquerading occurs when the name or location of an object, legitimate or malicious, is manipulated or abused for the sake of evading defenses. |
| T1574 | Hijack Execution Flow | Adversaries may execute their own malicious payloads by hijacking the way operating systems run programs. |
| T1202 | Indirect Command Execution | Adversaries may abuse utilities that allow for command execution to bypass security restrictions that limit the use of command-line interpreters. |
| T1073 | DLL Side-Loading | Adversaries may execute their own malicious payloads by side-loading DLLs. |
| T1140 | Deobfuscate/Decode Files or Information | Adversaries may require separate mechanisms to decode or deobfuscate information depending on how they intend to use it. |
| PERSISTENCE | ||
| T1603 | Scheduled Task/Job | Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. |
| PRIVILEGE-ESCALATION | ||
| T1547 | Boot or Logon Autostart Execution | Adversaries may configure system settings to automatically execute a program during system boot to maintain persistence on compromised systems. |
| EXECUTION | ||
| T1204 | User Execution | An adversary may rely upon specific actions by a user to gain execution. |
Indicator of Compromise (IOC)
| INFO | TYPE | SHA-256 |
| adobe.dat | application/octet-stream | 125f760ebae9111c14170ce3d185fa59f6d38ffee60da44cc59cbb5174fe5d44 |
| dismcore.dll | Win32 DLL | b4f1cae6622cd459388294afb418cb0af7a5cb82f367933e57ab8c1fb0a8a8a7 |
| x32bridge.dll | Win32 DLL | 0490ceace858ff7949b90ab4acf4867878815d2557089c179c9971b2dd0918b9 |
| hex.dll | Win32 DLL | a75598a76d2df2afc747757d3ec278285c5262fadf654be2243f8e08762dbcea |
| mpsvc.dll | Win32 DLL | 2e5412c25b53b9f86dd03ef44db66ed02bf7f984ac012f439efdc1835a05e6b3 |
| SafeGuard.exe | application/x-ms-dos-exec | (legittimo) 0459e62c5444896d5be404c559c834ba455fa5cae1689c70fc8c61bc15468681 |
| msvcp120.dll | Win32 DLL | (legittimo) d672fb07a05fb53cc821da0fde823fdfd46071854fe8c6c5ea83d7450b978ecb |
| msvcr120.dll | Win32 DLL | (legittimo) e0305aa54823e6f39d847f8b651b7bd08c085f1dbbcb5c3c1ce1942c0fa1e9fa |
| AUG.exe | application/x-ms-dos-exec | (legittimo) 6e8ebf5ec6999883b82b9b41fcd53a4266b236e86cb41fbc450a3b7c64e708c0 |
| x32bridge.dat | application/octet-stream | e72e49dc1d95efabc2c12c46df373173f2e20dab715caf58b1be9ca41ec0e172 |
| x32dbg.exe | application/x-ms-dos-exec | (legittimo) ec5cf913773459da0fd30bb282fb0144b85717aa6ce660e81a0bad24a2f23e15 |
| Groza_1.dat | application/octet-stream | 553ff37a1eb7e8dc226a83fa143d6aab8a305771bf0cec7b94f4202dcd1f55b2 |
| f23d2c37.exe | application/x-ms-dos-exec | 6ee360db059a412b3789040af43af7cab6e414d4cad3d72debf325b7ff2ad2b5 |
| 2682ece8.exe | application/x-ms-dos-exec | 157858663a1f651258cdbfe114d331b33f23994c1a9732e27f783697eb47a4e8 |
| aki.dat | application/octet-stream | 226c452359906e2100b81f9a6ac92342a3fc53a77516d80bdebc56df76909218 |
| Removable Disk(3GB).lnk | application/octet-stream | ed63ec38d8c35a140a061a2af4df7ed7751ab17d84f322969b8d18abd38cf17c |
| C2 | IPv4 | 160.20.147[.]254 |





