In April 2021, an unidentified Gold Southfield operator carried out a Ransomware attack against a European company. The initial access is performed by Gold Cabin, an access broker, that deploys IceID (Bokbot), a Remote Access Tool (RAT) malware[link].
Once inside the company, the access broker passes privileges to the main operator who deploys the REvil ransomware. This threat actor uses typical escalation techniques and moves laterally using CobaltStrike, Mimikatz, and other tools.
In this article, we focus on the anomaly related to the time zone on the attacker’s machine. Our information on the attack operations that were performed identifies cyber activity over roughly 10 days.
In line with the times of the attack shared also by other cybersecurity groups [link], we go ahead to investigating the actual times when the attack operations were performed, with surprising results. We are the first to identify that this piece of malware (csharp-streamer.exe) can be traced back to a Gold Southfield operator. Also, most surprisingly, despite REvil’s mandate to work exclusively with Russian-speaking cybercriminals, we find that UTC time zone of the operations is UTC-8 (West Coast, US/Canada).
Table of Contents
Threat Actors involved and Profiles
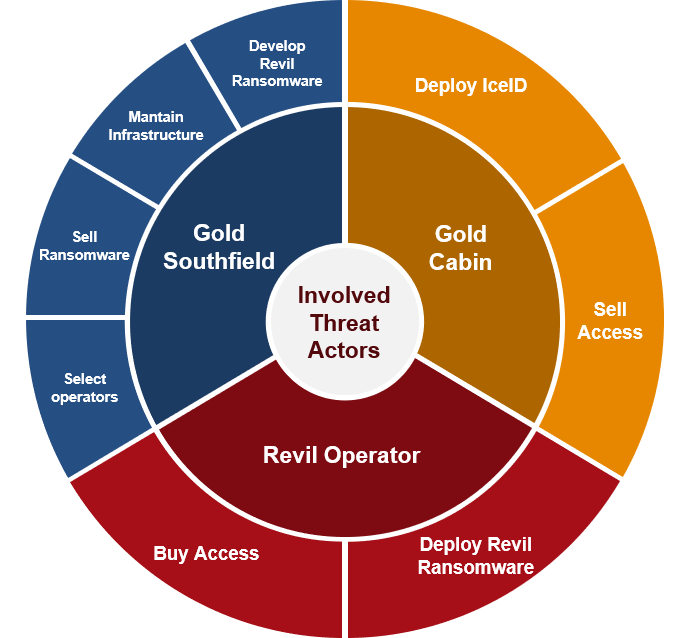
Gold Southfield (Pinchy Spider) is a financially motivated cybercriminal threat group that authors and operates the REvil (aka Sodinokibi) ransomware on behalf of various affiliated threat groups.
Reference: Link 1, Link 2
Gold Southfield operates the backend infrastructure used by affiliates (also called partners) to create malware builds and to collect ransom payments from victims. REvil partners are recruited on semi-exclusive underground forums by the Russian-speaking Gold Southfield operators who refuse to work with English-speaking criminals.
In December 2019, Gold Southfield began operating a name-and-shame style website that uses stolen data from intrusions to generate additional leverage against victims.
Gold Cabin is a financially motivated cybercriminal threat group operating a malware distribution service on behalf of numerous customers since 2018. Gold Cabin uses malicious documents, often contained in password-protected archives delivered through email to download and execute payloads. The second-stage payloads are most frequently Gozi ISFB (Ursnif) or IcedID (Bokbot), sometimes using intermediary malware like Valak.
Reference: Link 1, Link 2
Threat actor infrastructure
First, we explain the threat actor’s architecture and the attack details based on CobaltStrike Post-Exploitation Framework – a very common tool used in this type of cyber operation.
The attack in a nutshell – our analysis:
- First to discover that the “csharp-streamer.exe” code is related to the REvil ransomware attack (see below IOC of similar samples);
- Identified CobaltStrike C2 server and configuration (Fig.2, Section 2);
- Identified the UTC-8 time zone setting (Fig. 3, Section 2);
- Analysis of the regular working times of the attackers across different time zones and (Fig. 4, Section 3).
The CobaltStrike C2 server, located in Europe, belongs to a German company which offers hosting sevices. The threat actor used a remote host “WIN-XXXX” to connect to the internal server through an SSL tunnel. They used RDP/SMB services and the compromised credentials to gain access to other systems in the infrastructure:
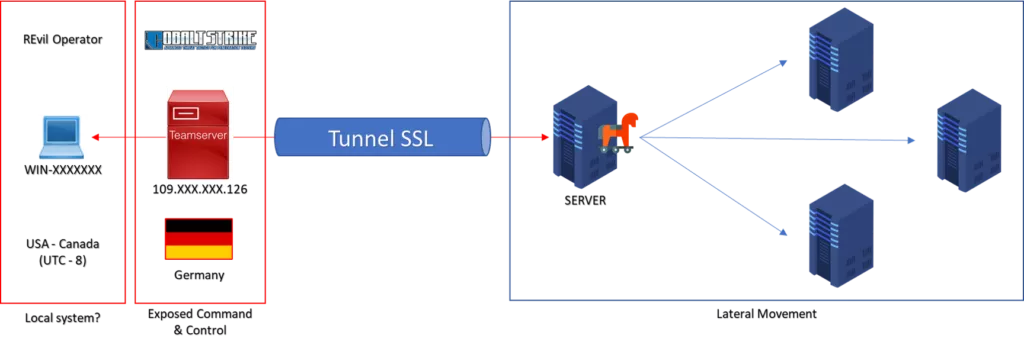
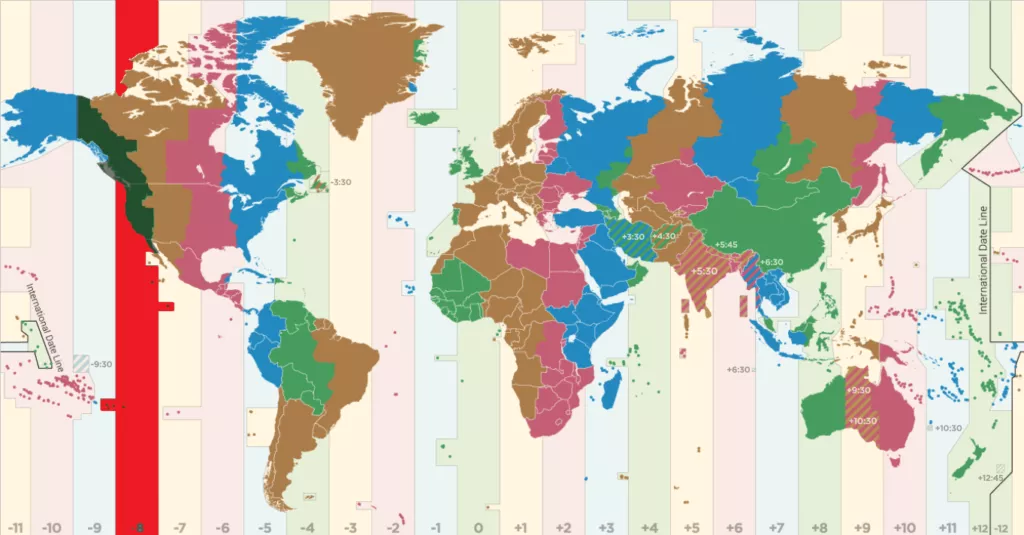
Interestingly, RDP servers that received the malicious connections noted the UTC time difference between server and client, and logged it in Windows Event Log. This information places the “WIN-XXXX” host in UTC-8 time zone (West Coast, USA & Canada), which in turn does not correspond to how Gold Southfield typically operates and recruits.
REvil partners are recruited on semi-exclusive underground forums by the Russian-speaking operators of GOLD SOUTHFIELD, who refuse to work with English-speaking criminals.
UTC-8 (USA – Canada) seems to not fit with threat actor profile.
Review of working hours
The UTC time zone setting can be easily manipulated and is not a conclusive proof. So, when analysing the incident, we took into account also other information of the attack.
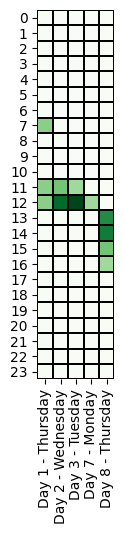
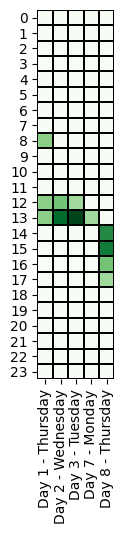
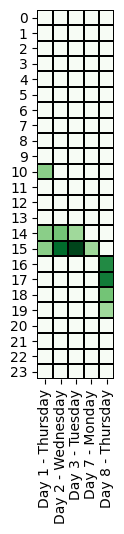
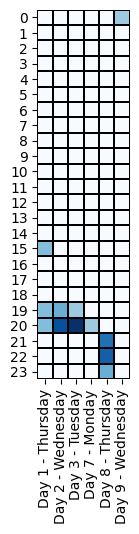
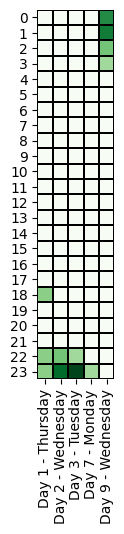
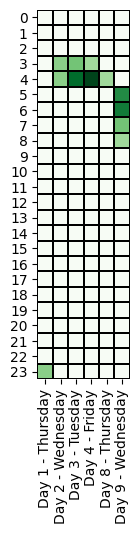
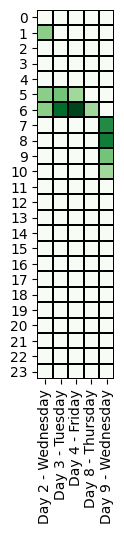
Specifically, we evaluated if the threat actor’s working time zone is compatible with the time zone of the cyber operations. Below, we compare the time of the offensive activities across different time zones.
The first access (Day 1, 15:00 UTC-0) is made by Gold Cabin, an access broker that compromised a workstation (probably through an email attachment containing an IceID malware), and moved inside the server through privilege escalation activities, then sold access to the REvil operator.
UTC-0 was used as a reference for the malicious activities:
Seattle
Los Angeles
New York
Moscow
Beijing
Sydney
Concluding remarks
Our analysis shows that REvil operator is a sophisticated and well-organized threat actor, capable of quickly achieving persistence across multiple systems after initial access.
Most notably, the ransomware attack operators always worked within a window of 2 hours per day (UTC-0), except for Days 8 and 9 when system administrators are typically off-duty:
| Day | Time of Cyber Attack |
| 1 , 2 , 3 , 7 | 19:00 – 21:00 |
| 8-9 (Ransomware) | 21:00 – 01:00 |
We observe that the attacker’s operations can have a range of up to 6 hours. In addition, we note that there were no activities on Saturday and Sunday.
The timing of the operations suggest that the threat actor(s) may be located in Eastern Europe (UTC+3, from 22:00 to 4:00), but we also note that US West Coast fits these working hours (UTC-8, from 11:00 to 17:00).
The information published in this article is our assessment of the incident and hacking activity. We do not have enough data to determine the actual location of the REvil operator. We think this could be an interesting starting point for further investigations.
Fortgale Cyber Defence
Fortgale provides specialized managed defence services for advanced protection against cyber attacks. We are an industry-leading company with a specialist team in Cyber Threat Intelligence and Threat Hunting.
For more information: contact
IOC and related samples
| Similar samples | C2 IP |
| csharp-streamer.exe: [VT-1] MD5 351ba5a029f2671ddbc62bbb35588612 SHA-1 e5f1d22ad78ba2d0c5bbd0afae162837368ebcb4 SHA-256 ad5c06b52b468711f4f1ce1bf6957506b805b07e52c9be331035536672505160 csharp-streamer.exe: [VT-2] MD5 c00afc74e9424d9848fd8359a73415d3 SHA-1 2a76c44b8f5c2780a7245051d2d51e1592ec7a9f SHA-256 18458972b8917f358215ac7172aae62bc4438281614779dc264acc1c88629988 csharp-streamer.exe: [VT-3] MD5 5dd7bdf63e81cc08c75b6b54d581b48d SHA-1 a13f9e9372ce4efaa6a0e2844347897818dc2ebb SHA-256 58939d19a56dd6da9947e72360ed50704475c5f0aa350f5ccce3bbc4c9a0e6c5 csharp-streamer.exe: [VT-4] MD5 51f44e3c6ea8b85b6abbe7ff466c480e SHA-1 d5a448d91f0e73d17f28b4a35979f013d0215be5 SHA-256 3066e57cfadd3d127aa951562d6c1f50d97a9a0f2bdfbe39e83dc71971811384 csharp-streamer.exe: [VT-5] MD5 77d3f27aefa5424ca737dd4491b9bdf6 SHA-1 85524d6166471354547dccf8ca8d03210b34a037 SHA-256 80702e892a2f99da35e8a5a36bb7a2789f3642020c87bc72d238841045d71e47 | 136.144.245.9 109.248.144.72 |